Summary
Oort’s Engineering Team was on 🔥last week. This week, you can benefit from our new dashboard and the ‘Quarantine User’ action type.
We’re also introducing the Oort Knowledge Base this week. This knowledge base is where you can find all previous release notes, integration guides, and product documents. We’ll build this out more over the coming months, so get it bookmarked!
☢️ Quarantine Compromised Users
Let us outline a scenario. A malicious actor acquires legitimate credentials for an inactive account and attempts to log in. The account had no MFA, and the attacker was able to register their own factor. The user starts to perform unusual actions – from no activity in the last 30 days, suddenly, they’re highly active and performing suspicious actions from strange new IP addresses.
You need to act–and act fast.
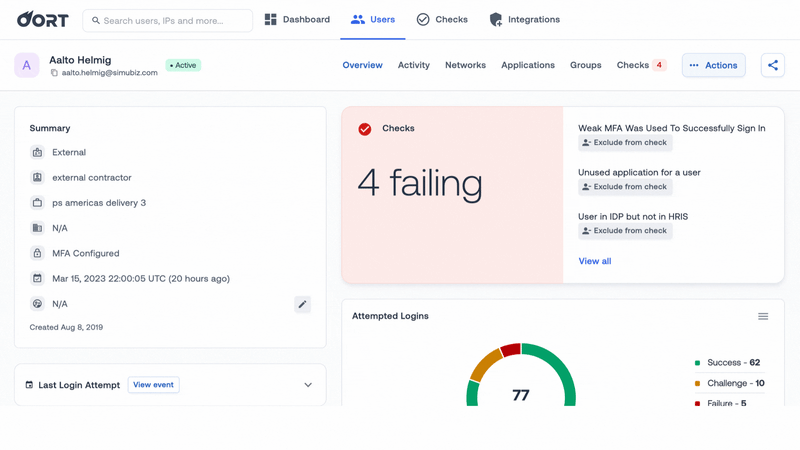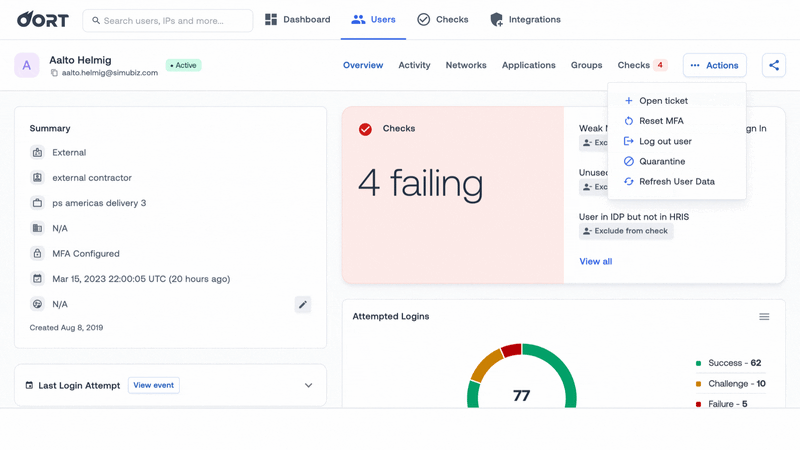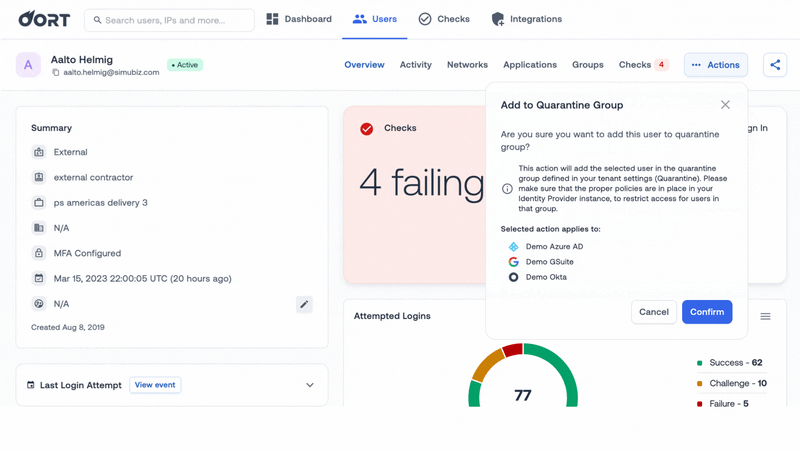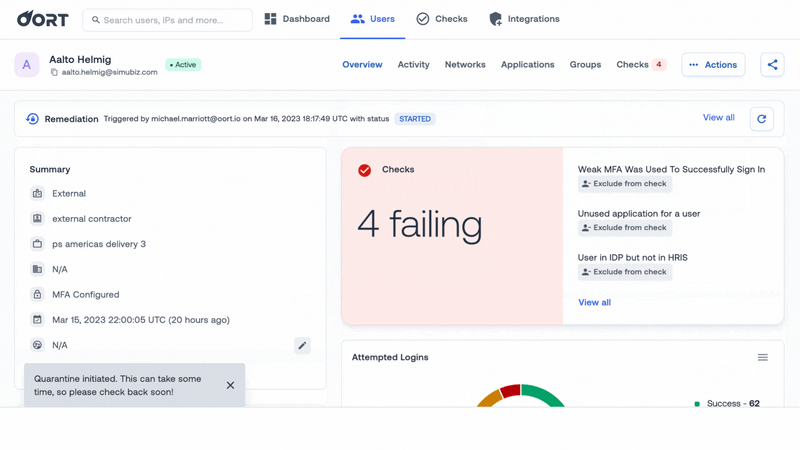
To prevent the compromised account from being used to access sensitive applications and data, you need to quarantine the account.
