Summary
Yesterday, the FBI seized Genesis Market, an Automated Vending Cart (AVC) that sold the cookie data of consumers and corporate accounts. In doing so, Genesis enabled criminals to bypass existing fingerprinting controls and hijack user sessions.
While the takedown is welcome news, targeting identities with session hijacking is here to stay.
The Rise and Fall of the Genesis Market
The Genesis Market launched their Alpha product in late 2017 and rapidly grew in popularity. Its emergence was one of the most exciting developments in the cybercriminal underworld. According to KrebsOnSecurity, the store had more than 450,000 bots for sale last month.
‘Operation Cookie Monster’ was a joint effort by law enforcement and private companies from 17 different countries. The takedown is alleged to have coincided with a large number of arrests.
The FBI takedown notice for Genesis Market
The takedown is a great win; after more than five years in business, Genesis Market has significantly impacted the cybercriminal landscape. If you’re interested to learn more about the history of the site, check out the following:
- Genesis Botnet: The Market Claiming to Sell Bots That Bypass Fingerprinting Controls
- Genesis Market, one of world’s largest platforms for cyber fraud, seized by police
- How Anti-Detect Browsers Spoof Real Users
How did this all work, and why were these authentication cookies appealing to fraudsters?
Cookies and Session Hijacking
Session hijacking is an attack where an attacker takes over an active session between a user and a website or application. The attacker can then use the session to access the user's sensitive information or perform unauthorized actions.
Cookies are often used to hijack sessions because they are used to store session IDs, which are unique identifiers that allow servers to associate a user's requests with their ongoing session.
Stealing session IDs can often mean attackers do not have to log in and sometimes even bypass MFA controls.
Techniques for Session Hijacking
Simply because Genesis Market was seized, it does not mean session hijacking will fall off.
Plenty of tools and techniques make this an appealing option for attackers. One such tool is Evilginx. This phishing tool acts like an Attacker in The Middle (AiTM), sitting between the server and the client to steal session IDs. By doing so, Evilginx can bypass weak forms of two-factor authentication.
- The attacker sets up a convincing phishing site and sends it to target
- The victim clicks on the link and enters the password and one-time password (OTP)
- Evilginx captures credentials and session cookies
- The attacker uses credentials and cookers to authenticate into the real domain
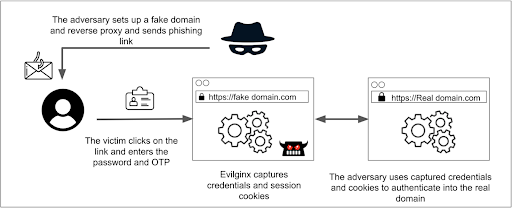
How Evilginx works. Source: okta.com
To understand the prevalence of session hijacking, our State of Identity Security report analyzed the number of suspicious Attacker in the Middle (AiTM) attacks. AiTM attacks might look like when a user opens multiple sessions with the same website or application but come from different IP addresses or devices. This can be an indicator of session hijacking because it can allow an attacker to take over one of the sessions while the user is still active on the other. The attacker can then use the hijacked session to access sensitive information or perform unauthorized actions. The report found that 46% of organizations saw suspicious AiTM activity in 2022.
 Detecting risky parallel sessions in Oort
Detecting risky parallel sessions in Oort
Poor IAM Hygiene Facilitates Session Hijacking
As with many identity threats, weaknesses in IAM hygiene present attackers with opportunities.
One control that we often see is overlooked is the length of sessions. Excessively long sessions can enable terminated users to continue having access to their inbox after termination or even for regular users to evade enforcement when you roll out new MFA policies until they need to authenticate. They also help session hijacking: the longer a session, the less likely an attacker is to be kicked off.
Okta recommends total lifetime sessions are at most one working day.
While there may be some instances to break that, any sessions that exceed seven days (168 hours) can make it easier to hijack sessions. Our analysis shows that, while most sessions are limited to the working day, the average company has 16.83 sessions every month that exceed seven days.

Protecting Against Session Hijacking
Organizations should ensure that they have robust session management practices in place to prevent parallel sessions and protect against session hijacking. This can include implementing timeout settings, invalidating sessions after a set period of inactivity, and using secure authentication methods, such as phishing-resistant multi-factor authentication. By taking these measures, organizations can reduce the risk of session hijacking and protect their sensitive information from unauthorized access.
Organizations are increasingly establishing identity security programs that can monitor for threats like session hijacking and fix weaknesses associated with identities. Oort is helping organizations achieve this.
Curious to learn more? Reach out to our team to learn how we can help.



