In this week’s release, we’ve introduced saved filters for the users tab, a new action for IT help desk teams, and even more context for checks. Read on, and enjoy!
💾 Save Time Querying Identity Population with Saved Filters
Earlier this year, we released the “Advanced Mode” for the search bar on the Users page, which enables you to create more complex queries across your entire identity population. This helps you to find specific parts of your population that have weaknesses. For example, you might want to see all guest accounts with weak forms of MFA that have been inactive in the last 30 days and experienced a password-spraying attack.
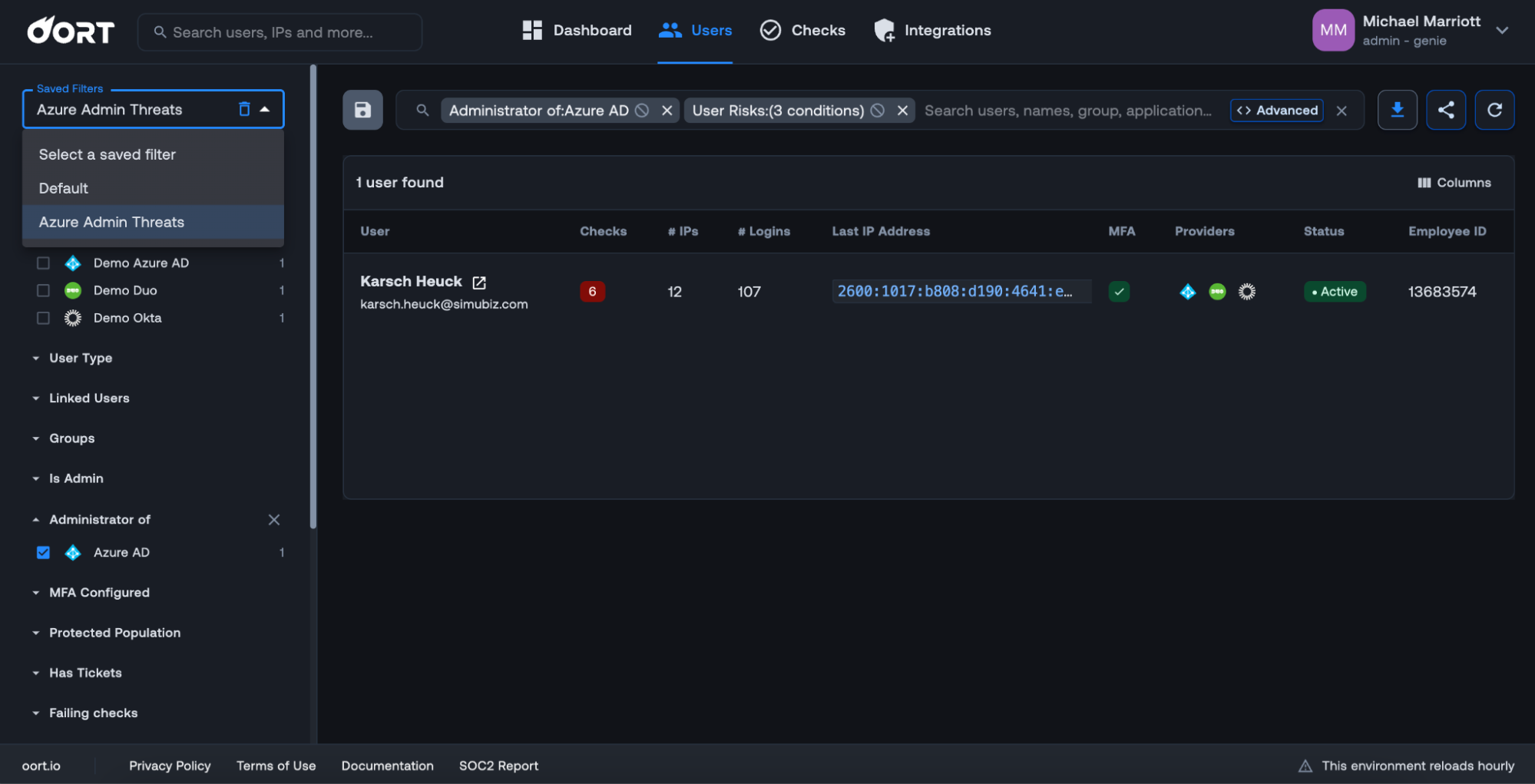
In this release, we’ve introduced saved filters. To create a new filter, simply select filters or craft your own advanced query in the search bar. Once you are happy, click the
“Save” icon on the left-hand side of the search bar. You will be prompted to select a name for your saved filter. In the example below, I have created a filter called “Azure Admin Threats” that is filtered by “Administrator of Azure AD” and “High”, “Medium”, and “Low” User Risks.
