Identity Threat Detection and Response (ITDR) plays a crucial role in modern identity security strategies. To effectively detect and respond to identity-related security incidents, organizations must prioritize strong IAM foundations, implement proper collection techniques, and leverage key detections. In this blog, we will explore the importance of proper collection, key detections as KPIs, and the limitations of SIEM detections. Additionally, we will discuss the significance of incorporating non-traditional identity providers and the levels of maturity in operationalizing identity data.
Proper Collection: Cloud-based & Non-traditional IdPs
To effectively detect identity-based threats, organizations need to collect, store, and retain the relevant logs from various sources. This includes traditional on-premises Active Directory (AD) as well as cloud-based IAM solutions like Azure AD, Okta, and AWS. Additionally, monitoring non-traditional identity providers such as Google, Slack, Salesforce, and GitHub is essential, as attackers often exploit compromised non-traditional identities. By incorporating these sources, organizations can proactively identify potential threats and ensure compliance with security policies.

Key Detections: KPIs for Success
Monitoring the effectiveness of ITDR requires defining and tracking key performance indicators (KPIs). Some essential KPIs to consider include:
Retention Policy Validation: Ensure that identity sources are aggregated to a SIEM system with a validated retention policy. This KPI ensures that the collected data is stored appropriately and available for analysis.
Active Utilization of Data: Move beyond data collection and actively utilize the identity data by implementing rules and automation for analysis. This KPI signifies a shift towards proactive threat detection and response.
Identity Data Engineering: Achieve a comprehensive understanding and optimization of identity data through advanced data engineering techniques. This KPI indicates a high level of maturity in leveraging identity data for enhanced security insights.
Limitations of SIEM Detections
While SIEM systems have traditionally been the go-to choice for threat detection and response, they do have limitations. These include:
Ingestion Costs: SIEM systems often involve significant upfront costs for hardware, licensing, and maintenance. Alternatively, security data lakes offer more flexible cost structures, depending on specific requirements, but require investments in data ingestion and processing tools.
Storage Costs: SIEM systems have storage limitations and tend to store only a subset of relevant security data. In contrast, security data lakes can store large volumes of structured and unstructured data at a relatively lower cost.
Data Retention Period: SIEM systems typically have limited data retention periods, while security data lakes offer longer retention periods, facilitating forensic analysis and historical investigations.
Usability: SIEM systems can be complex and require specialized expertise, while security data lakes are often more user-friendly and accessible to both security analysts and data scientists.
If you're interested in learning more about the limitations of SIEM detections for identity security, our team wrote a blog earlier this year that goes into more detail.
Levels of Maturity
To measure the maturity of ITDR strategies, organizations can assess their progress against the following levels:
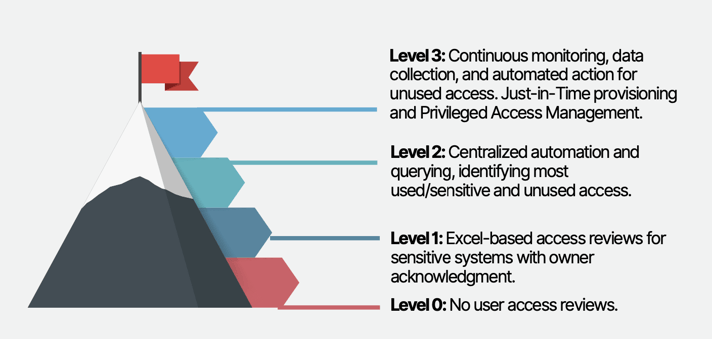
Level 0: No collection of identity logs or data.
Level 1: Identity sources aggregated to a SIEM system with validated retention policies.
Level 2: Active utilization of data through rule implementation and automation for analysis.
Level 3: Identity Data Engineering for comprehensive understanding and optimization of data.
Source: Building an Identity Security Program, Oort 2023
Conclusion
Proper detection for identity security is crucial for protecting sensitive information and mitigating risks. By focusing on proper collection, incorporating key detections as KPIs, considering the limitations of SIEM detections, and embracing non-traditional identity providers, organizations can enhance their ITDR strategies. By continuously maturing their approaches, organizations can effectively detect and respond to identity-related incidents, reducing the risk of data breaches and other security threats.
Oort recently published a guide with 11 key criteria for mastering identity security including establishing comprehensive detection. Download the full guide and contact us if you have any questions.
Oort’s Identity Security Platform
Oort is an identity-centric enterprise security platform. As a turnkey solution for Identity Threat Detection and Response (ITDR), Oort is providing immediate value to security teams by working with existing sources of identity to enable comprehensive identity attack surface management in minutes. Led by a team with decades of domain expertise across identity, networking, and security, Oort is backed by venture capital investors including Energy Impact Partners, .406 Ventures, Bain Capital Ventures, Cisco Investments and others. Market-leading technology companies, like Collibra and Avid Technology, rely on Oort to provide full visibility into their identity populations.
To get a free identity security health assessment, request a demo.



