Following an exciting week at Identiverse 2023, we’re starting off the week with a flurry of new capabilities. This week, our headline item is a new check for monitoring activity from untrustworthy Internet Service Providers (ISPs).
⚠️ Monitor Activity from Untrustworthy Internet Service Providers
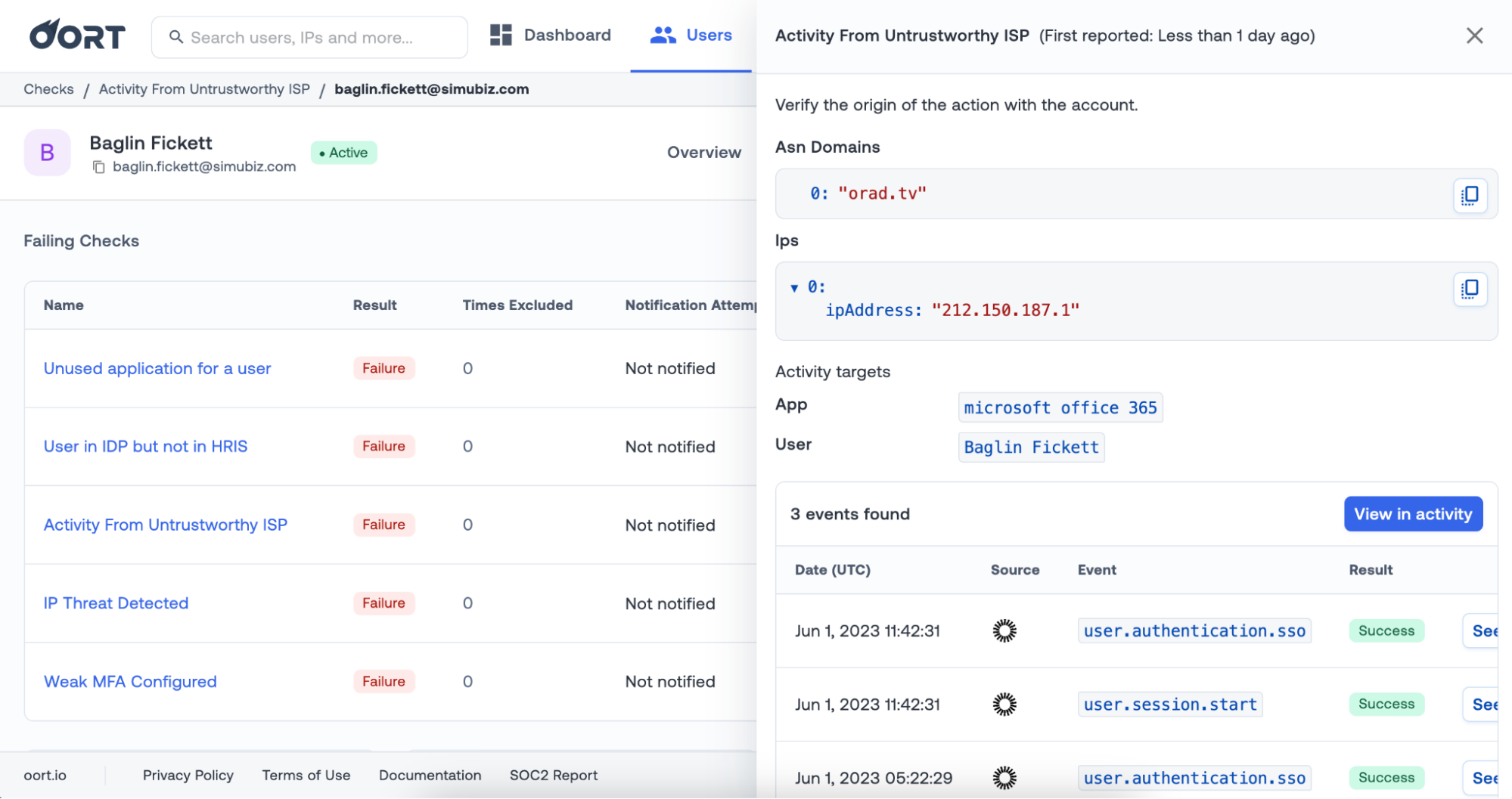
You may have noticed that we have recently put a lot of effort into adding more identity-related context from IP addresses. This has included adding in ASN (autonomous system number) data, such as ASN, ASN Domain, ASN Name, ASN Type, and ASN Country.
