Are you tired of relying on SIEMs and still failing to generate valuable insights from your data? Concerned about the increasing costs of your SIEM? Are you looking to understand how to get meaningful insights from identity sources?
You're not alone.
In this blog, we'll explain why modern CISOs are building their security program on a security data lake and the role that identity and access management (IAM) can play.
Scale Venture Partners’ (SVP) Cybersecurity Perspectives 2023 report
Three Reasons Why A Security Data Lake Suits the Modern CISO
If the term is new to you, a security data lake is a centralized and scalable repository that stores and manages vast amounts of security-related data from various sources within an organization. With this data, organizations can perform advanced security analytics, threat detection, and incident response in ways that would be extremely painful with a SIEM. In the words of Snowflake, a security data lake “improves visibility across the entire operation, providing a centralized solution for managing security.”
While SIEM systems have been a traditional choice for threat detection and response, security data lakes are gaining popularity due to:
- Their ability to store and analyze large amounts of data. A security data lake offers the advantage of storing extensive volumes of data, including both structured and unstructured data, at a relatively lower cost. This scalability and flexibility make the security data lake an appealing choice for efficiently managing and analyzing diverse data sources, empowering comprehensive security operations. Many companies have many different sources of identity tools, and so the ability to store all of this can become burdensome.
- Support flexible data retention periods. Legacy SIEM systems often face storage limitations, leading to limited data retention, typically measured in days to weeks. On the other hand, a security data lake offers the advantage of extended data retention, ranging from months to years. This prolonged retention capability is particularly valuable for forensic analysis and investigating users. Making effective decisions often requires access to contextual data that extends beyond the standard 30-day timeframe. By opting for a security data lake, security leaders can ensure the availability of historical data for comprehensive investigations and informed decision-making of identity threats.
- Provide advanced analytics capabilities. Legacy SIEM systems can be intricate, demanding substantial know-how to configure, operate, and maintain effectively. Conversely, a security data lake offers a more user-friendly approach, making it accessible to less technical users. This accessibility empowers a broader range of security analysts and data scientists to leverage advanced analytics and machine learning capabilities in detecting and responding to identity threats.
For these reasons, CISOs are increasingly moving away from the idea that the SIEM is the place to store all of your security data.
