In this week’s release, we have enhanced explainability, auto-domain discovery, and a smattering of smaller but mighty updates!
💡More Context Provided for Failing Users
We know it’s always helpful to have as much context as possible when you’re investigating a user who is failing checks, and regular release note readers will be familiar with the recent additions to the check side drawer. This is something we refer to as “explainability”.
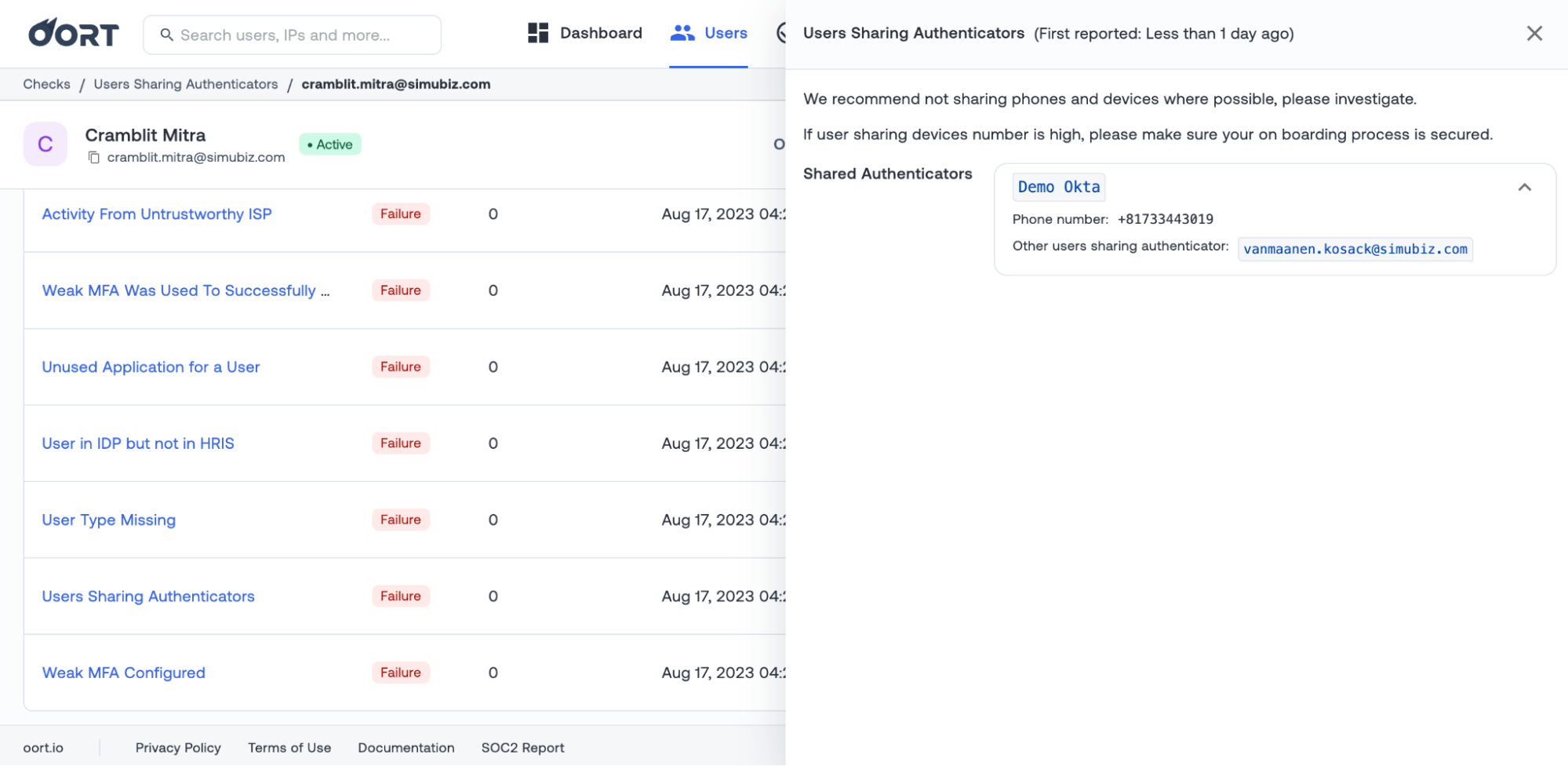
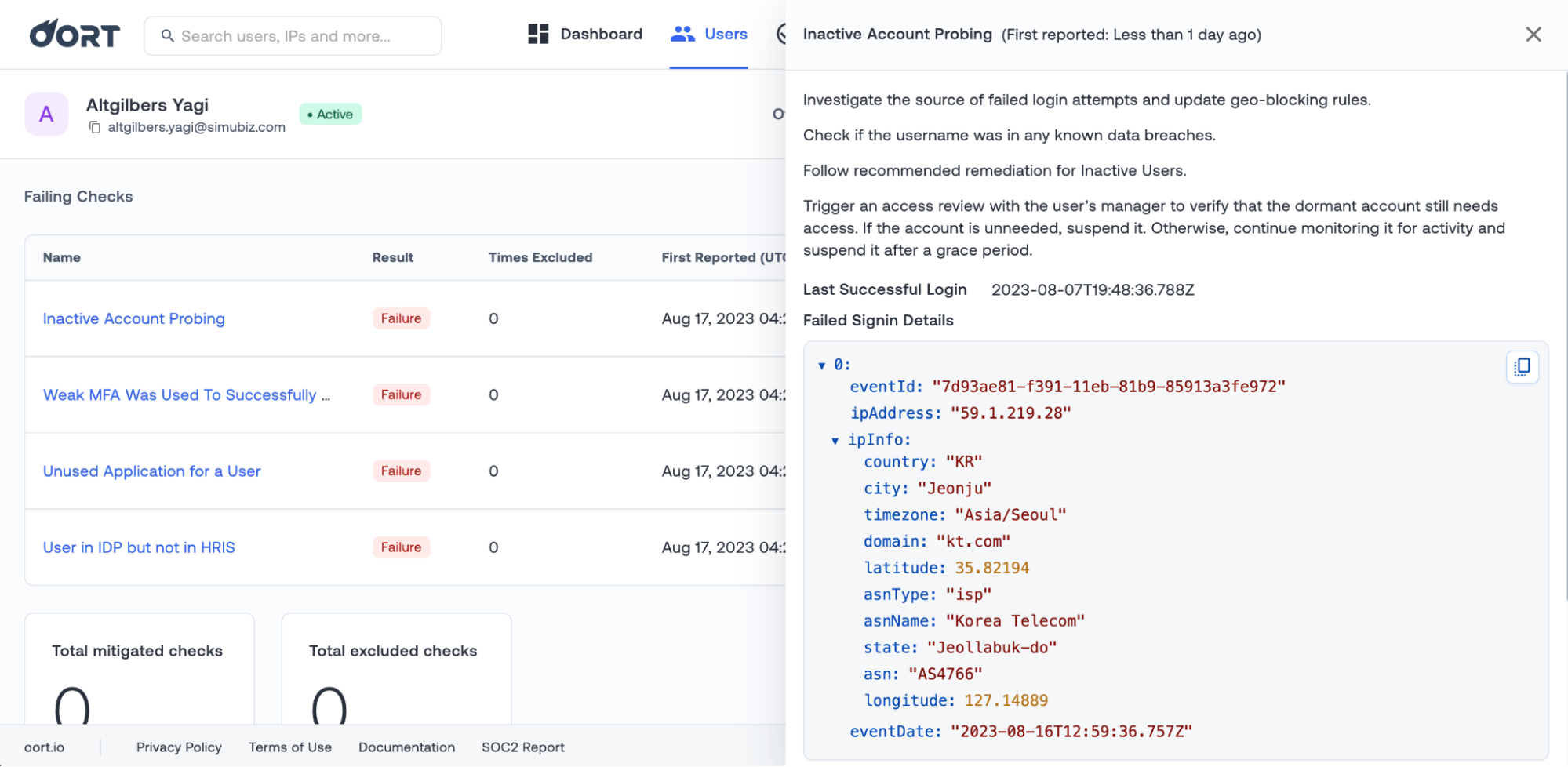
First, we have added context from IPInfo to the Inactive Account Probing check. You will now see information like country, domain, ASN name, and type alongside other data on the failed login attempts.