You can create multiple saved queries, which are available from the “Saved Filters” dropdown on the left-hand side of the page.
📳 New Actions to Support IT Helpdesk Teams
We all know that attackers are increasingly targeting identities as part of their campaigns. Social engineering is a significant part of this, with sophisticated campaigns calling up IT helpdesk teams to impersonate an employee and seek to reset a password or reset MFA. Helpdesk teams need a way to verify the identity of a caller.
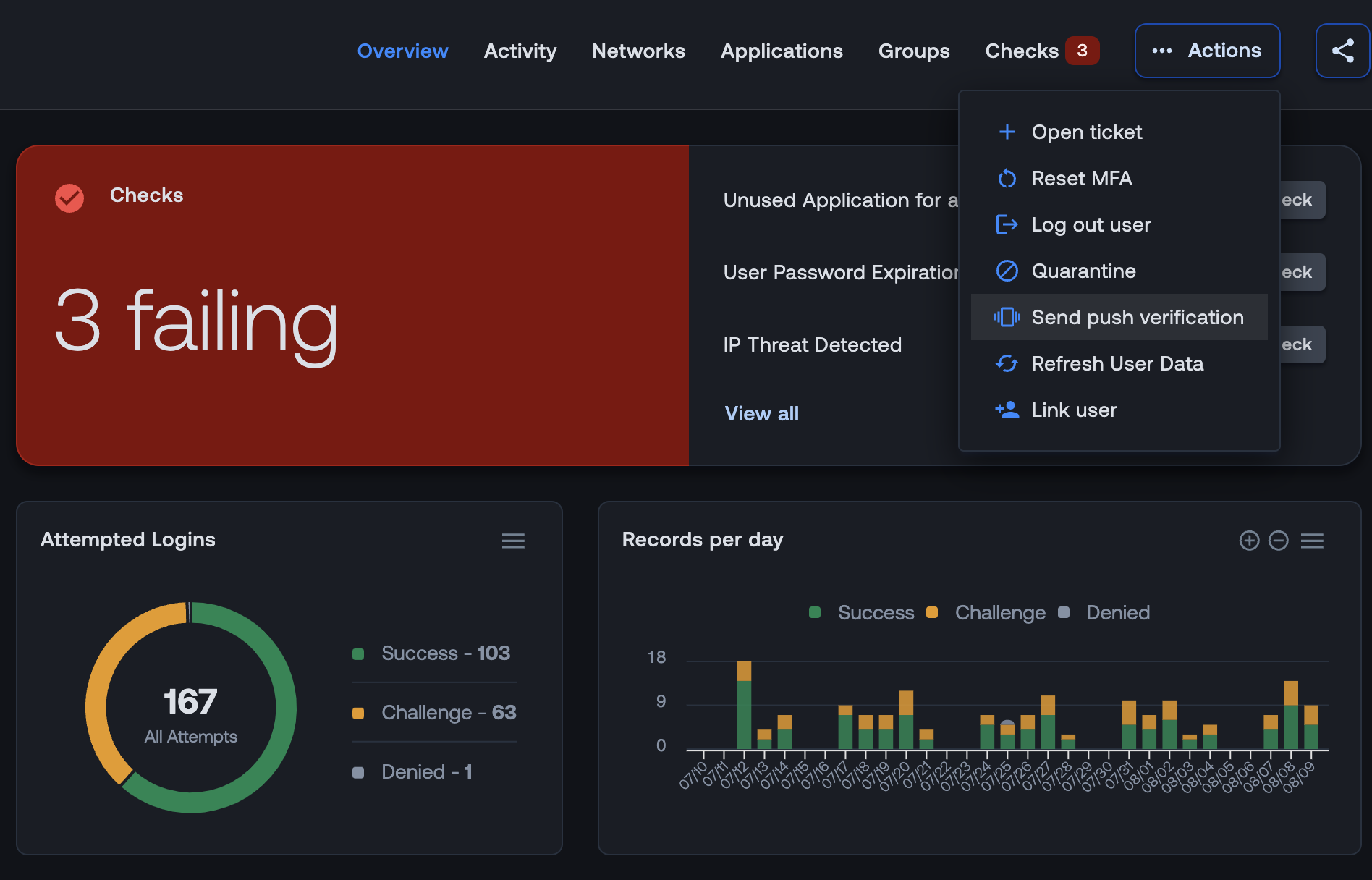
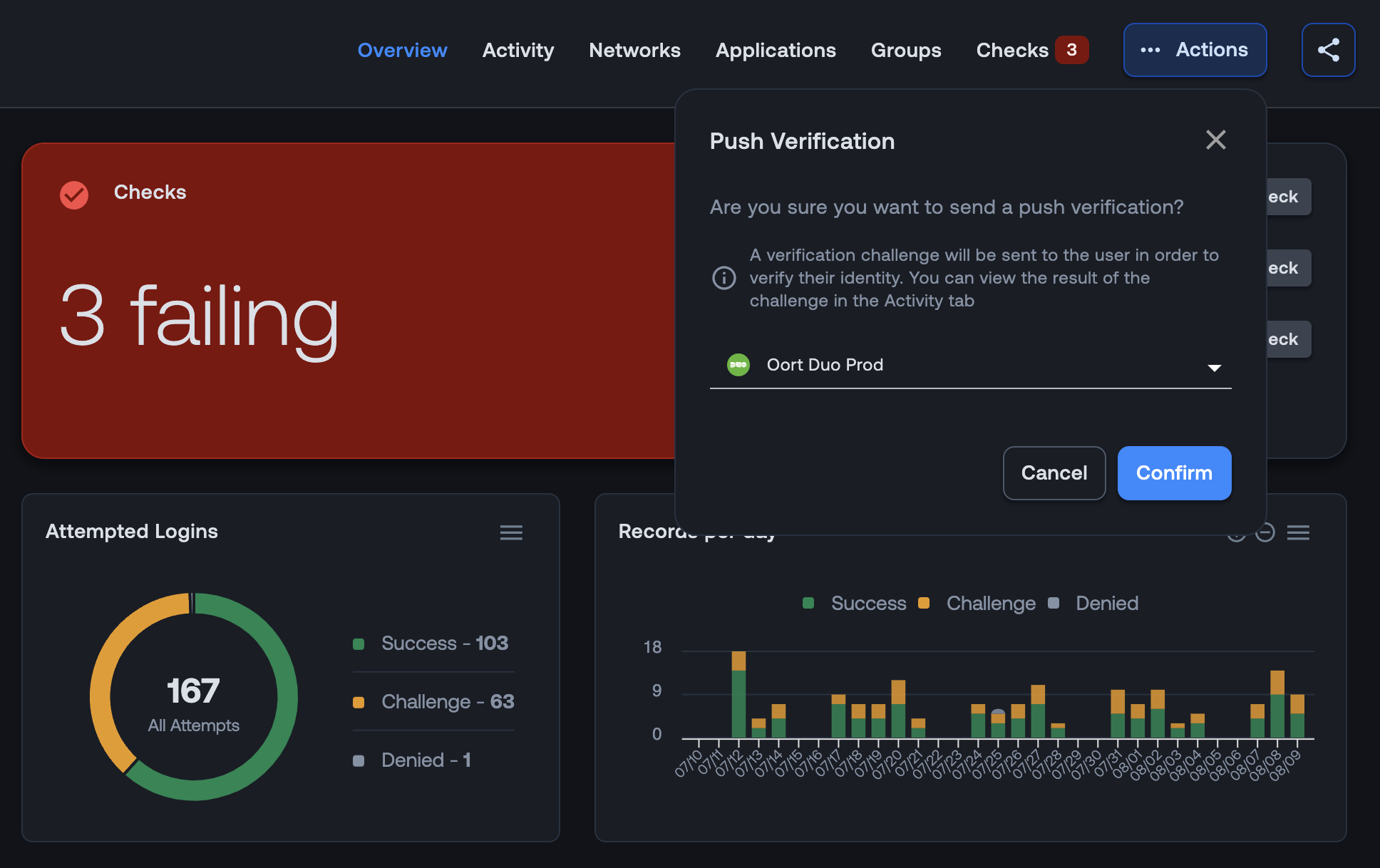
The context within user profiles can help to provide clues as to the legitimacy of the user, but another step. In this release, we’ve introduced a new action item, Send Push Notification. By clicking this button, support teams can send a one-off push notification to the user’s phone. The response will be recorded within the Activity tab of the user profile.
