We have some more great product updates this week, including **THREE** all-new Identity Security Checks. If you’re an Okta customer, you’ll find these especially valuable in keeping your Okta security in line with your policies.

Speaking of product, our VP of Product Management, Nico Dard, is hiring a product designer! It’s an exciting opportunity and time here at Oort, so check out the job description here on LinkedIn and submit your application or send the job posting to a friend if you know someone who’s a great fit!
Improvements:
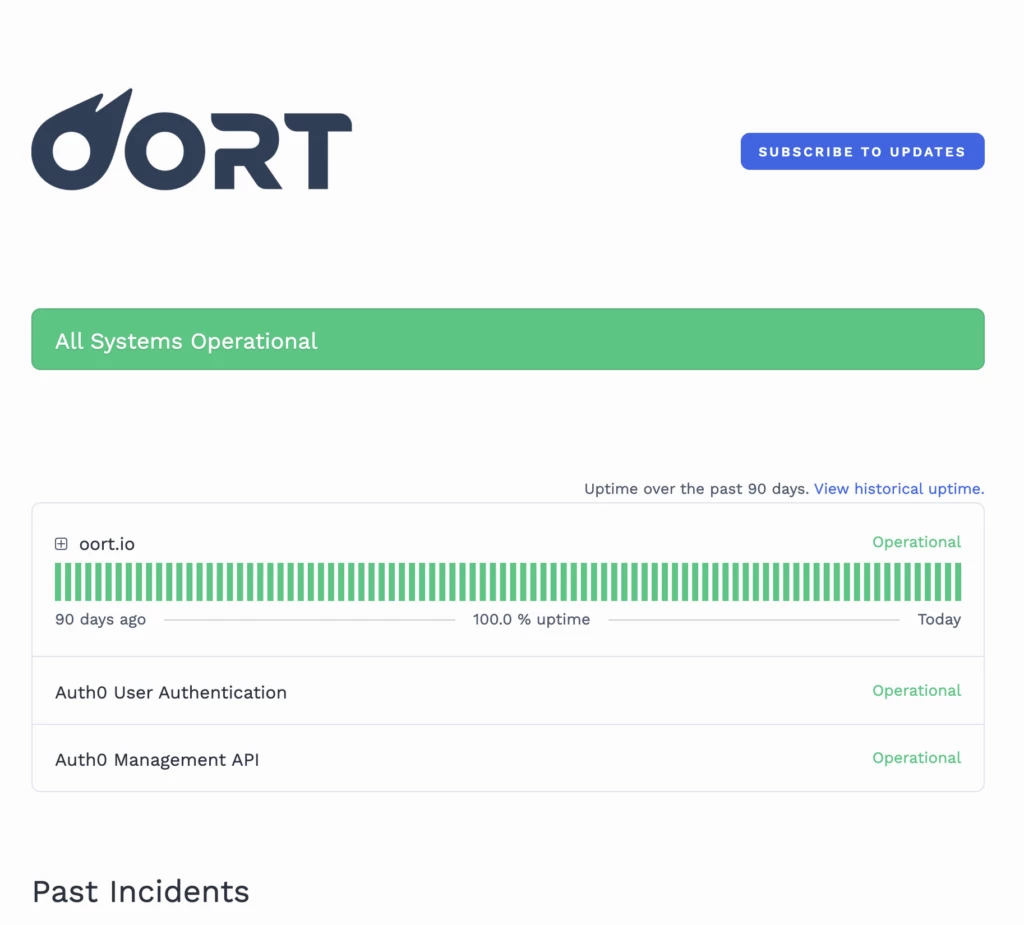
🆙 We made some updates to our status page to better communicate to our customers when our partners or service providers are down and causing downstream disruptions to the Oort identity security platform. Check out the updates on our status page here.
New Features
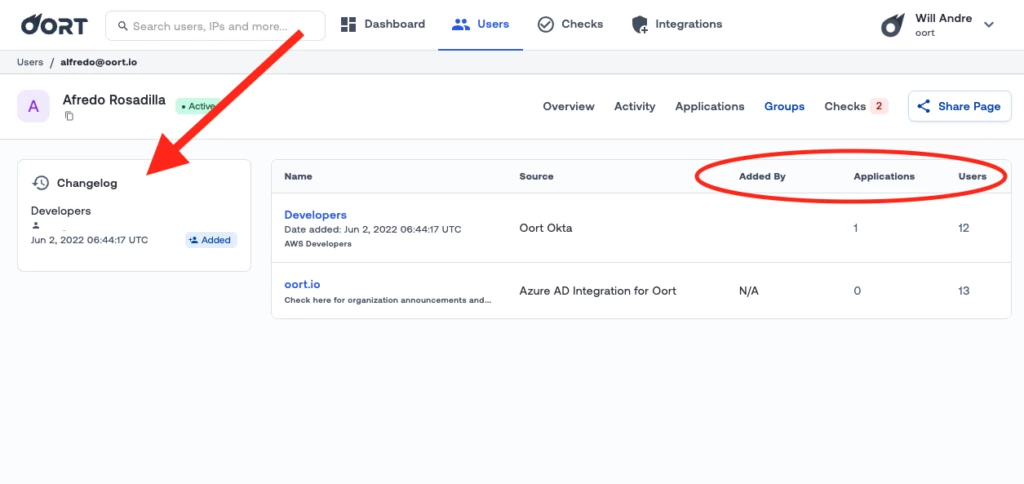
👥 New Information in User Detail > Groups + Changelog
In the user details page of any identity, you can now see enriched information about their group memberships including who added that user to the group, the number of applications that group can access, and the number of users in that group. Additionally, there’s now a changelog of all changes to group memberships which is useful in understanding whether there were recent changes that might be related to any identity threat investigation.
