It’s been a busy week in the world of identity with some sobering developments impacting organizations using Okta. The so-called “0ktapus” campaign is out there stealing credentials and weak one-time passcodes to virtually walk right in the front door of some pretty big companies.

As you probably know by now, this type of attack is one of the main reasons Oort exists. Detecting weak forms of MFA (such as SMS) and high-fidelity alerting on behavioral anomalies are just some of what we do better than anyone. With reports of over 10,000 submissions of valid credentials during the attack, it’s possible that more is yet to come. So, if you’re worried about these types of attacks, or if you just want to get a free assessment of your identity security posture, let’s start you with a demo of Oort.
Now is also a good time to subscribe to our release notes so you don’t miss any new features, integrations or Identity Security Checks.
New Features
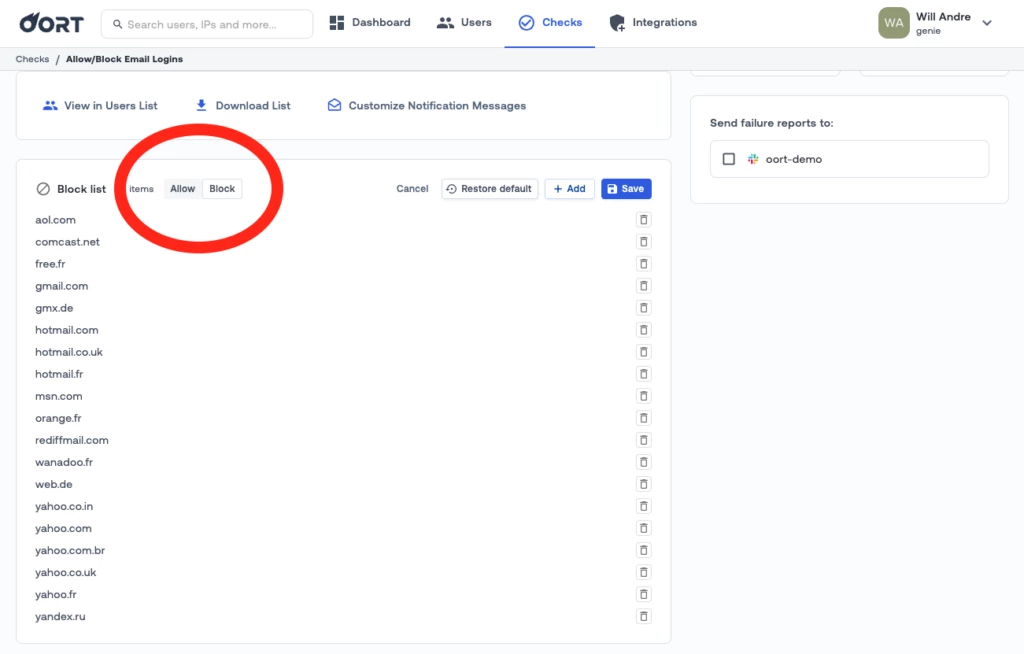
Allow & Block Lists Now Bi-Directional
You can now toggle your lists to ‘Allow’ or ‘Block’ certain email domains or browser types. Setting these lists will help security analysts quickly identify authentication behavior that is out of policy for your organization by failing its respective checks when any of the criteria are met.