This new feature is available for all customers with Duo configured and requires Duo’s Auth API.
💡More Context for More Checks with Enhanced Explainabilty
When investigating a user with failing checks, it’s always helpful to have as much context as possible. Within the checks section of the User Profile, clicking on the check row will reveal a side panel to pop out on the right. This panel reveals some of the most important details and context for you to understand the precise issue.
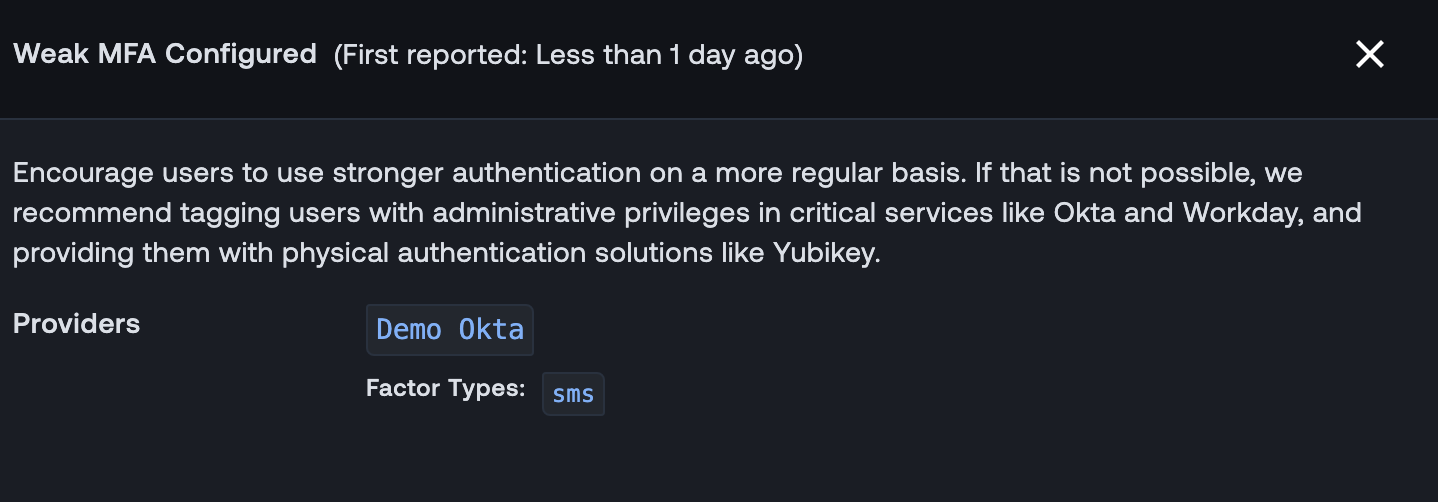
In this release, we have beefed up the information in this right-hand panel for five checks: Suspicious Activity Reported by User, Personal VPN Usage, Weak MFA configured, Sign in Threat Detected, and Missing Value In Mandatory field.