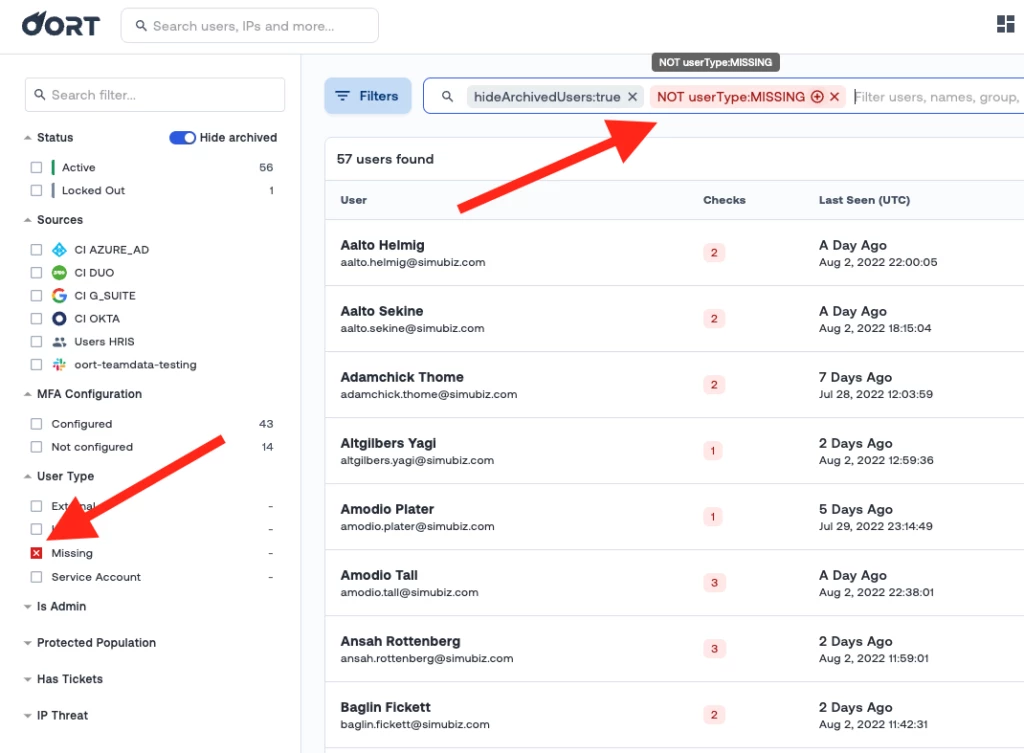
❌ Inverse Filters Active
You can now see in the sidebar which filters you have inverted from include to exclude. This helps identity threat hunters to easily visualize which criteria they have applied to their user base so they can detect threats faster.
**NEW** Identity Security Checks:
✅ Risky Parallel Sessions
This behavioral check alerts when the same identity is logged into more than one session within a set period of time (configurable by days). This behavioral anomaly can potentially indicate active credential sharing either within the workforce or to external users. Naturally, this behavior increases the risk of data leakage, loss, or mishandling and should be investigated.
COMPATIBILITY: Okta
✅ Service Account Successful Sign In
This check will alert on successful logins to service accounts through the IdP. Service accounts are normally backend-to-backend communications, so logging in to one through an identity provider such as Okta or Azure AD could be an indicator of compromise.
COMPATIBILITY: Okta, Azure AD
✅ Login to Admin Console in Okta
This check collects the identities that have logged into the Okta admin console within the past seven days. There are usually very few people who are authorized to do this, so this check flags and alerts on this activity so that the accounts and the associated activity are brought to the attention of the Oort admin.
COMPATIBILITY: Okta
That’s a wrap for this week! Make sure you subscribe to our updates up top so you don’t miss any new features or announcements coming from Oort! Can’t wait? Get a demo today!