 Second, the “Users Sharing Authenticators” will now easily display any other users who are using the same authenticators. Clicking on this user chip will take you to that specific user profile.
Second, the “Users Sharing Authenticators” will now easily display any other users who are using the same authenticators. Clicking on this user chip will take you to that specific user profile.
🔍 Auto-Discovery of Rare Email Domains and Browsers
Many of the Oort checks come with Custom Detection Settings, which can be found on the Check Details page. These custom settings help to tune the checks to your specific policies and thresholds.
In this release, we have introduced auto-discovery for two checks: All/Block Email Logins and Rare Browser Activity.
In the case of the All/Block Email Logins check, the auto-discovery will look for domains specific to your own environment. What defines rare? You tell us in the “Rare Domain Threshold Occurrence”. By default, this will be 5, but you can change this to your own number. Enabling auto-discovery will mean that the domains we alert for the checks are as specific to your environment as possible and will dynamically stay updated.
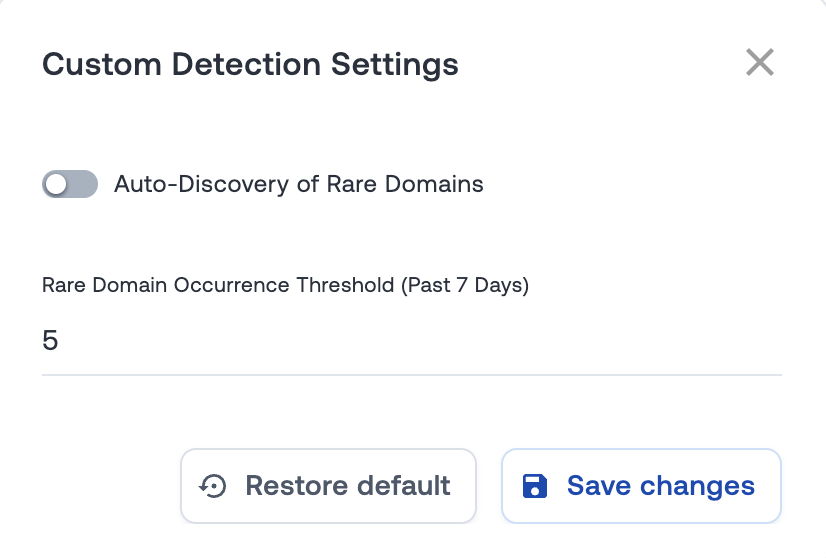
A similar story is true for the Rare Browser Activity check, which will look for rare uses of unusual browsers, defined by how many devices have accessed that browser.
Please note we’re busy making some changes to the allow, block, and ignore lists to further enable this workflow.