Building an Ecosystem That Makes Sense for You
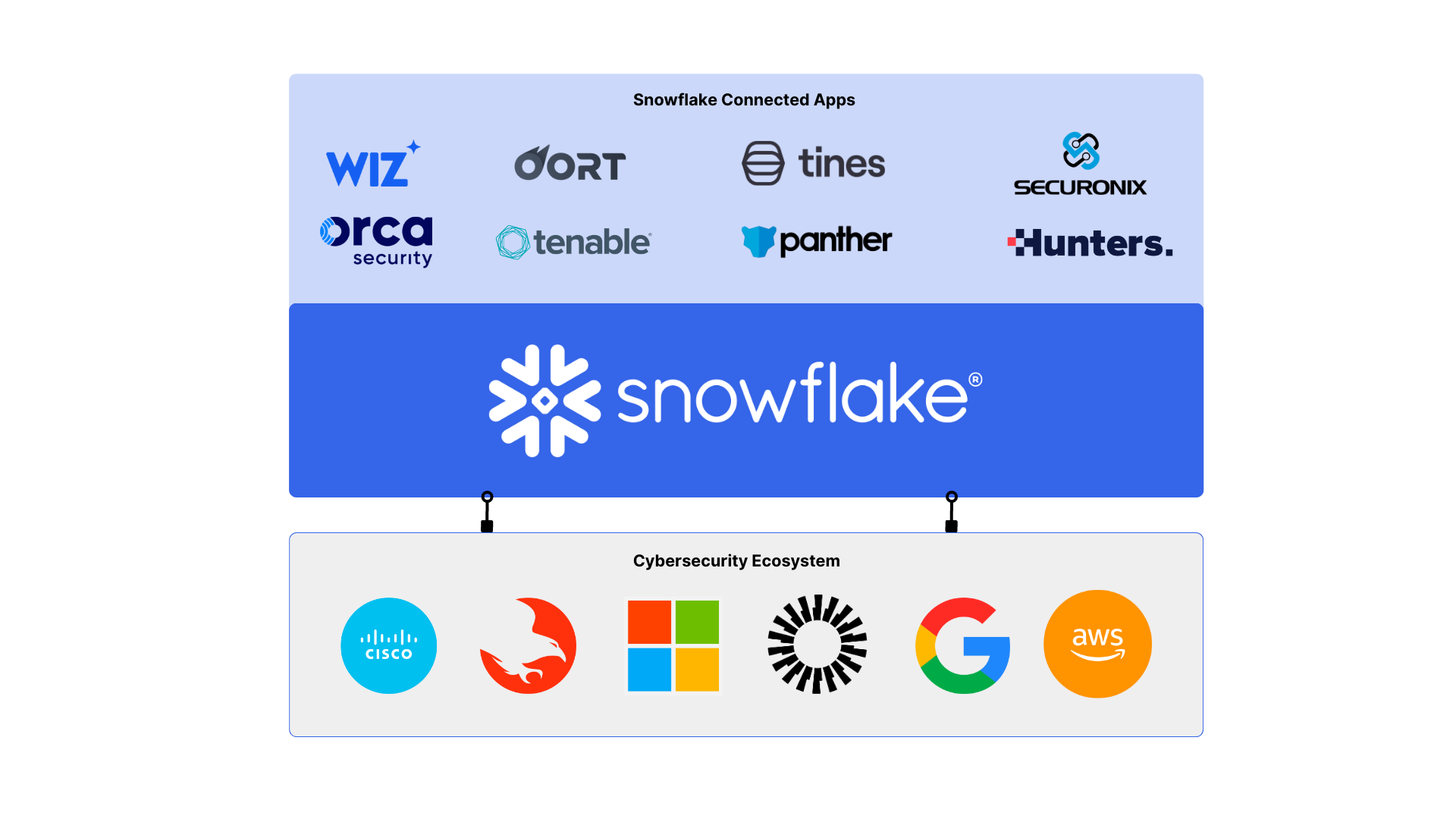
By ingesting and processing data in a security data lake, organizations can make sense of the information, apply data enrichment techniques, and perform advanced analytics. One of the superpowers of Snowflake is its rich ecosystem of pre-built integrations that make this incredibly easy.
If you want a vulnerability management solution integrated, try a solution like Dassana.
Looking to get insights on cloud security? Try Lacework or Orca. Looking for email security? Try Material Security. Looking for threat intelligence providers? Try IPInfo.
There are even integrations with ticketing platforms like ServiceNow and automation platforms like Tines.
Bringing these together helps you to save costs and make use of all the data that may otherwise live in silos. This enables proactive threat detection and facilitates deeper insights into security events.
Once the data has been refined and enriched in the security data lake, it can then be selectively fed into a SIEM. This targeted approach ensures that the SIEM receives relevant, contextualized data, optimizing its efficiency and reducing false positives. The SIEM can then focus on real-time event correlation and response orchestration, leveraging the processed data from the security data lake. Luckily, there are some excellent tools built on Snowflake’s data cloud that can do this; Hunters, Securonix, and Panther are the exemplars.
IAM Analytics for your Security Program
At the same time as modernizing their security program, CISOs are grappling to understand how to gain visibility of their identity providers. Many organizations today have a multitude of identity tools in their infrastructure, enabling various user access and authentication mechanisms. According to research from Dimensional Research, approximately 50% of all organizations use 25+ systems to manage identity and access rights.
Oort already provides identity analytics on top of Snowflake, which means we can provide incredible insights on vast datasets for our customers. With a Connected App in Snowflake, organizations can overcome this challenge while simultaneously pursuing a security data lake strategy.
With Oort and Snowflake, security leaders can confidently rely on cutting-edge analytics, enriched data, and the continuous evolution of our detection capabilities. Together, we strive to provide comprehensive and up-to-date security solutions tailored to address the dynamic challenges of identity threats.
Learn More about Oort and Snowflake
If your interest is peaked and you want to learn a bit more detail about Oort, read about how Oort uses Snowflake Marketplace to streamline data collaboration with IP Info data and enable contextualized security insights.
You can also watch a recording of our joint webinar with Snowflake, where you can hear from the amazing team at IPInfo, who we partner with to get the best IP data around.


