Today, we’re unveiling our new integration with Polarity.
For those of you unfamiliar with Polarity, it’s awesome. The premise is simple but powerful. Organizations have a ton of data that can be extremely valuable for security teams, whether they are responding to an incident, hunting for threats, or gathering threat intelligence. However, that data is often sat in silos and inaccessible to analysts. To get that context, they would first need to be given access, and then proceed to login to every different application.
That’s where polarity comes in. Polarity provides a desktop client that acts as an overlay for any application you may be working on. It then takes data from different integration partners via APIs and fuses them together in a unified view to provide immediate context on observables.
Ultimately, this means faster response time and higher confidence.
Why Security Teams Need Identity Context
Security teams have IP and IOC context coming out of their ears. Some are better than others (we like IPInfo for IP data), but there are a number of providers and feeds to choose from.
However, as attacks have become more identity-centric, analysts need to better understand the 'who' behind an incident. If they had this kind of insight, the improvements to the speed of response would be significant.
Unfortunately, it is almost impossible to get that view of who the user is, what they have access to, and what they’ve been up to. This would be doable – albeit challenging – if enterprises had a single view of identities. But they don’t. Identity data is dispersed across multiple siloed populations.
Additionally, many Security Information and Event Management (SIEM) systems face challenges with static, entitlement data and a lack of understanding of the historical context. While they are powerful tools that collect, store, and analyze security logs, they often lack the ability to capture a continuous record of a user's identity. This 'Identity Memory' gap makes it tough for security teams to have a distilled view of a user's past and present activities.
How the Oort - Polarity Integration Provides Identity Context
With Oort’s integration in Polarity, you can gain instant context on both IP addresses and email addresses.
When investigating an IP address, you will be able to easily see the information about all users associated with that IP address. These results will link to an overview of each user's info, including name, status, phone number, user type, associated IP addresses, factors used, applications used, and locations of recent sign-in. Of course, you can also access this context by looking up a user email address directly.
What sets Polarity apart is its ability to act as an overlay across other applications. For example, if you’re working in Splunk and need this context, this information from Oort will be instantly available when you pivot off an IP or email address with the Polarity desktop client. This will save security teams hours of time responding to identity threats.
What Sets Oort Apart
We aim to provide the most comprehensive, richest view of an organization’s identity population. To do so, we integrate with identity providers like Okta, Microsoft Entra ID, Cisco Duo, GitHub, and, most recently, AWS. We then merge identities across these platforms to provide a consolidated view.
But it doesn’t stop there because it’s the depth of integrations is what truly sets Oort apart. By combining static entitlement data with dynamic, event-centric data, Oort affords unparalleled identity security insights. Here’s the difference:
Scenario 1: Detect an anomalous event, including a suspicious, new IP address. In the session, the user performs administrative actions.
Scenario 2: An over-permissioned retail store worker has been inactive for 6 months, but all of a sudden becomes active again. Although they are located in London in the HR system, the login came from Romania, and used a back-up SMS factor that the worker had registered 5 years ago. The users granted additional privileges to other users, which is highly unusual for their role.
That’s why it is absolutely critical to combine entitlement, static data with real-time event data. That’s exactly what we do in our User360 profiles.
Oort-Polarity Integration Overview
If this combination of Oort and Polarity sounds like the solution your security team has been looking for, setting it up is straightforward.
Generate API Credentials. Begin by creating the New Polarity Integration in Oort. During this process, you'll need to generate API credentials. While entering the necessary details, only the name is mandatory; adding a description or custom header name is optional.
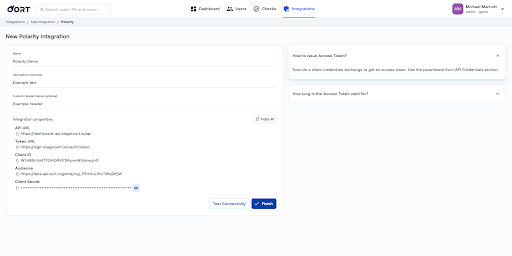
Download the Code. Once you have your API credentials, head over to https://github.com/polarityio/oort to download the integration.
Start your Analysis. Start by looking up a user email address or IP address, and see the type of information you can get from Oort. This includes name, status, phone number, user type, associated IP addresses, factors used, applications used, locations of recent sign-in, and other users associated with that IP address.
Getting Started
Identity context is not just an added luxury; it's a necessity for modern security teams. By integrating identity data into Polarity, security professionals can arm themselves with the context they need to enhance their ability to detect and respond to threats.
To get started with Oort's integration with Polarity, visit https://github.com/polarityio/oort.
You can request a live demonstration and speak with our team by following this link: https://oort.io/demo.


