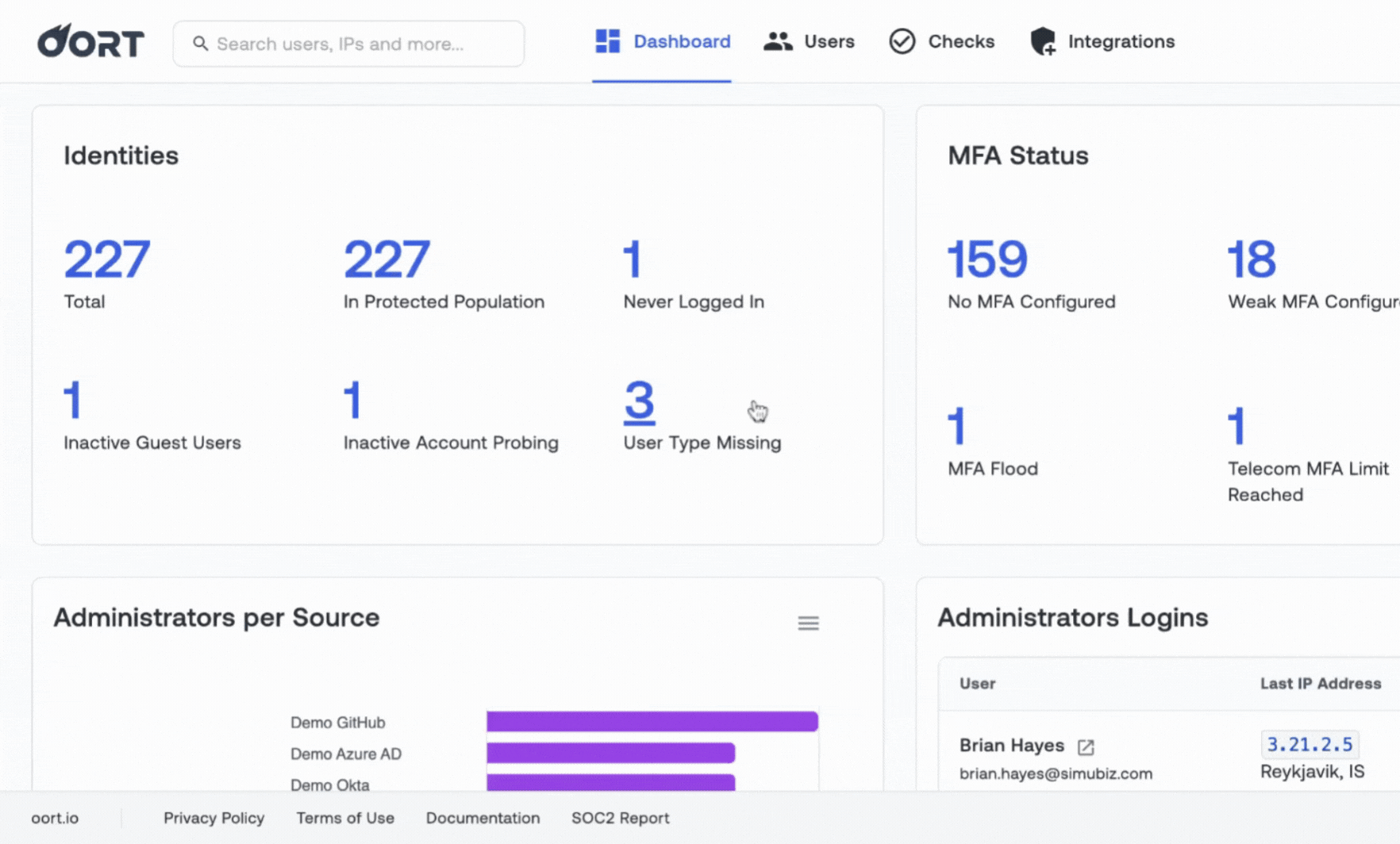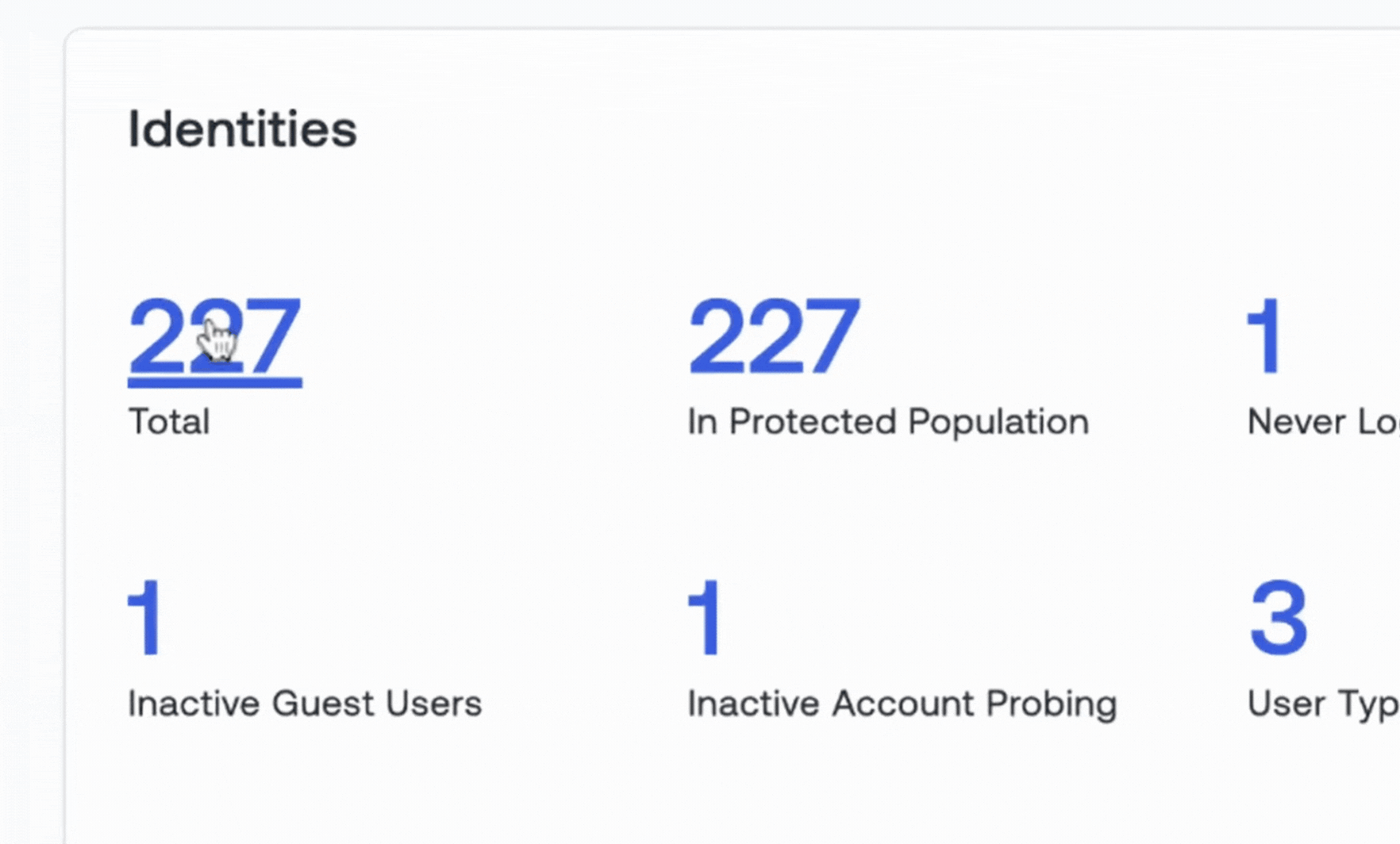