The term “zero trust” was first coined in 2009 by John Kindervag. It’s a “trust but verify” approach that is related to defense-in-depth strategies and the principle of least privilege. In traditional security approaches, trust was often placed on the network perimeter, assuming that once inside, users and devices were inherently trustworthy. However, the evolving threat landscape and the rise of insider threats have challenged this assumption. Zero trust strategies shift the focus from a perimeter-centric model to an identity-centric one.
This blog will outline some of the key ways identity ties into overall zero trust strategies. Join us on June 17th, when John Kindervag will be joining us to discuss these themes in more detail.
Zero Trust Initiatives Are On The Rise
Although zero trust has been the victim of overhyped marketing, security leaders are now creating and implementing zero trust initiatives in earnest. According to Okta’s The State of Zero Trust Security 2022, 55% of respondents said they have a defined zero trust initiative underway. Gartner predicts that by the end of 2023, 60% of organizations will adopt a Zero Trust security model instead of virtual private networks.
However, the role of identity still trips people up. As I will explain, even developing a user inventory proves elusive.
Last month, the National Security Agency released a paper (Advancing Zero Trust Maturity Throughout the User Pillar) to discuss the role of identity in zero trust.
Let’s dig into why identity is a fundamental pillar of any zero trust strategy.
The Role of Identity in Zero Trust Strategy
Identity is a critical pillar of a zero trust strategy due to its inherent role in establishing trust and ensuring secure access to resources.
By incorporating identity as a foundational element, organizations can validate and verify the authenticity of users, devices, and applications at every access request. This approach rejects blind trust and enforces rigorous verification and continuous authentication, regardless of the user's location or network connection. It emphasizes a "never trust, always verify" principle, wherein identity becomes the key determinant for granting or denying access to sensitive resources.
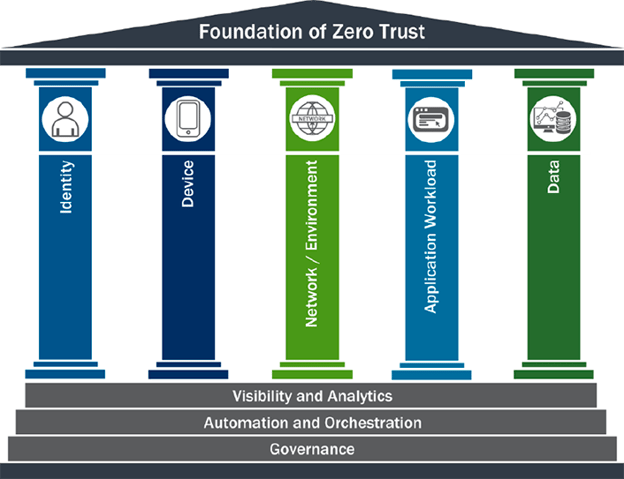
Integrating identity into a zero trust framework fosters a more dynamic and adaptive security posture. It enables organizations to continually assess the trustworthiness of users, devices, and applications based on contextual and historical factors such as user behavior, role, and location. This contextual awareness allows for real-time risk assessment and adaptive security controls, ensuring that access privileges can be adjusted dynamically based on the evolving threat landscape and user requirements.
Discovery
Zero Trust, at its core, is about protecting an organization’s data and assets. One model espoused by the DoD is Data, Applications, Assets, Services (DAAS) or, as John Kindervag describes it, “the protect surface”. Any effective zero trust strategy will have this at the center, and provide various controls to protect these.
Once this is determined, organizations need “ the ability to continuously authenticate, authorize, and monitor activity patterns to govern users’ access and privileges while protecting and securing all interactions.”
The first (and possibly hardest) element of identity is to develop a comprehensive user inventory. With machine identities, guest accounts, orphaned accounts, many security teams are not sure how many identities they manage, nor what access to data or applications they have.
Building an inventory, however, is wrought with challenges. As we recently outlined in Populating the Unpopulated: Challenges of Building a Comprehensive User Inventory , there are user lifecycle variations, difficulties merging users across platforms, the headache of managing machine identities, and the issue of administrative access across shadow IT.
Access Management: Mapping Users to Applications
Mapping users to applications is essential in zero trust strategies to establish granular access controls and mitigate security risks. By mapping users to applications, organizations can ensure that each user only has access to the specific applications and resources they require to perform their tasks, minimizing the attack surface.
If a user has inherited and developed excessive access, why not remove them? If a guest account has access to applications and hasn’t been active in a few months, why not delete it?
This approach enforces the principle of least privilege, reducing the potential impact of compromised credentials or insider threats. Mapping users to applications also enables organizations to monitor user activities, detect anomalies, and apply behavioral analytics to identify potential security breaches or unauthorized access attempts.
Ultimately, this mapping facilitates stronger access management and enhances the overall security posture of the organization.
From Multi Factor to Continuous Authentication
Zero trust strategies require multi-factor authentication and continuous authentication to bolster the security of identities and protect against unauthorized access. Multi-factor authentication adds an extra layer of verification by requiring users to provide multiple forms of authentication, such as a password and a unique code sent to their mobile device, making it more difficult for attackers to gain access using stolen credentials alone.
Continuous authentication goes a step further by continuously monitoring user behavior, device attributes, and contextual factors to assess the legitimacy of ongoing sessions. This dynamic approach helps detect and respond to suspicious activities in real-time, minimizing the risk of account takeover and maintaining a higher level of security throughout the user's session.
Mapping Users to Devices
Although “Devices” is a distinct pillar of zero trust, it’s important to map the users in your inventory to the devices.
Mapping users to devices is crucial in zero trust strategies to ensure secure access and mitigate potential risks. By mapping users to devices, organizations can establish device-specific policies and enforce access controls based on the trustworthiness and security posture of each device. This approach allows organizations to verify the identity and integrity of the device before granting access, reducing the likelihood of compromised or untrusted devices accessing sensitive resources.
Mapping users to devices also facilitates device-level monitoring, enabling organizations to detect anomalies, potential security breaches, or unauthorized access attempts. This mapping strengthens the overall security framework by incorporating device security as a key factor in the access decision-making process.
Oort’s Identity Security Platform
Security leaders use Oort’s Identity Security platform as an enabler of the identity pillar of zero trust. With Oort, you can easily:
- Create and maintain a user inventory across identity providers
- Track human and machine identities
- Map identities to applications, and identify over-permissioning
- Identify and delete inactive guest accounts
- Track access from unmanaged devices
To learn more about Oort for zero trust, reach out for a demonstration and register for our upcoming webinar.