This action works by moving the user into a quarantine group. You can define the policy for your quarantine group, which will vary from organization to organization. You can define what they have access to and what to do with the account after you have investigated (you can either move the user out of the group or remove the user account entirely).
Please note this capability will require read-write API permissions. If you’d like any support or questions, don’t hesitate to contact our team.
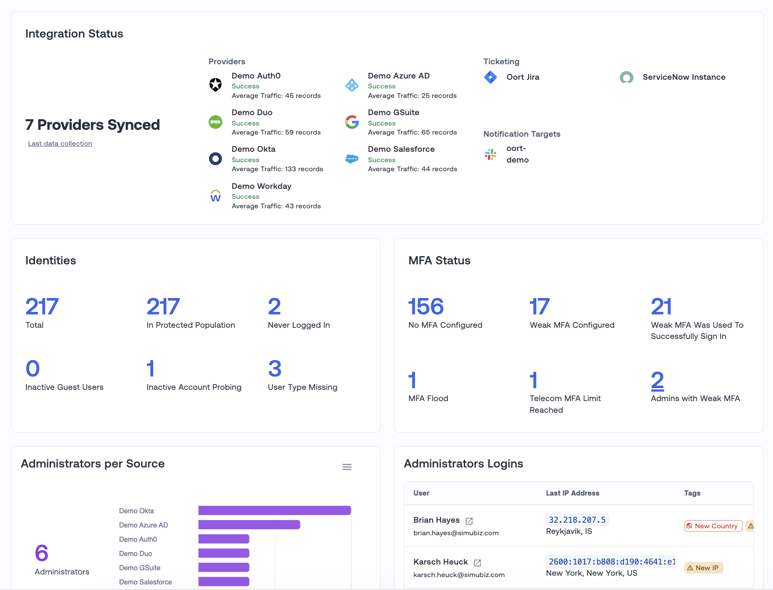
🖥️ New Dashboard has Landed
Many of you have been excited to get your hands on our new dashboard, and rightly so! The dashboard provides an overview of some of the most critical aspects of your identity security program, including:
- Identity Snapshot. Understand your total number of identities, including inactive and guest accounts. This also includes the different sources of your identities and any hygiene issues associated with those users.
- Administrator Snapshot. See how many administrators you have across different identity platforms and their latest logins. This helps to protect your most targeted users, with our recent research finding that administrators encounter three times more attacks than regular users.
- Threat Activity. Identify accounts experiencing threats like inactive account probing and MFA flood attacks.
- Multi-Factor Authentication Status. See how many users have no MFA or weak MFA and usage trends.
- Login Geolocation. All user logins are displayed in a helpful map view, showing where your users are logging in.
- Unused Applications. Track applications with no or little usage. Removing access can reduce costs and reverse permission creep.
We’ve made the components dynamic so you can drill down into the full data and explore for yourself. For most of the components, you can also download the CSV (or the image of the chart) from the component itself. For further details about our new dashboard, check out our blog, ‘Oort’s New Identity Security Dashboard.’
We'd love to hear from you if you have any feedback or suggestions for the dashboard!