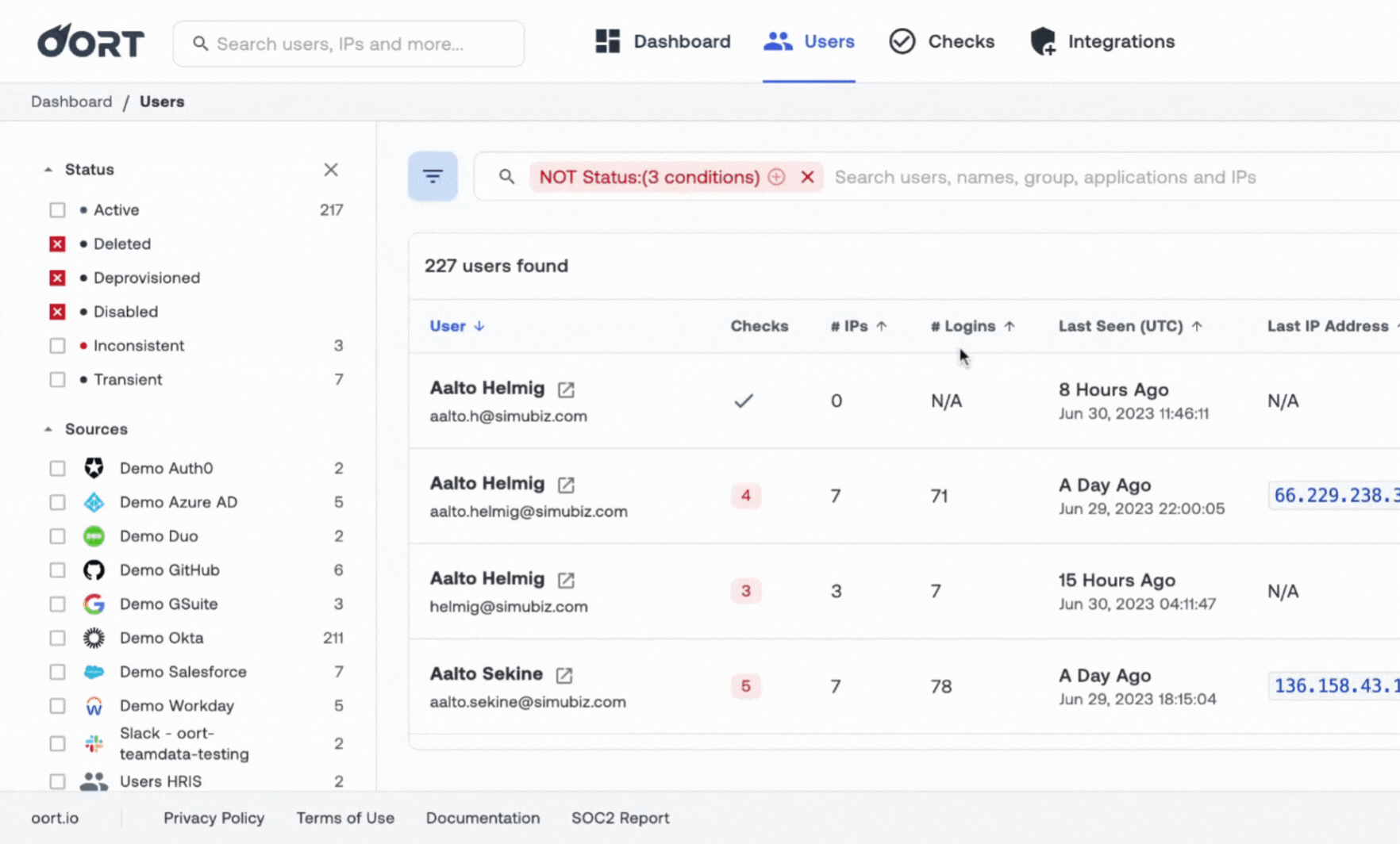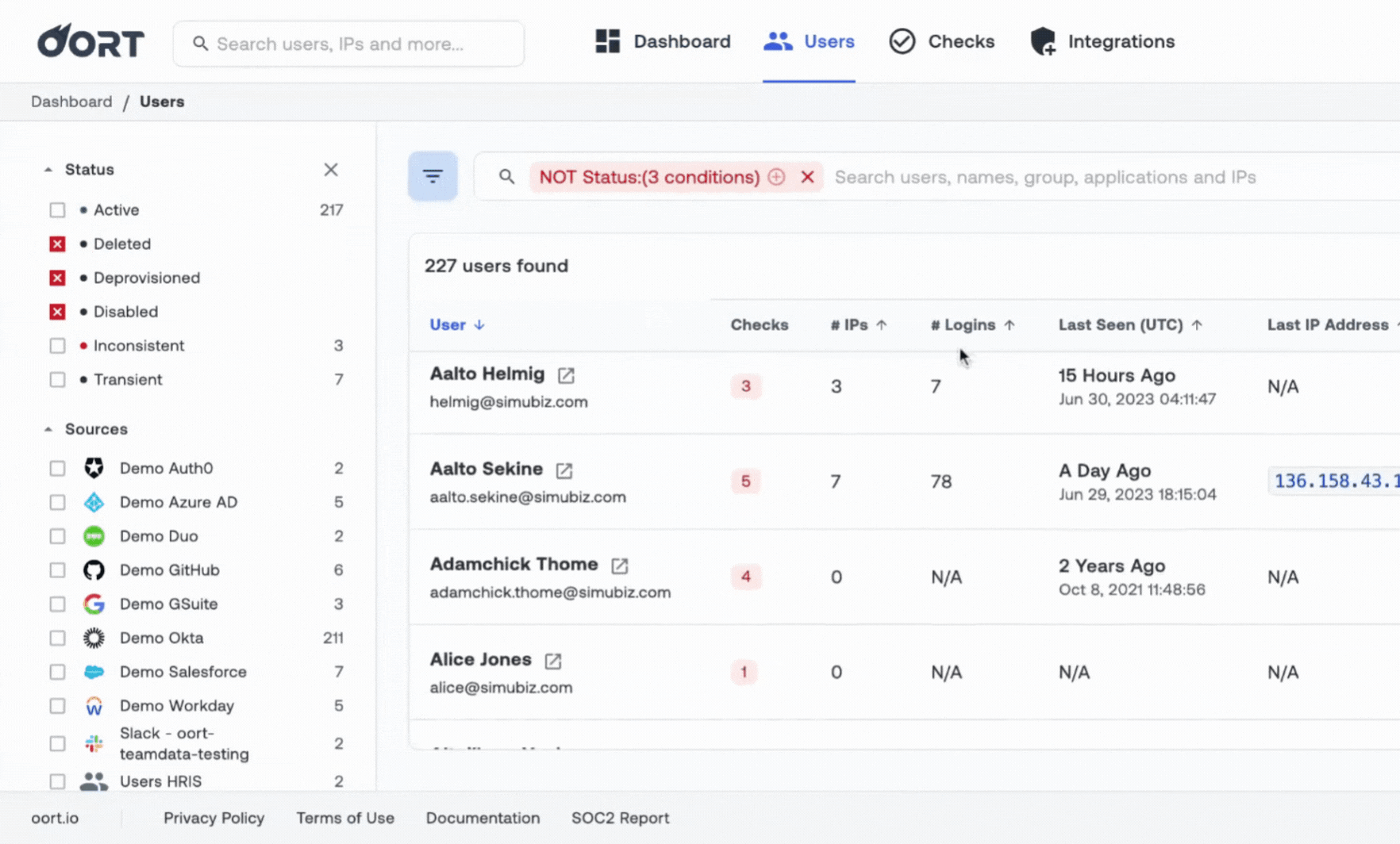
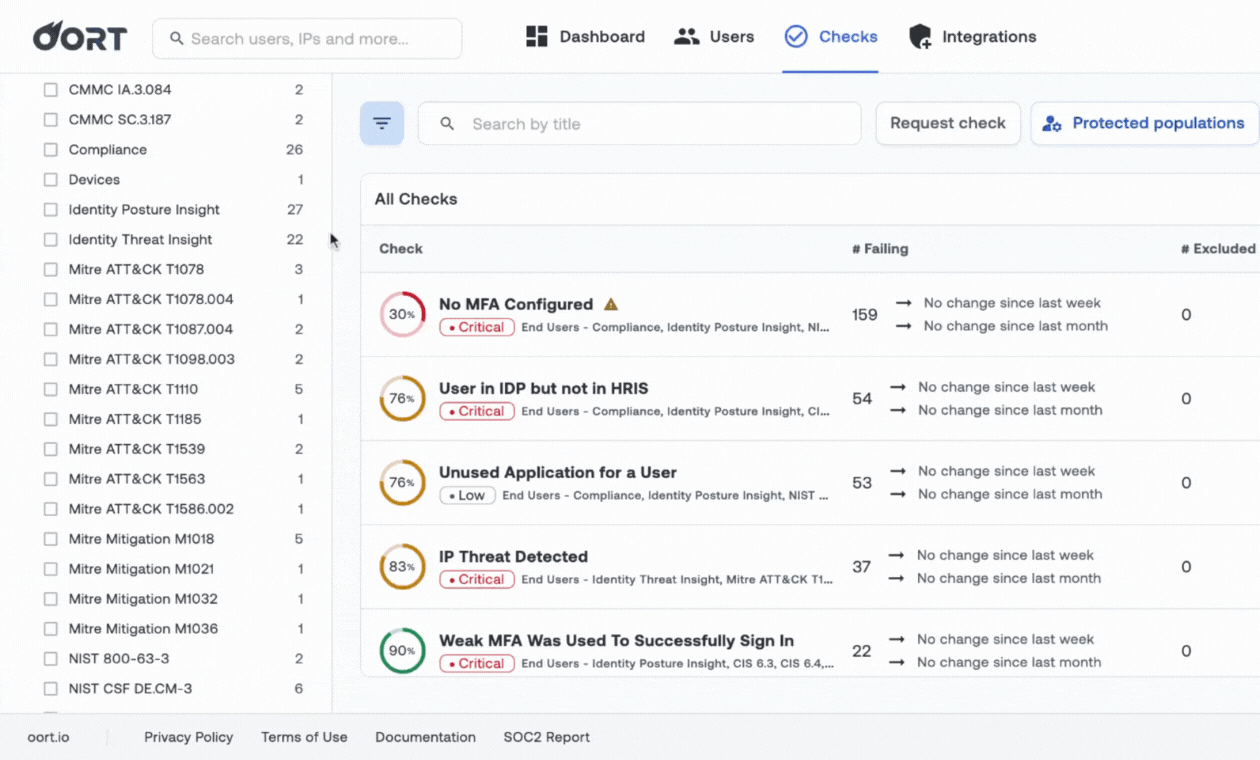