In today's digital landscape, where organizations heavily rely on technology and automation, managing machine identities has become a crucial aspect of identity security. Machine identities, also known as non-human identities, refer to accounts and identities associated with machines, systems, and applications. In this blog, we will explore the types of machine identities, the unique risks they pose, the levels of maturity in managing them, and key performance indicators (KPIs) to consider.
Types of Machine Identities
Machine identities encompass various types of accounts and identities. One prominent example is service accounts, which are created to cater to specific applications or services. These accounts often exist across multiple systems, making it challenging to track and manage them effectively. Other examples of non-human identities include shared mailboxes and network devices.
Unique Risks with Machine Accounts
Machine accounts introduce unique risks to organizations. Service accounts, for instance, often possess elevated privileges and access to sensitive resources. This makes them attractive targets for potential attackers seeking to exploit these accounts. Moreover, service accounts may be shared among multiple users or applications, creating intricate scenarios that can lead to security vulnerabilities.
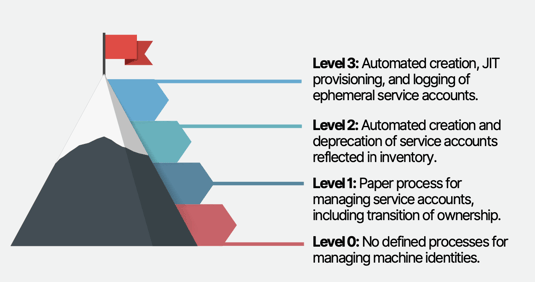
Levels of Maturity in Managing Machine Accounts:
Level 0: No defined processes for managing machine identities.
Level 1: Implementing a paper-based process for managing service accounts, including the transition of ownership to ensure accountability.
Level 2: Automating the creation and deprecation of service accounts, with proper reflection in the user inventory.
Level 3: Advancing to automated creation, Just-In-Time (JIT) provisioning, and logging of ephemeral service accounts, which are used for one-off tasks and have a limited lifespan.
 Source: Building an Identity Security Program, Oort 2023
Source: Building an Identity Security Program, Oort 2023
KPIs for Managing Machine Identities
To measure the effectiveness of machine identity management, organizations can consider the following key performance indicators:
Number of service accounts with unknown owners: This KPI helps identify accounts that lack clear ownership, indicating a potential security gap. Tracking this metric can drive efforts to assign accountability and prevent unauthorized access.
Account provisioning and de-provisioning time: Measuring the time taken to create and revoke machine identities provides insights into the efficiency of the process. Shorter provisioning times indicate streamlined workflows and reduced exposure to security risks.
Compliance with least privilege: Assessing the percentage of machine accounts with the least privilege principle ensures that each account has only the necessary permissions. Higher compliance rates demonstrate better control over access rights and reduced chances of privilege misuse.
Account usage and activity monitoring: Keeping track of machine account activities and monitoring their usage patterns helps detect anomalies and potential security incidents. This KPI can help identify unauthorized access attempts and ensure timely response.
Conclusion
Managing machine identities is crucial for maintaining a secure and well-structured identity security program. By understanding the types of machine identities, recognizing the unique risks they pose, striving for maturity in managing these accounts, and tracking relevant KPIs, organizations can enhance their overall security posture. Establishing robust processes, automating where possible, and maintaining accountability will ultimately help safeguard sensitive resources and protect against potential threats.
Understanding and managing your machine identities is a requirement for building true identity immunity. If you are building an identity security program, we have built a comprehensive blueprint that begins with understanding your current maturity across 11 factors. Download the full guide and contact us if you have any questions.
Oort’s Identity Security Platform
Oort is an identity-centric enterprise security platform. As a turnkey solution for Identity Threat Detection and Response (ITDR), Oort is providing immediate value to security teams by working with existing sources of identity to enable comprehensive identity attack surface management in minutes. Led by a team with decades of domain expertise across identity, networking, and security, Oort is backed by venture capital investors including Energy Impact Partners, .406 Ventures, Bain Capital Ventures, Cisco Investments and others. Market-leading technology companies, like Collibra and Avid Technology, rely on Oort to provide full visibility into their identity populations.
To get a free identity security health assessment, request a demo.



