Detecting identity threats is an important step, but an effective response is equally crucial. Organizations should establish clear processes and playbooks to respond to identity-related incidents. In this blog, we will explore best practices for efficiently responding to identity threats, including response playbooks, key performance indicators (KPIs), and levels of response maturity. By implementing these practices, organizations can effectively contain and remediate identity threats, minimizing their impact on security.
Response Playbooks: Clear and Actionable Guidance
Response playbooks provide security teams with clear and actionable guidance when responding to identity-related incidents. These playbooks outline the necessary steps to identify, prioritize, and remediate incidents, ensuring a consistent and effective response. By following established playbooks, security teams can reduce response time, minimize errors, and mitigate the impact of incidents on the organization.
To enhance the maturity of response playbooks, organizations can leverage Security Orchestration, Automation, and Response (SOAR) platforms. These platforms automate incident response processes, improving response speed and efficiency. Integration with ITDR tools and systems provides additional context and insights, enabling security teams to make informed decisions and take effective actions.
KPIs for Effective Response
Measuring response effectiveness is essential to identify areas for improvement. Some key performance indicators (KPIs) to consider include:
1. False Positive Rate: This metric measures the percentage of incidents flagged as threats but later determined to be false positives. A lower false positive rate indicates more accurate detection and reduces the burden on response teams.
2. Time to Respond to Brute-Forcing Event: This KPI measures the time taken to respond to brute-force attacks targeting user credentials. A quicker response helps prevent unauthorized access and limits potential damage.
3. Time to Respond to Compromised User: This metric tracks the time taken to respond to a compromised user account. Swift action reduces the window of opportunity for attackers and minimizes the impact of the compromise.
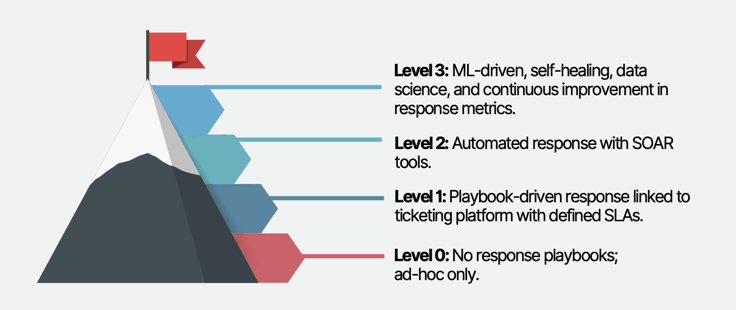
Levels of Response Maturity
To assess the maturity of response capabilities, organizations can evaluate their progress against the following levels:
1. Level 0: Ad-Hoc Response: No formalized response playbooks, with responses handled on an ad-hoc basis.
2. Level 1: Playbook-Driven Response with Ticketing Integration: Response playbooks are defined and linked to a ticketing platform with defined Service Level Agreements (SLAs). This level ensures consistency and accountability in incident response.
3. Level 2: Automated Response with SOAR Tools: Response playbooks are executed using SOAR platforms, automating incident response processes. This level increases efficiency and reduces manual effort.
4. Level 3: ML-Driven Self-Healing and Continuous Improvement: Response processes incorporate machine learning (ML) techniques for self-healing and optimizing response metrics. Continuous improvement efforts refine the response capabilities based on data-driven insights.
 Source: Building an Identity Security Program, Oort 2023
Source: Building an Identity Security Program, Oort 2023
Efficient Response Strategies
Efficiently responding to identity threats involves implementing various strategies, including:
1. Quarantine Users: Quarantine compromised user accounts within the identity provider, preventing access to any applications or services tied to that identity. This comprehensive approach limits an attacker's ability to bypass security controls.
2. Password Reset: Establish procedures for securely resetting passwords, ensuring strong and secure new passwords are set. Some platforms also recommend killing active sessions during the password reset process for enhanced security.
3. Killing Sessions: Immediately terminate hijacked sessions to prevent further unauthorized access. Logging the user out of all active sessions and revoking access tokens adds an extra layer of security.
4. Removing Access: If a user account is compromised, promptly revoke their access by removing their account from groups or roles that grant permissions to critical resources.
5. User Education and Awareness: Include procedures for user education and regular security awareness training. This helps users recognize threats, practice good security habits, and report suspicious activities.
6. Incident Response Plan: Develop a comprehensive incident response plan that outlines steps to identify, contain, assess, and recover from security incidents. Regularly review and update the plan to ensure its effectiveness.

Conclusion
Efficiently responding to identity threats requires well-defined response playbooks, adherence to KPIs, and progression through levels of response maturity. By following these best practices, organizations can effectively detect, contain, and remediate identity-related incidents, reducing the overall risk to their security. A comprehensive and efficient response strategy contributes to a robust identity security program and strengthens the organization's defenses against evolving threats.
Oort recently published a guide with 11 key criteria for mastering identity security including best practices for responding to threats quickly and effectively. Download the full guide and contact us if you have any questions.
Oort’s Identity Security Platform
Oort is an identity-centric enterprise security platform. As a turnkey solution for Identity Threat Detection and Response (ITDR), Oort is providing immediate value to security teams by working with existing sources of identity to enable comprehensive identity attack surface management in minutes. Led by a team with decades of domain expertise across identity, networking, and security, Oort is backed by venture capital investors including Energy Impact Partners, .406 Ventures, Bain Capital Ventures, Cisco Investments and others. Market-leading technology companies, like Collibra and Avid Technology, rely on Oort to provide full visibility into their identity populations.
To get a free identity security health assessment, request a demo.