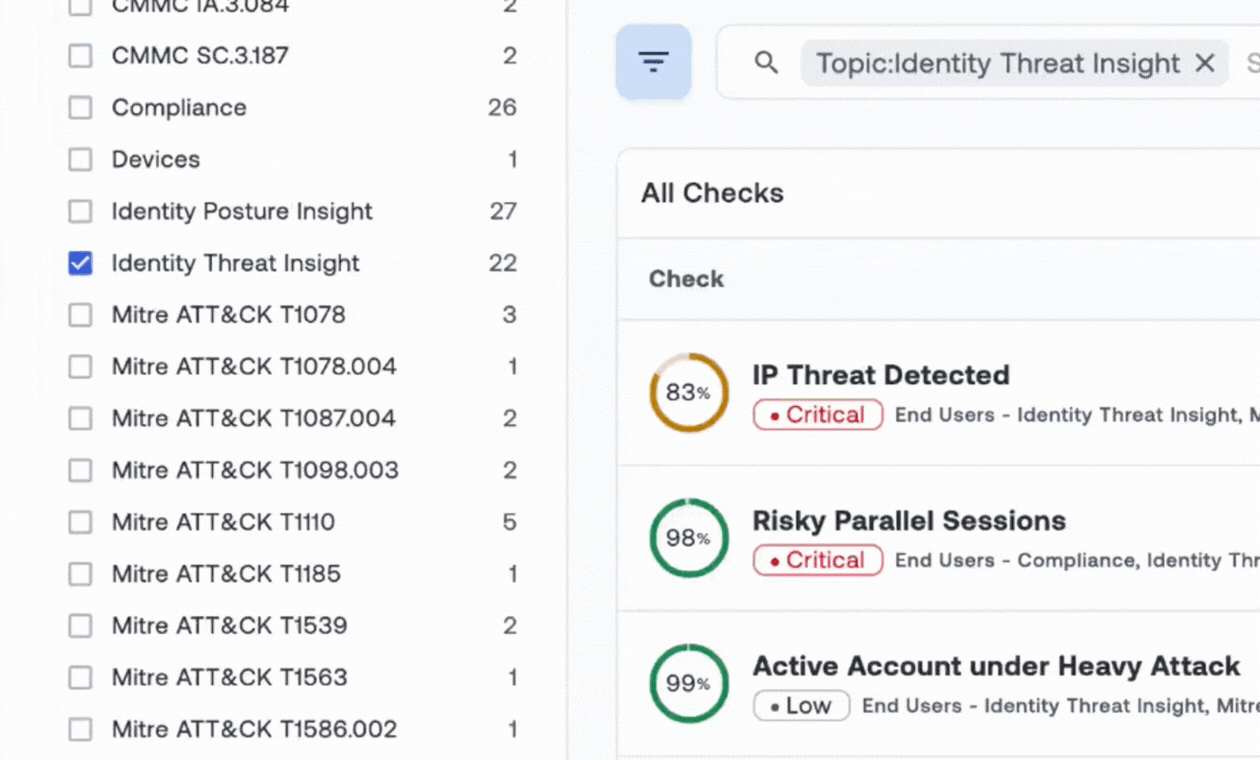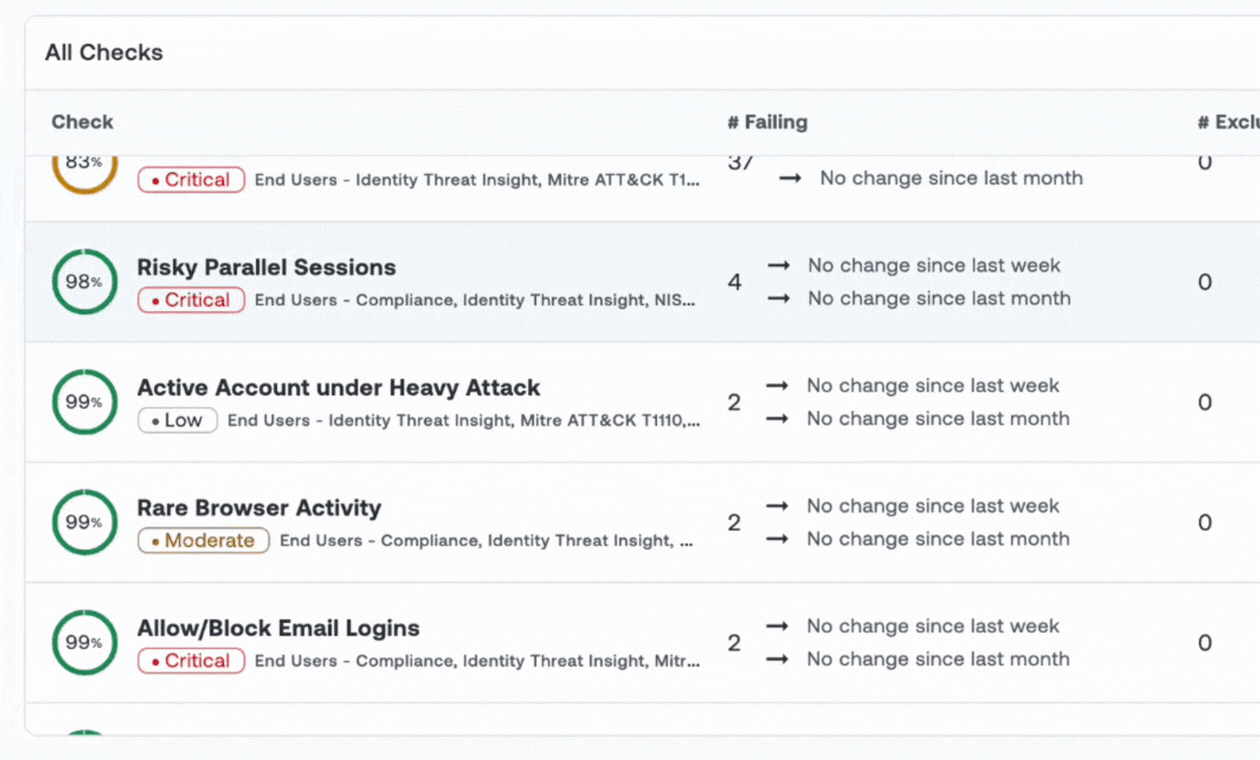