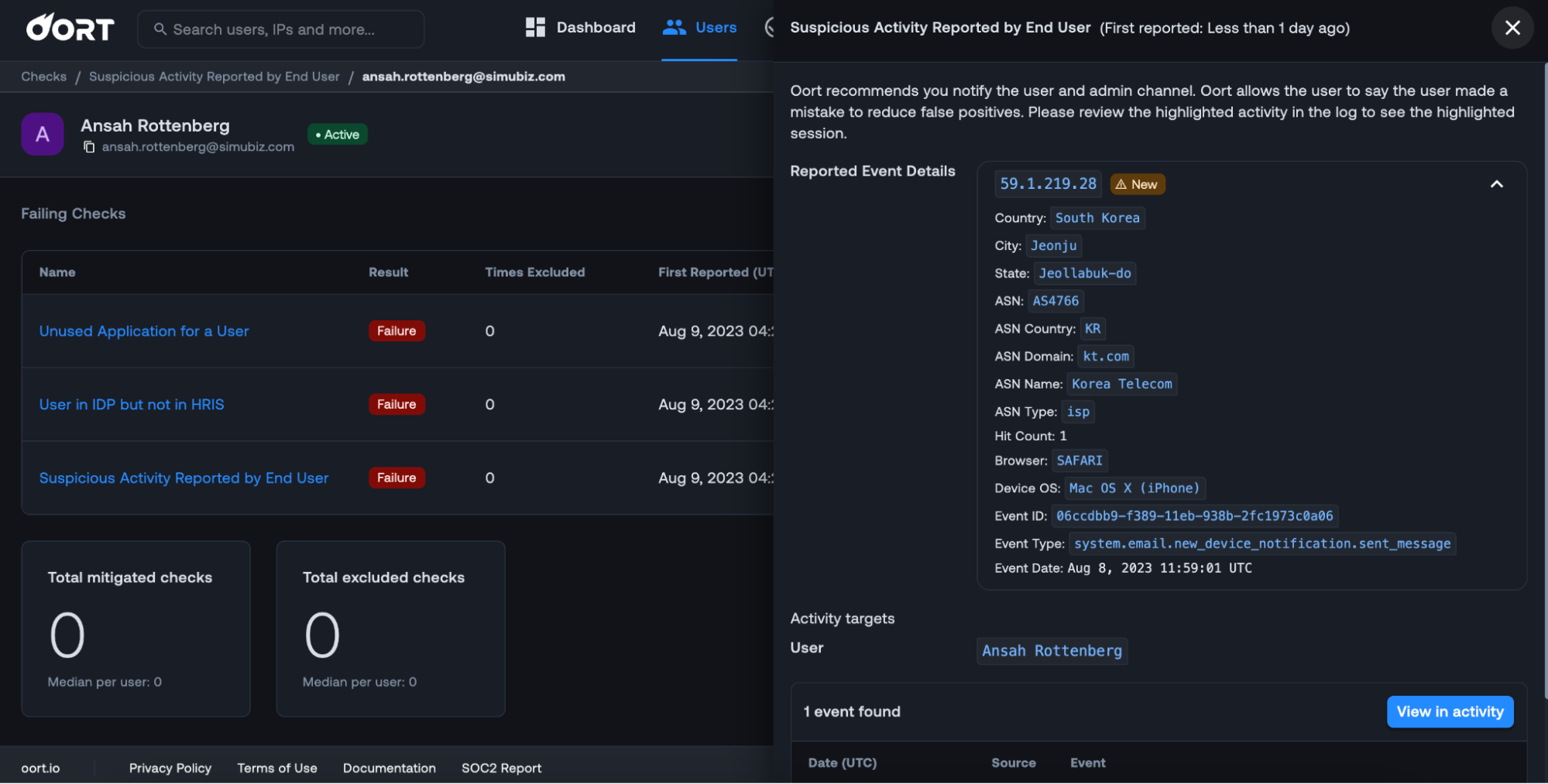
To give you an idea of why this is useful, check out the Suspicious Activity Reported by User check below. This now includes the IP address (which you can pivot on), country, browser, devices, OS, and other attributes.
Similarly, for the Week MFA configured check, you can see with identity provider(s) this applies to and specifically which factor was used. You can then pivot off the factor type to see what actions were performed during that session.
Bug Fixes and Minor Improvements
- Microsoft Entra ID (Azure AD) Collection. We have extended data collection to include two new data types: message rules and device audit events. We will use message rules to collect and search for suspicious email forwarding rules.
- Activity Tab Search. Advanced mode is now available within the Activity Tab of the User360 profiles. Selecting Control and Space will reveal the list of query suggestions.