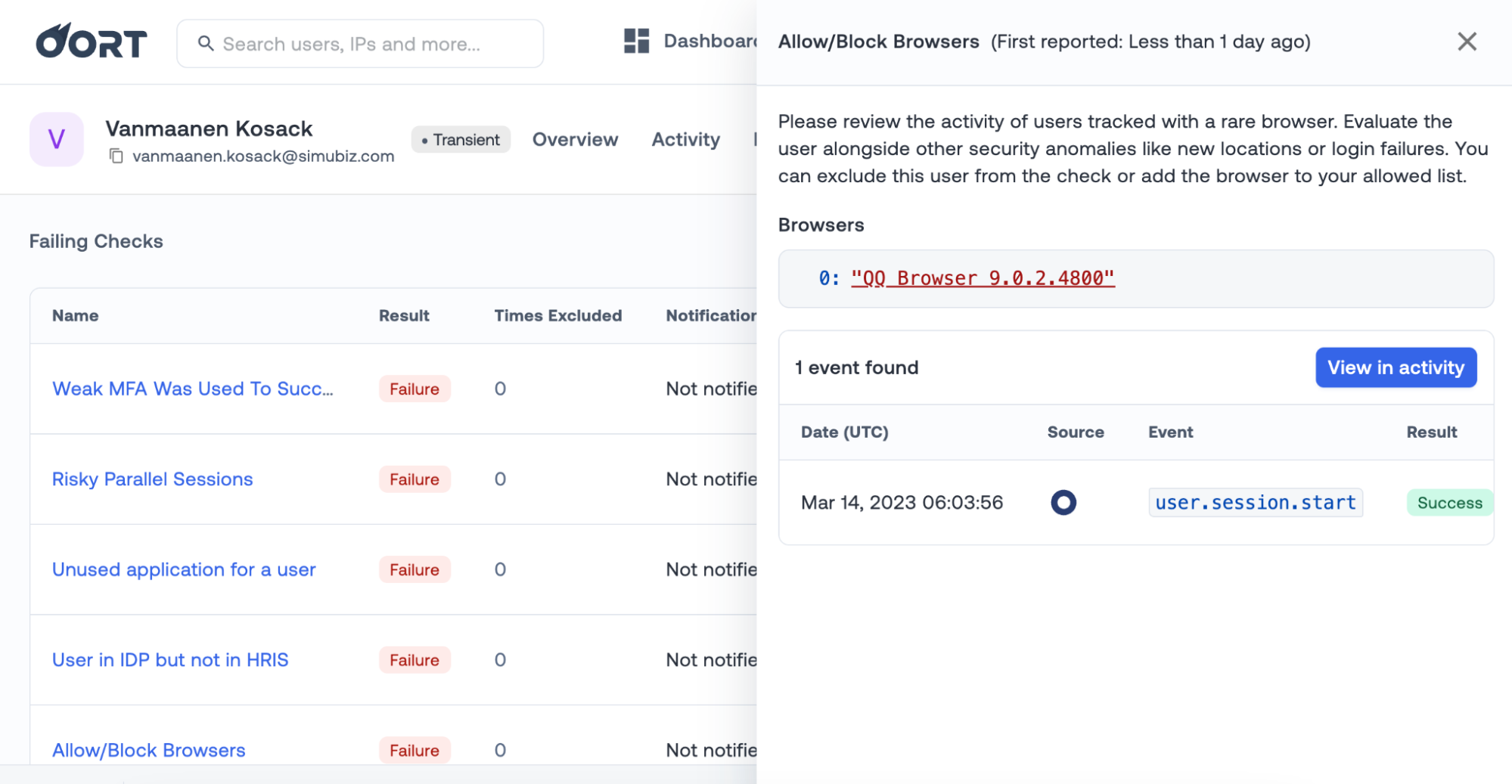
✍️ Rare Browser Activity
Last week we announced that we had increased the type of browsers we detect suspicious logins for. In this week’s release, we’ve added more context in the side panel to quickly identify the browser in question and understand the risk. Detection for this check type is also expanded. We previously analyzed the last browser used to log in, whereas the check will now look at all browsers used for the login.
Bug Fixes and Minor Improvements
- IP Context for Reported Activity. Additional context on an IP address is available in the activity panel for the ‘Suspicious Activity Reported by End User’ check.
- Sensitive Applications. In Tenant Settings, under ‘Sensitive Applications,’ you can edit and add applications you wish to define as sensitive. A bug that wrongly named applications from Okta has been fixed.