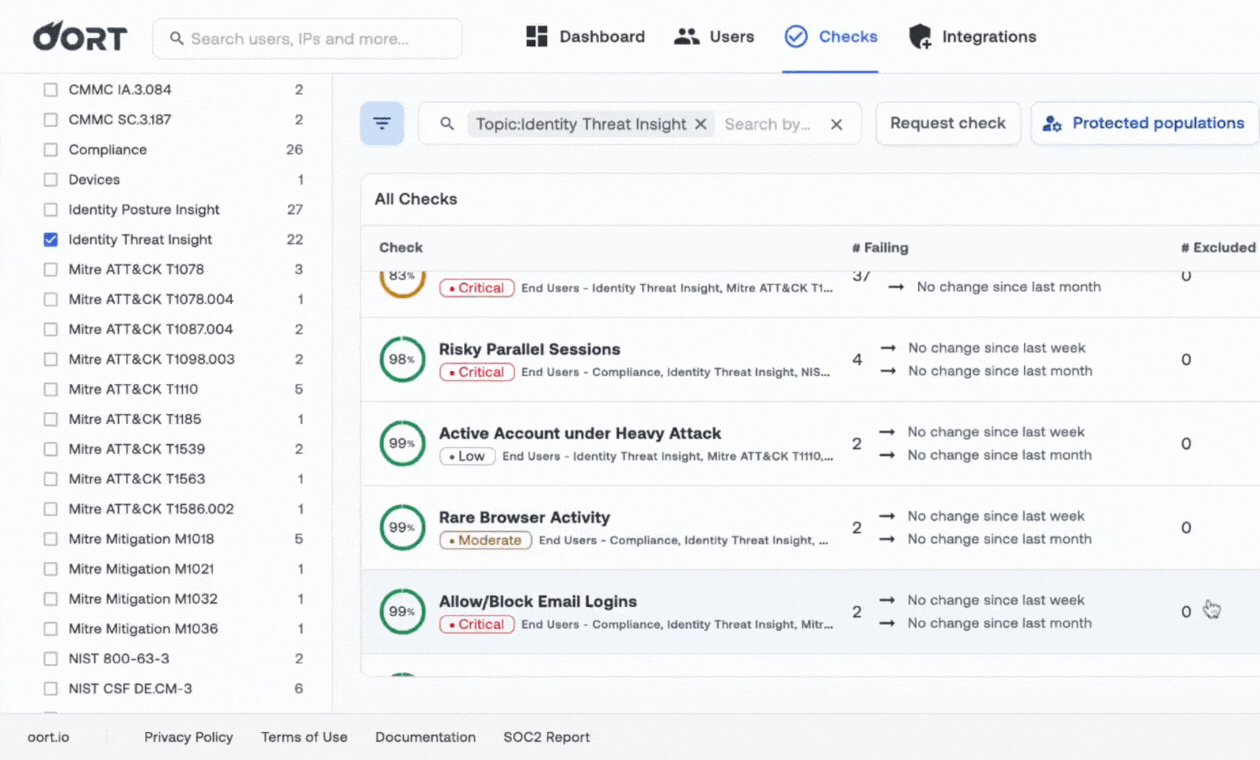
Build Your Identity Security Program - a Blueprint
Know you need to tackle identity security, but don't know where to start? Oort worked with dozens of practitioners to build this comprehensive guide for mapping where you are today across 11 key capabilities, guidance on how to build the right team, and KPIs to meaure progress.




.png)
.png)








