Cisco Identity Intelligence Webex Notification Integration
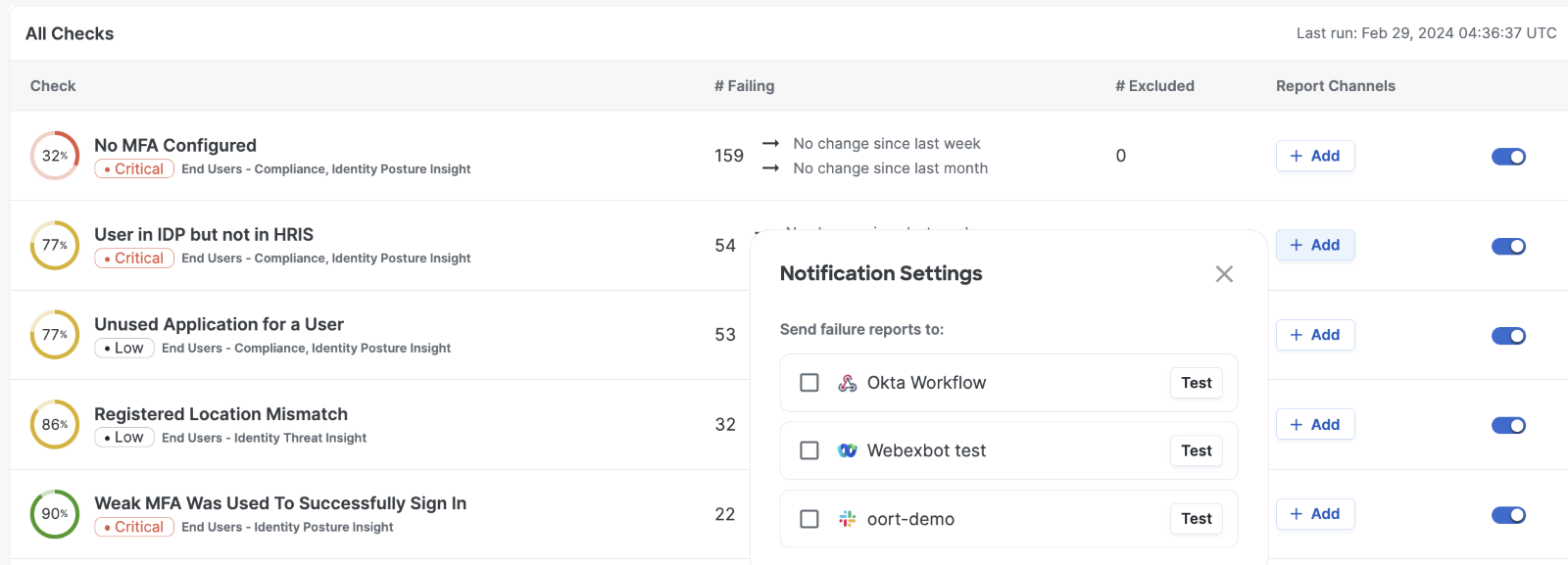
As you might be aware, we currently offer the Slack integration, allowing you to set up Slack as a notification target. We are thrilled to announce the release of the Webex notification integration, providing you with the ability to install our app in a Webex Workspace. With this integration, you’ll receive notifications for failed checks and data collections errors directly in your Webex Workspace.
This integration empowers you to configure notifications for checks that are important to you. With that, you’ll be promptly alerted when users fail specific checks, enabling you to investigate matters of significance to your operations.
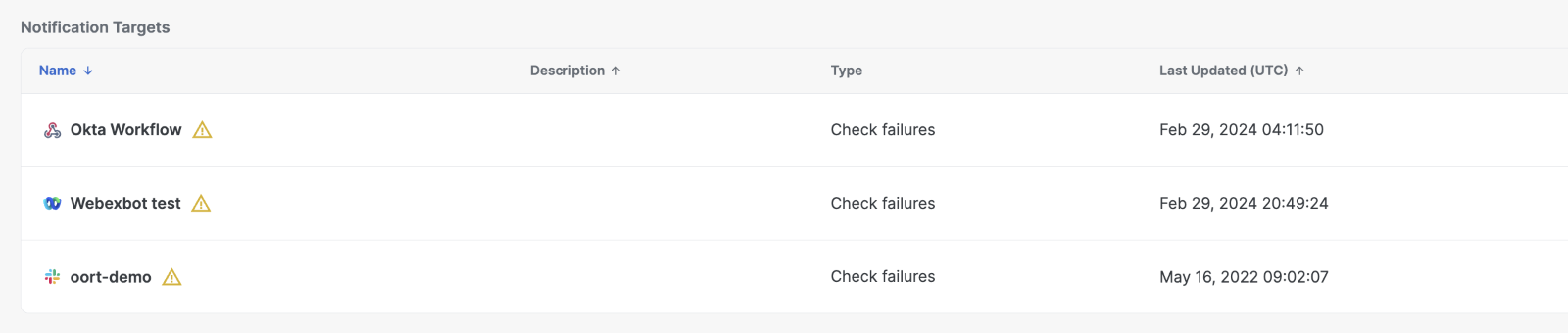
Once the integration is configured, you’ll find the bot listed under ‘Notifications Targets’ on the Integrations tab. Additionally, you’ll see the bot displayed as an option in ‘Notification Settings’ for your checks.