- Service Accounts. Service accounts are now excluded from the “User in IDP but not in HRIS” check, as it is not relevant for this account type.
- IP Threats Filter. The Users Tab filters will now display different types of IP threats for you to search across. This includes Hosting, Malicious IP, Password Spray, Tor, and VPN.
⚠️ Detect Risky User Sign-ins
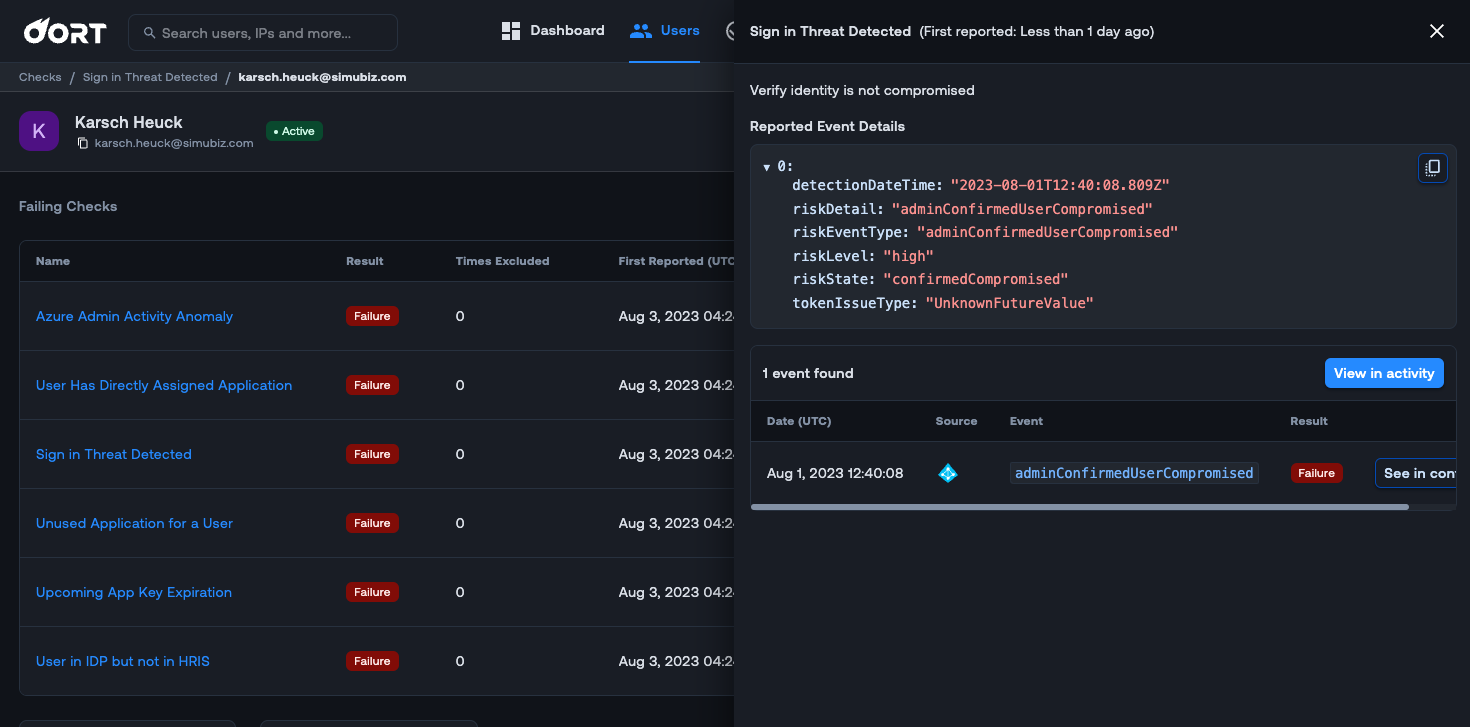
Keeping a pulse on the risky sign-in behaviors of user accounts when you are managing various activities related to your employees can be challenging. We are excited to introduce a new check for Microsoft Entra ID (Azure AD) called “Sign-in Threat Detected”. With this new check, Oort will now monitor Microsoft Entra ID Risk User events for “high” level risk users and trigger the check.