🕐 New Filter to Help Prioritize Check Response
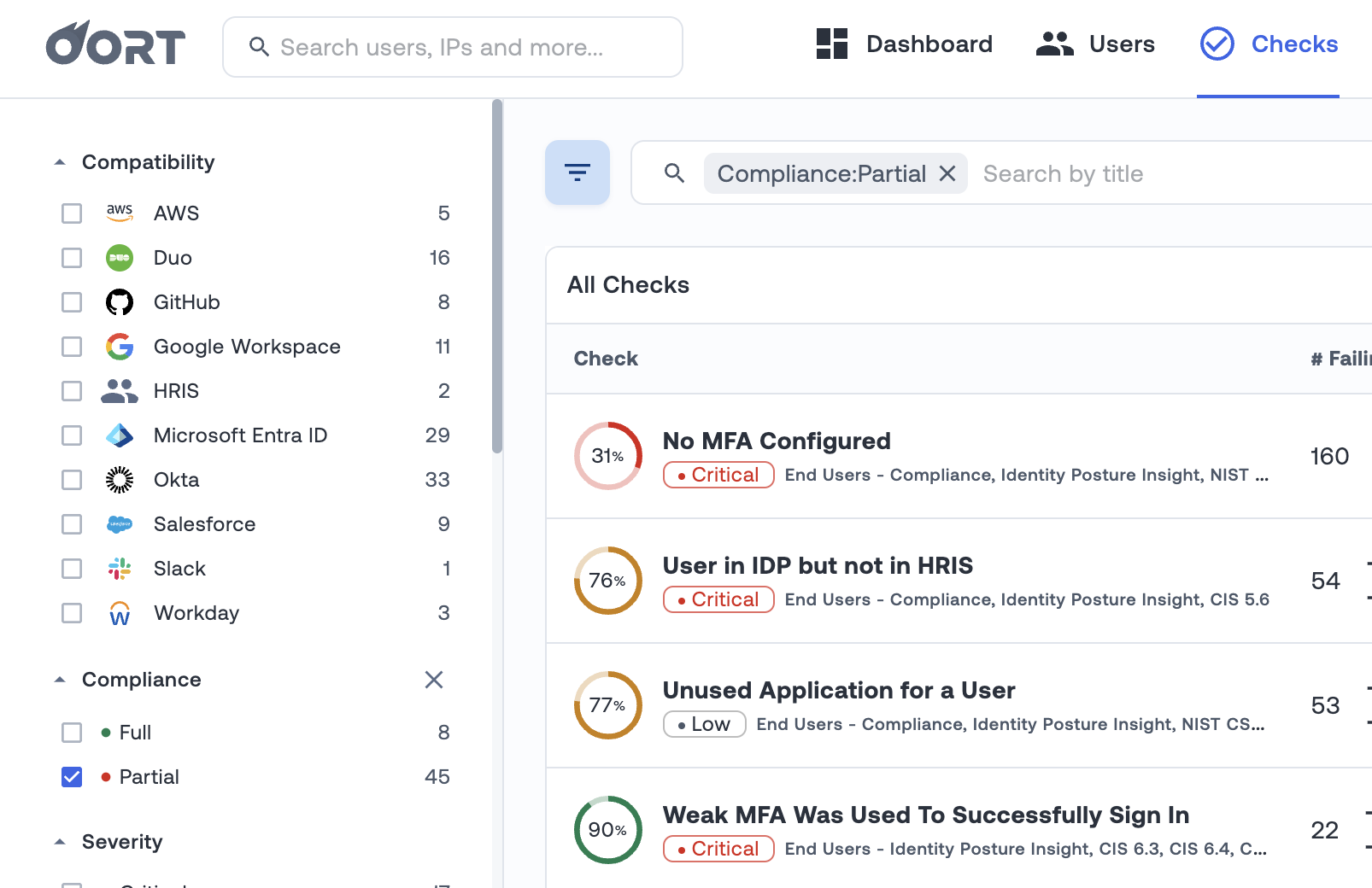
With more than 50 pre-built checks, we want to ensure that you can best prioritize your efforts. Each check has a compliance percentage that helps you to track how you are performing and gamify remediating the issues. Once you are at 100% compliance, you can give yourself a pat on the back and focus on the next biggest issues.
To track your progress, we have introduced a new filter. This “Compliance” filter enables you to select between Full and Partial. For example, if you only want to see the checks that have failing users, you can select the “Partial” filter. An example of this is displayed below.
 Bug Fixes and Minor Improvements
Bug Fixes and Minor Improvements
- IP Tags. Additional tags are displayed in the User Profile Networks tab. This includes a “Personal VPN” tag, which helps you to pinpoint IP activity from employees using personal VPNs.
- Super Admin Login to Google. Extended coverage of this check to include all admin activities, not just the sign-in. This will help to provide greater visibility into super admin activity in Google.
- Microsoft Entra ID (Azure AD) Renaming. The dashboard has been updated to reflect the new naming of Azure Active Directory, Microsoft Entra ID.
