In today's digital landscape, managing multiple usernames and passwords across various systems can be a daunting task. Single sign-on (SSO) systems offer a solution by allowing users to authenticate once and gain access to multiple applications or systems seamlessly. In this blog, we will explore the purpose behind the invention of SSO, its potential vulnerabilities as a single point of failure, the importance of managing session length via SSO systems, and the levels of maturity securing your SSO deployment. Additionally, we will discuss key performance indicators (KPIs) to consider when evaluating the effectiveness of SSO implementations.
Why SSO was Invented
The primary motivation behind the invention of SSO was to address the challenges of credential hygiene. SSO allows users to authenticate once, eliminating the need to remember multiple usernames and passwords for different applications. This not only simplifies the login process but also improves productivity by reducing the time and effort required to access various systems. SSO mitigates the risk of password-based attacks, such as credential stuffing, by reducing the number of passwords that users need to manage.
SSO as a Single Point of Failure
While SSO offers convenience and security benefits, it can also become a single point of failure if not properly monitored. If an attacker gains unauthorized access to an SSO system, they could potentially gain access to multiple applications and systems linked to it. Therefore, it is crucial to implement robust monitoring and event tracking mechanisms to detect and respond to any suspicious activities. Treating SSO as a firewall can help organizations recognize its importance and take appropriate security measures.
Session Length Requirements
The duration of SSO sessions is an essential consideration for balancing convenience and security. Longer session lengths provide more convenience to users, as they don't have to repeatedly authenticate. However, longer sessions also increase the window of opportunity for potential attackers to exploit compromised sessions. Striking the right balance between session length and security is crucial, and it may vary depending on the sensitivity of the applications and the risk appetite of the organization.
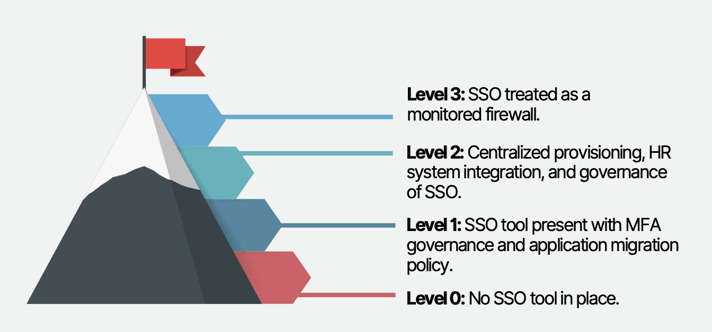
Levels of Maturity in Securing SSO Deployments
Level 0: No SSO tool in place.
Level 1: Implementing an SSO tool with multifactor authentication (MFA) governance and an application migration policy to gradually move applications to SSO.
Level 2: Centralized provisioning, integration with HR systems for seamless onboarding and deprovisioning, and governance of SSO to ensure proper access controls.
Level 3: Treating SSO as a monitored firewall by implementing robust event monitoring, tracking, and response mechanisms to detect and mitigate any potential security incidents.
 Source: Building an Identity Security Program, Oort 2023
Source: Building an Identity Security Program, Oort 2023
KPIs to Consider
To measure the effectiveness of SSO deployments, organizations can consider the following key performance indicators:
Percentage of business applications using SSO: This metric indicates the extent to which SSO has been implemented across the organization, providing insights into the overall coverage and adoption rate.
Percentage of password complexity rate: Evaluating the complexity rate of passwords associated with SSO accounts helps assess the strength of user authentication. Higher complexity rates indicate better password security practices.
Percentage of accounts with password updates in the last 30 days: Tracking the frequency of password updates provides insights into the level of proactive password management and helps identify potential security gaps.
Conclusion
Implementing SSO systems can significantly enhance identity security and simplify user access to multiple applications. However, organizations must be mindful of potential vulnerabilities and treat SSO as a critical component that requires proper monitoring and security measures. By striving for maturity in securing SSO deployments and tracking relevant KPIs, organizations can strengthen their identity security program and protect sensitive information from unauthorized access.
If you are worried about your SSO system being a single point of failure, you are not alone. SSO is a key technology for IAM and identity security, but it requires proper monitoring to prevent breaches. We have built a comprehensive blueprint that begins with understanding your current maturity across 11 factors and provides recommendations on how you improve your defenses and move up the maturity curve. Download the full guide and contact us if you have any questions.
Oort’s Identity Security Platform
Oort is an identity-centric enterprise security platform. As a turnkey solution for Identity Threat Detection and Response (ITDR), Oort is providing immediate value to security teams by working with existing sources of identity to enable comprehensive identity attack surface management in minutes. Led by a team with decades of domain expertise across identity, networking, and security, Oort is backed by venture capital investors including Energy Impact Partners, .406 Ventures, Bain Capital Ventures, Cisco Investments and others. Market-leading technology companies, like Collibra and Avid Technology, rely on Oort to provide full visibility into their identity populations.
To get a free identity security health assessment, request a demo.