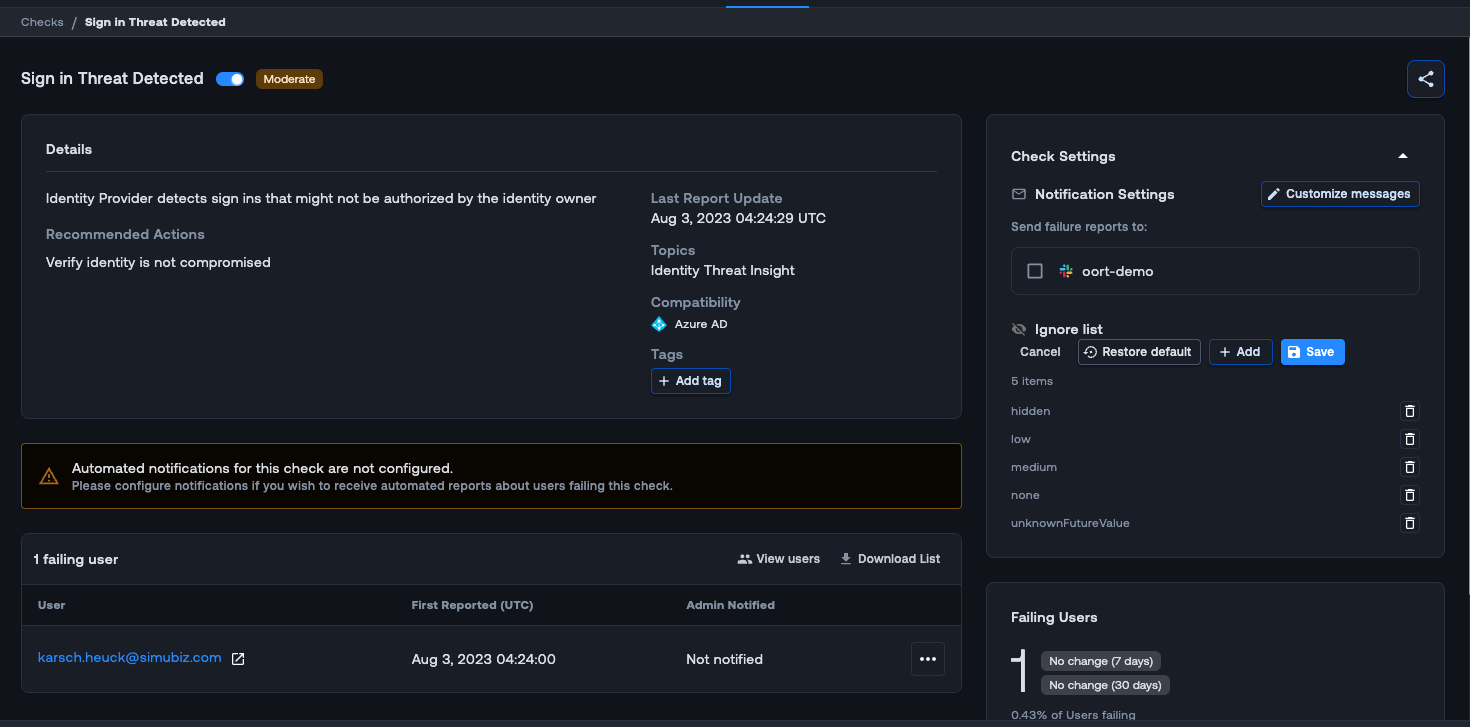
By default, the check will trigger on “high” risk levels, but by navigating to Check Settings in the check, you can customize the “Ignore list” to fit your needs. When you click on the failing check in the User 360 profile, an activity drawer opens to the right. This drawer gives you useful context for investigation such as insight into the user and why they are failing this check.
Bug Fixes and Minor Improvements
Ignore Slack provider in “No MFA” check - Slack does not return the proper indication if users are using MFA, causing false positives. We now ignore Slack for the No MFA check, which should reduce noise in your environment.
Weekly Digest - The weekly digest email from Oort allows you to get a snapshot of what is going on in your tenet. We have now added Oort admin activity which will give you an at a glance look at key admin activities.
GitHub - For GitHub integration, you will now see the “organization” in the activity drawer.