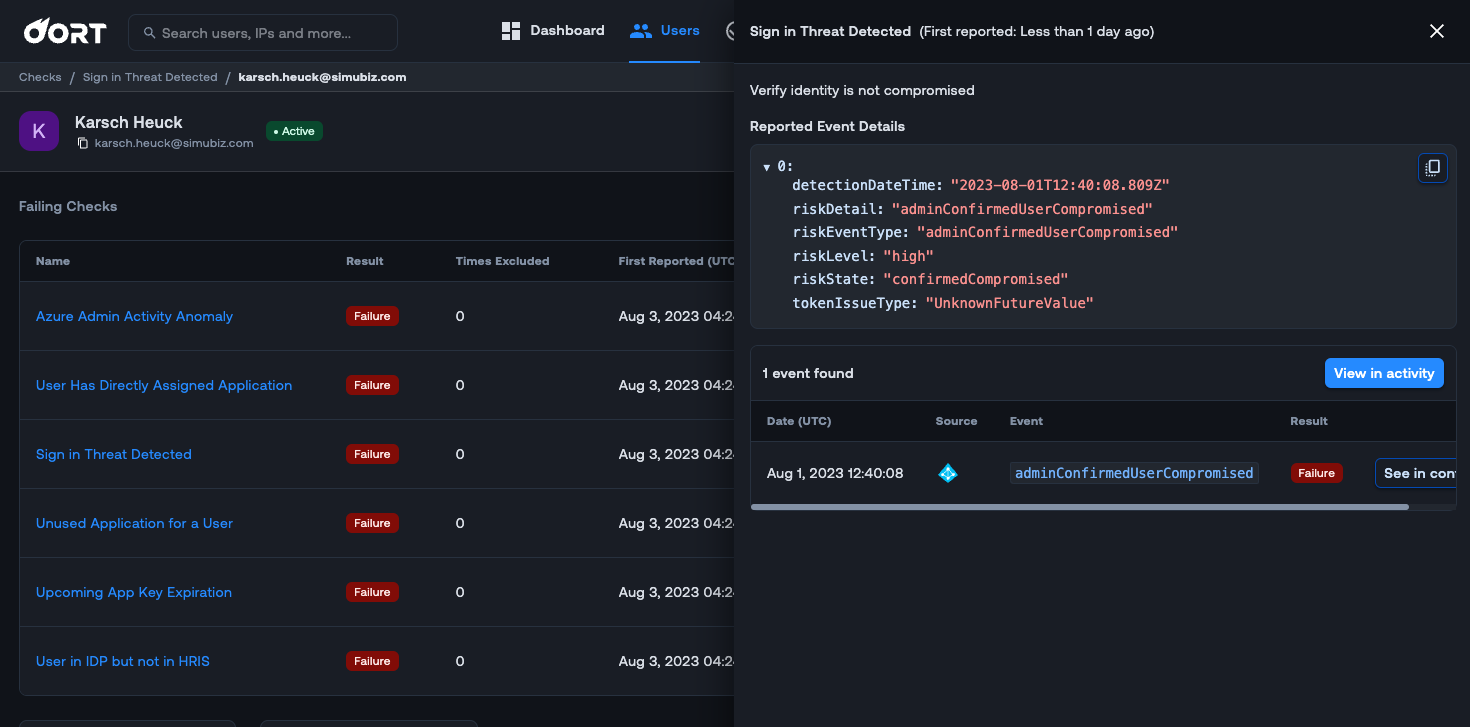
⚠️ Detect Risky User Sign-ins
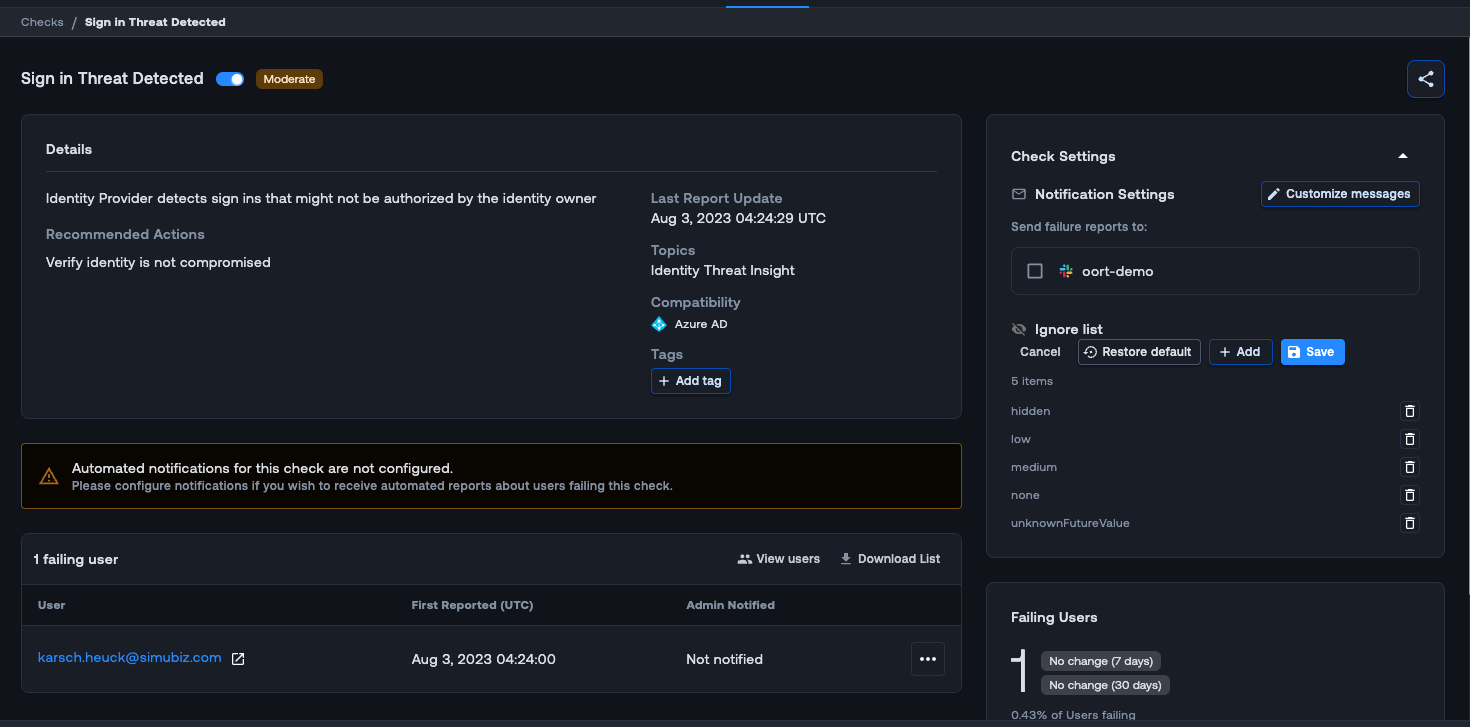
Keeping a pulse on the risky sign-in behaviors of user accounts when you are managing various activities related to your employees can be challenging. We are excited to introduce a new check for Microsoft Entra ID (Azure AD) called “Sign-in Threat Detected”. With this new check, Oort will now monitor Microsoft Entra ID Risk User events for “high” level risk users and trigger the check.
By default, the check will trigger on “high” risk levels, but by navigating to Check Settings in the check, you can customize the “Ignore list” to fit your needs. When you click on the failing check in the User 360 profile, an activity drawer opens to the right. This drawer gives you useful context for investigation such as insight into the user and why they are failing this check.
Bug Fixes and Minor Improvements
Ignore Slack provider in “No MFA” check - Slack does not return the proper indication if users are using MFA, causing false positives. We now ignore Slack for the No MFA check, which should reduce noise in your environment.
Weekly Digest - The weekly digest email from Oort allows you to get a snapshot of what is going on in your tenet. We have now added Oort admin activity which will give you an at a glance look at key admin activities.
GitHub - For GitHub integration, you will now see the “organization” in the activity drawer.