Guest accounts in Azure AD are identities belonging to external users invited to collaborate with the organization. Inviting guest accounts into your organization can be as simple as sending a link to a document or messaging an external email address on Teams.
While guest accounts are essential for collaboration and access management in Office 365, they are also a central risk for data loss and leaks. For example, a common practice for employees expecting to be terminated is to share information with private Gmail or Microsoft cloud accounts.
While policies can be set in place, no industry standard or guidelines for managing guest accounts exists.
Put a Policy in Place
Like everything else, start with the right level of policy that might be governed by the regulation of your industry. Before implementing a highly restrictive policy, be aware that people will find other ways to share content. These “creative” methods might not be as easy to regulate as guest accounts. Instead, start with putting a process in place for how an invite process works, who can be invited, for how long, and to what types of content. Set an expiration time for invites and link them to your current access review process. This ensures that guest accounts are only used for as long as needed and not left open indefinitely.
Manage Attribution
It's essential to keep a clear link to who invited the user and set the policy to include personal invites and what happens when the person who invited them leaves. This helps to ensure that guest accounts are only used by people who have a legitimate reason to access them. In addition, it's important to have a bi-directional view of who a user invited and who owns the invite. This ensures that a person inside the organization is responsible for those actions.
Review and Delete
Regular deletion of guest accounts is crucial to reduce data loss and leaks. Organizations should regularly review their guest accounts and delete those that are no longer needed. In addition, unaccepted invites or those in a limbo state should be deleted after one week. This helps to ensure that guest accounts are not left open and available to anyone who may have access to the link.
Set Up Multi-Factor Authentication
Setting up multi-factor authentication (MFA) for guest accounts ensures that the right person is accessing the right information and reduces the risk of identity theft. However, linking guest account MFA to the data accessed is important. You don't want external users accessing data that is internally regulated and governed via MFA. As a result, guest accounts should be granted access only to the data they need, and MFA should be enabled for that data.
Limit Guest Permissions
Organizations should limit the permissions of guest users to reduce the risk of unauthorized access to company data. Non-privileged users should not be allowed to register third-party applications. The "Restrict user ability to access groups features in the Access Panel" setting should be enabled to limit user access to AAD group features.
How Oort Helps
The Oort Identity Security platform helps security teams manage their guest accounts in Azure AD. It provides a simple understanding of the identity population, including inactive and active guest accounts. It also alerts organizations on inactivity, allowing them to regularly remove inactive accounts.
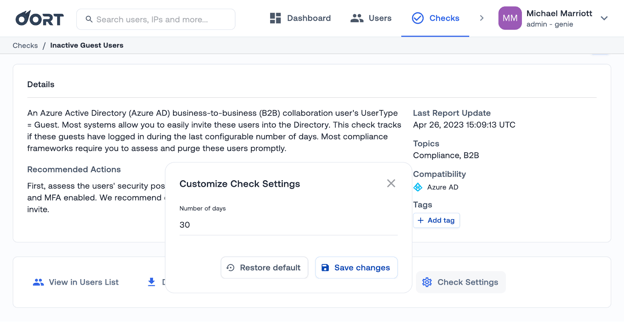
With Oort, organizations can create advanced filters to look for additional risks associated with guest accounts. For example:
- How many guest accounts have no MFA?
- How many guest accounts have no MFA AND have logged in from a new country?
These advanced filters make it easy to quickly see the risks posed by guest accounts
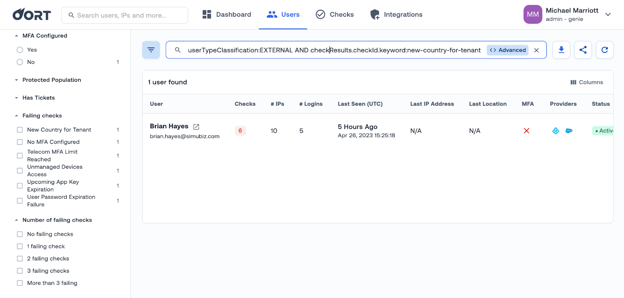
Easily remediate inactive guest accounts
Inactive guest accounts present a huge opportunity for attackers. If they take over these accounts, detecting or monitoring their activity becomes extremely hard. Therefore, why not delete inactive guest accounts once you have identified them? If the guest needs access once more, they can request it.
If this sounds appealing, you can benefit from Oort’s ability to delete the user in Azure AD with one button click. We’ve recently added this to our suite of remediation actions available within the User 360 profile.
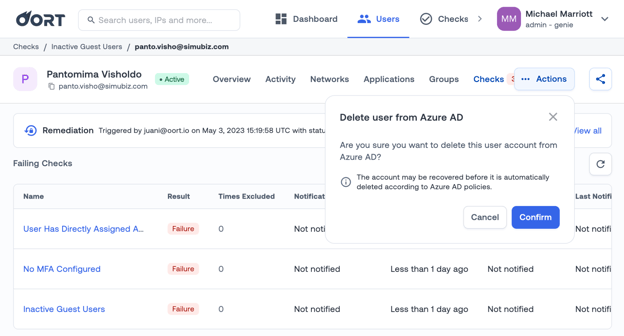
Don’t stick your head in the sand
Managing guest access can be hard, especially with no agreed standard. However, by creating a policy, understanding your identity population, and checking for weaknesses, you can help mitigate their risks.
Curious to learn more about how Oort helps? Schedule a demo!