See our configuration guide for instructions on how to set up the Webex Notification Integration for al or individual checks.
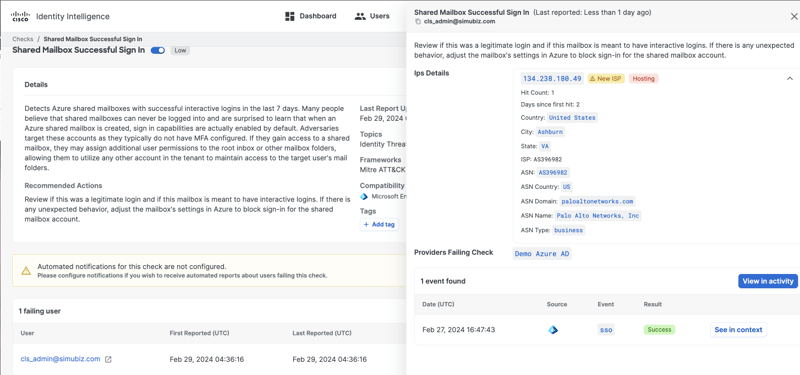
New Check: Shared Mailbox Successful Sign-in
In our previous release, we introduced the ‘Shared Mailbox Sign in Enabled’ check, which that identifies when a shared mailbox has the interactive sign-in feature enabled within Entra. In this release, we are introducing the ‘Shared Mailbox Successful Sign In’ check, which detects interactive logins within the last 7 days by default. Like many of our other checks, you can adjust the evaluation period ‘Check Settings’ to best fit your needs.
Having visibility into these interactive logins are key as shared mailboxes are often created with these sign-in capabilities by default with no Multi-Factor Authentication (MFA) configured. These accounts are often targeted by adversaries. If adversaries gain access, they could log directly into the mailbox and assign additional user permissions to other mailbox folders, including the root inbox. This could allow adversaries to utilize any other account within the tenant to maintain access to the target mailbox folders.
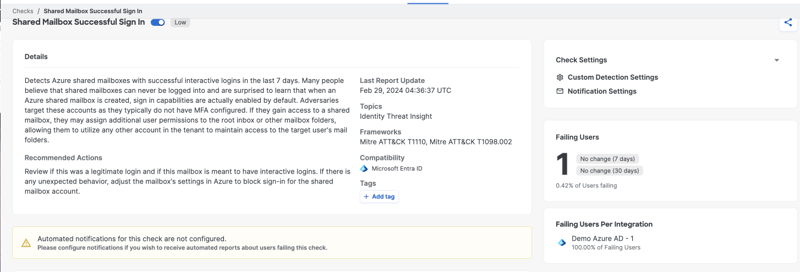
By clicking on the failing user, you will see the explainability drawer, which provides more context around the interactive login events. This enables you to further investigate the activity and determine whether it’s a legitimate login or if adjustments need to be made to the mailbox settings to block sign-ins.
Bug Fixes and Minor Improvements
- Add ‘Not Enabled’ to compliance filter. We added ‘Not Enabled’ to the check compliance filter. Allowing you to filter the checks by those that are not enabled.
- Display observations for resolved checks. You can now see the observations listed in a dropdown for resolved checks.
- Single date selection on activity view. For the activity view you, you can now select a single date. Allowing you to see the events for that day.
- Email and webhook on check settings. For Check direct message settings, you now have the ability to add email and webhook options.
- Copy user login button. Throughout the platform, you can now copy the user login for enhanced experience when navigating the platform during investigations.
- Allow deleting for ‘Never logged in’ check. For Azure external users that fail the ‘Never Logged in’ check, you now have the option to ‘Delete User’.