Summary
New insights, more context, and new remediation options. Brighten up your Monday morning by reading about Oort’s new capabilities.
I’m passionate about the “response” piece of Identity Threat Detection (ITDR), so we’ve been busy adding new action items.
Curious? Read on to learn more.
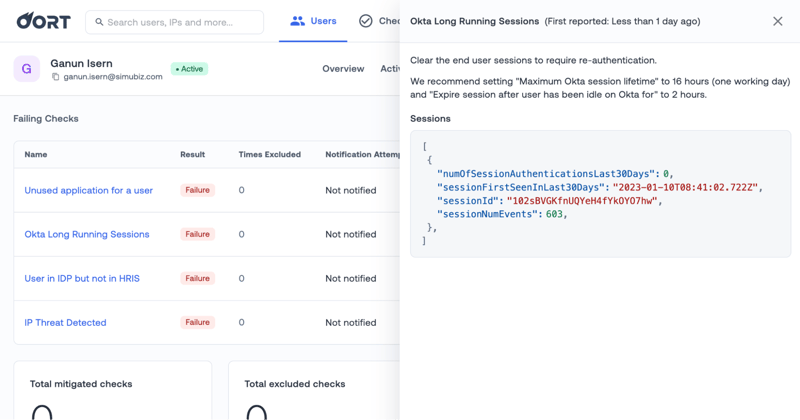
⏳ New Check - Okta Long Running Sessions
Oort already identifies if you do not have a maximum session lifetime in Okta, or if it seems unusually high. Long sessions without re-authentication pose a security threat by increasing the chance of session hijacking.
In this release, we have a new check “Okta Long Running Sessions” that will identify extremely long sessions. By default, this will look for a session 7 days long or more, but this threshold is configurable in Check Settings.
With this insight, you will be able to easily identify users with excessively long sessions and view information like the session ID, number of session authentications, and number of events in the session.
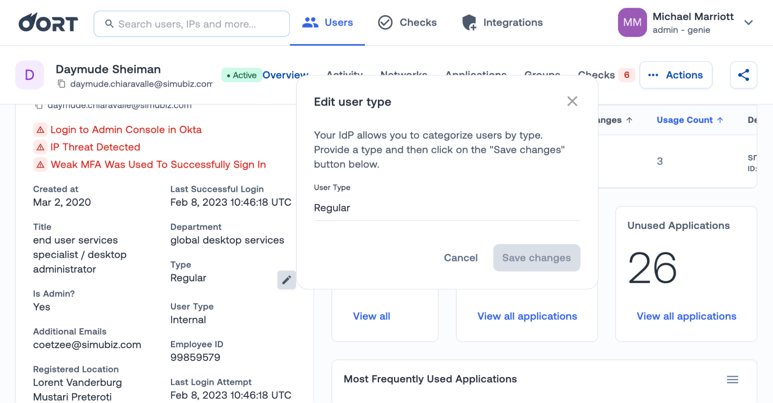
✍️ New Action - Edit User Type
Security teams are increasingly looking for new ways to reduce their identity attack surface. It’s one thing to detect identity threats, but reducing attacker opportunity creates actual risk reduction.
Unfortunately, IAM hygiene can be one of the most overlooked aspects of identity security. One of the common problems we find is missing user types. Your IDP will allow you to categorize users by type, which helps to keep track of different user types. Unfortunately, this field type is often missing for guest or API users.
Now, you can directly make changes from Oort itself! Within the User 360 profile, you will see an “Assign” icon if the type is missing or an edit icon if the user type exists. Either way, we’ve got you covered.

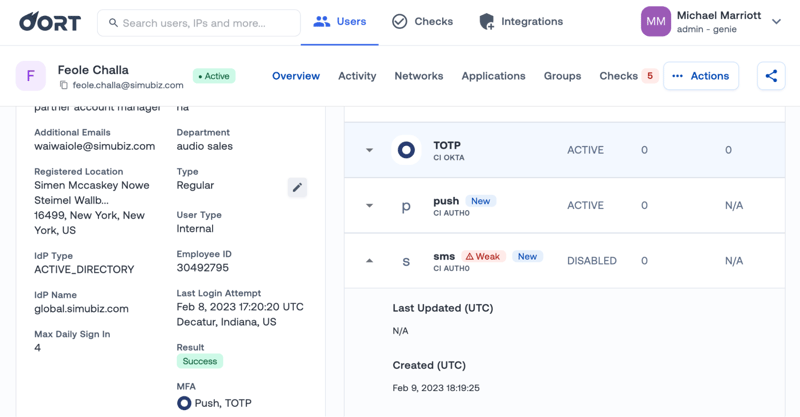
📳 New Authentication Factors
Did I mention how much customers loved the User 360 profiles?! These profiles put all the information you need in one place – including information on authentication factors. You can quickly see which factors a user has enabled, any changes to those factors, when they were created, and when they were last used.
We’re pleased to announce that Auth0 factors will now be displayed on this page.
📕 Enhanced Explainability for Unmanaged Device Access
Organizations are turning to device trust to harden their identity attack surface. Oort already identifies users who are still logging in from unmanaged devices, making it possible to identify and deprecate unmanaged device access when the organization is fully ready.
To make this as easy as possible, we have included increased context to help explain what happened. This includes extensive information about the device, including the device name, and device ID.
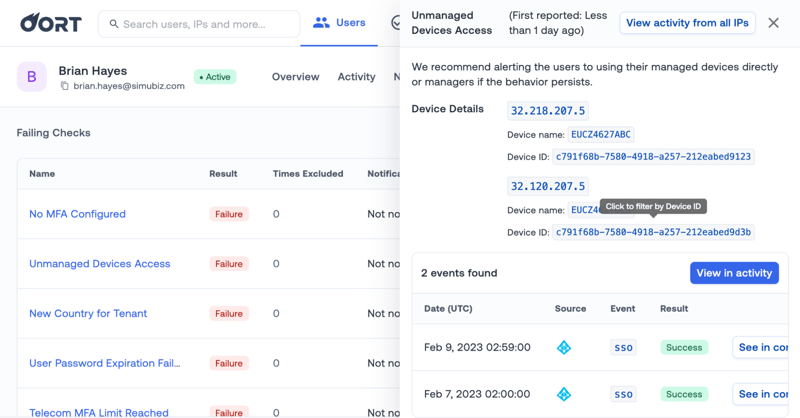
You’ll see the similar (but different) additional context for other checks like ‘New Country for Tenant’ and ‘Active Account under Heavy Attack’.
Bug Fixes and Minor Improvements
- IP Threat. Improved accuracy by filtering known ASNs and common IP addresses
- Slack Pop Up. Message edits for accuracy
- Login geoinformation
- Status Banner. You will now see a remediation status banner and user refresh status banner on the user profile pages.


