Identity plays a vital role in modern security frameworks and is a fundamental component of any robust zero trust strategy. To ensure the integrity and protection of sensitive data and resources, organizations must implement effective identity controls. In this blog, we will explore how identity controls align with the CIS Critical Security Controls (CIS Controls) and the NIST Cybersecurity Framework, specifically focusing on six key areas: identity inventory, multi-factor authentication (MFA), access control, IAM hygiene, log collection, and session management.
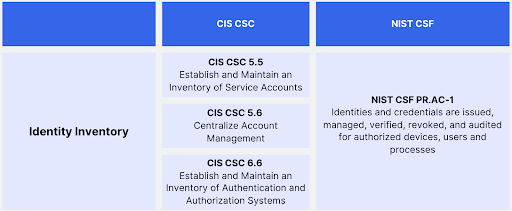
Developing an Identity Inventory
One of the foundational steps in establishing a secure environment is developing a comprehensive identity inventory. This involves maintaining an inventory of service accounts, authentication and authorization systems, and centralizing account management. The CIS CSC 5.5, CIS CSC 6.6, and CIS CSC 5.6 address these requirements, while the NIST CSF's PR.AC-1 emphasizes issuing, managing, verifying, revoking, and auditing identities and credentials for authorized devices, users, and processes.
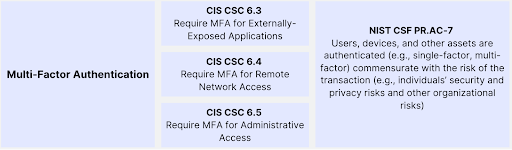
Requiring Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of verification. The CIS CSC 6.3, CIS CSC 6.4, and CIS CSC 6.5 highlight the importance of implementing MFA for externally-exposed applications, remote network access, and administrative access. Similarly, the NIST CSF's PR.AC-7 emphasizes that authentication methods should be commensurate with the risk of the transaction, considering individuals' security and privacy risks as well as other organizational risks.
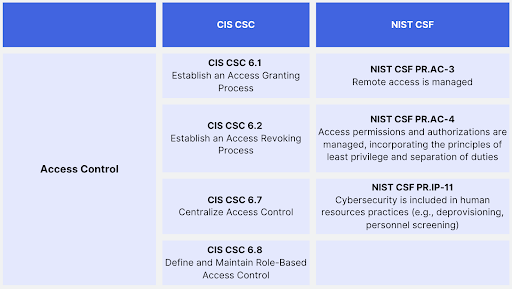
Enabling Access Controls
Access controls are essential for managing user privileges and preventing unauthorized access. The CIS CSC 6.1 and CIS CSC 6.2 emphasize establishing access granting and revoking processes, while CIS CSC 6.7 highlights the centralization of access control. Additionally, CIS CSC 6.8 underlines the importance of defining and maintaining role-based access control. The NIST CSF complements these controls with PR.AC-3, which focuses on managing remote access, and PR.AC-4, which emphasizes the principles of least privilege and separation of duties in access permissions and authorizations. PR.IP-11 further highlights the inclusion of cybersecurity in human resources practices, such as deprovisioning and personnel screening.
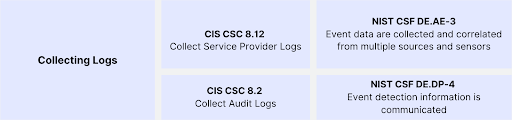
Collecting Logs from Identity Sources
Collecting and analyzing logs from identity sources is crucial for detecting and responding to security incidents. The CIS CSC 8.12 and CIS CSC 8.2 address the need to collect service provider logs and audit logs, respectively. Similarly, the NIST CSF's DE.AE-3 emphasizes the collection and correlation of event data from multiple sources and sensors, while DE.DP-4 emphasizes the importance of communicating event detection information.
IAM Hygiene
IAM (Identity and Access Management) hygiene focuses on maintaining the integrity of user accounts and access privileges. The CIS CSC 5.3 emphasizes the need to disable dormant accounts, while CIS CSC 4.7 highlights managing default accounts on enterprise assets and software. These controls help mitigate the risk of unauthorized access and potential misuse of dormant or default accounts.
Managing Sessions
Effective session management is crucial for securing enterprise assets. CIS CSC 4.3 stresses the importance of configuring automatic session locking on enterprise assets, preventing unauthorized access in case of user inactivity. By implementing this control, organizations can minimize the risk of unauthorized access to sensitive information.
Conclusion
Identity controls play a pivotal role in building a robust security framework and implementing a zero trust strategy. By mapping these controls to the CIS CSC and NIST CSF security frameworks, organizations can ensure a comprehensive approach to identity management.
From developing an identity inventory and requiring multi-factor authentication to enabling access controls, collecting logs, maintaining IAM hygiene, and managing sessions, organizations can enhance their overall security posture and mitigate the risk of data breaches and unauthorized access.
Embracing these controls is critical ensuring identity is a key pillar of your overall security program. To read more about building an identity security program, download Oort’s Blueprint for Building an Identity Security Program.
Oort’s Identity Security Platform
Oort is an identity-centric enterprise security platform. As a turnkey solution for Identity Threat Detection and Response (ITDR), Oort is providing immediate value to security teams by working with existing sources of identity to enable comprehensive identity attack surface management in minutes. Led by a team with decades of domain expertise across identity, networking, and security, Oort is backed by venture capital investors including Energy Impact Partners, .406 Ventures, Bain Capital Ventures, Cisco Investments and others. Market-leading technology companies, like Collibra and Avid Technology, rely on Oort to provide full visibility into their identity populations.
To get a free identity security health assessment, request a demo.