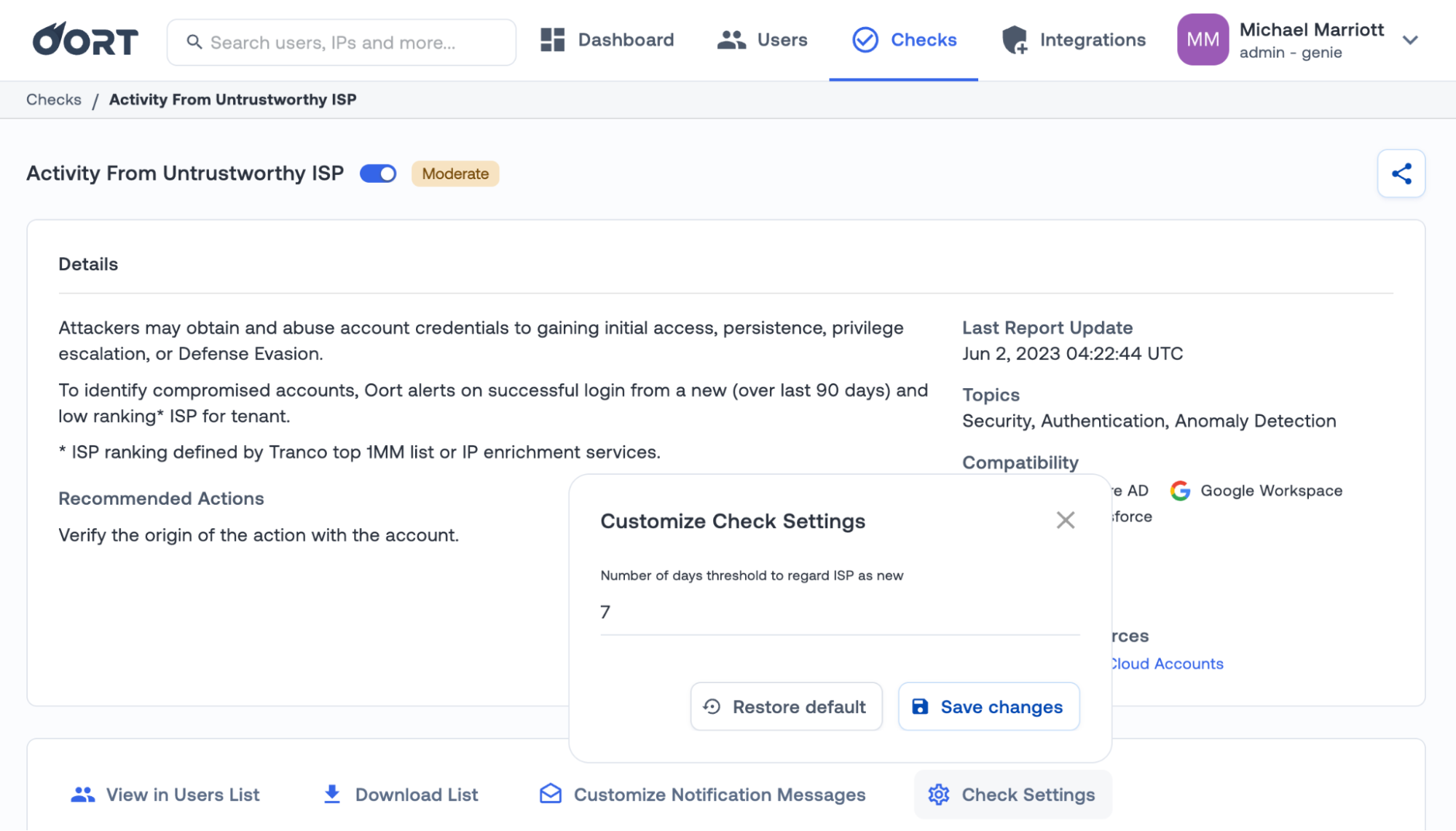
You may want to track activity from ASN domains that are untrustworthy, which is exactly what we have introduced this week with the “Activities from untrustworthy ISP” check. This continuously monitors for successful logins from new ISPs that have a low trust score. New ISPs are those that have not been seen in the last 90 days, and the trust score is calculated from enrichment services and the Tranco Top 1M list.
📧 Wizer Security Awareness Videos Available in Check Notification Emails
We recently introduced Wizer security awareness videos into Oort checks. These videos have been available in the Oort Dashboard, as well as in Slack messages that go to impacted Users. Included short videos help the user to understand the associated security risk of their failed check, such as using weak forms of MFA.
Videos are now also available in email-based alerts, further enabling users and managers to understand the importance of identity security.
Bug Fixes and Minor Improvements
- Inactive guest account check. In addition to Azure AD, this check also covers Okta, Workday, and Slack accounts.
- Password expiration failure. Enhanced explainability to include the associated provider.
- RBAC roles. Role-based access controls now apply to Slack and Teams, so users without the appropriate permissions cannot mark checks as “normal behavior” or “interesting”.
- Observations “Expired” state. After seven days, Observations will show an “Expired” state. This will help to ensure you do not have stale failed event-based checks.
- Azure Factor History. New data displayed within User360 profiles to show the history of an MFA factors in Azure.