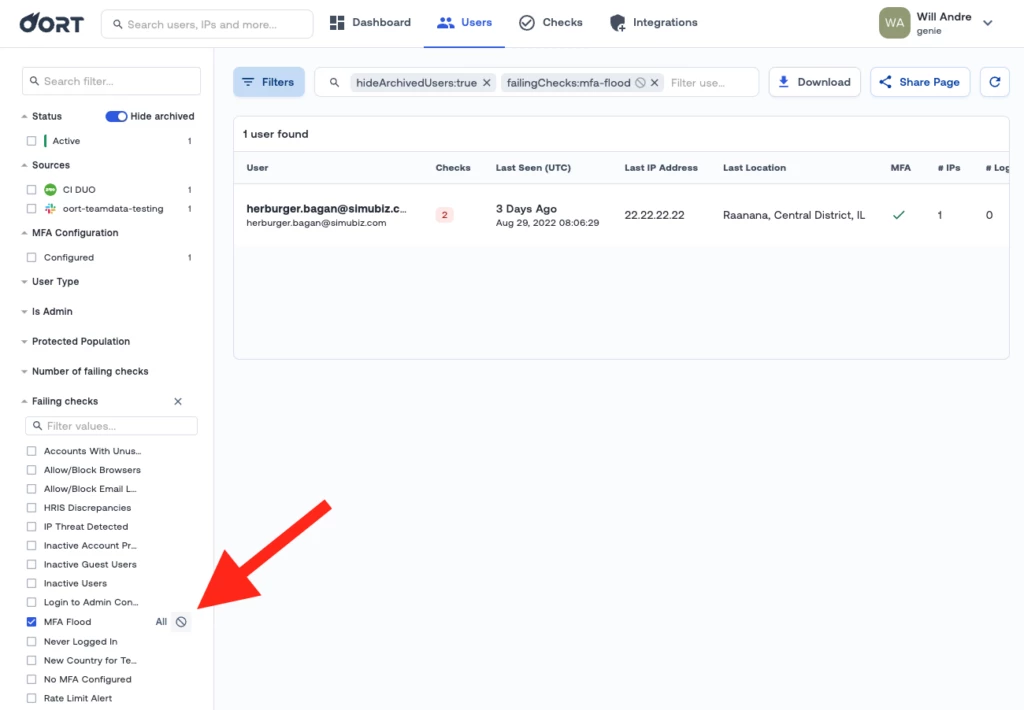
Filter Panel Now Actionable
You can now take action to include or exclude filters from the side panel when viewing the Users list. This enables specific populations of users to be shown in the results without having to enter a query in the search bar.
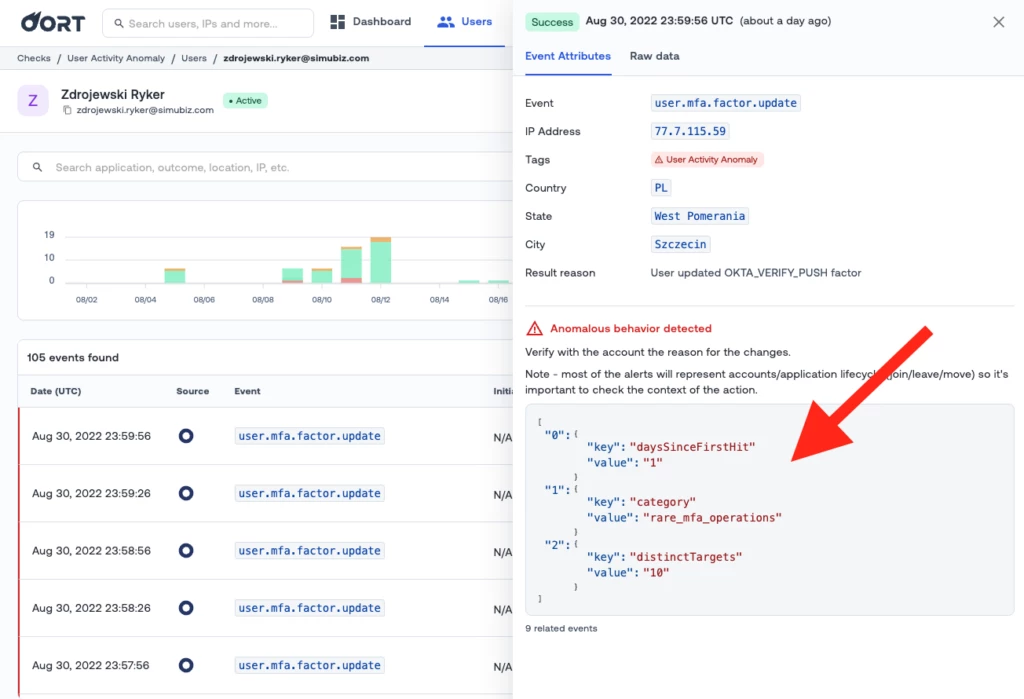
Behavioral Check Failures Now Explained
You can now see the reason why a behavioral check failed. Navigate to any user, click the ‘Activity’ tab, then click the event in the table. The sidebar will open up with details of what behavior triggered the check failure.
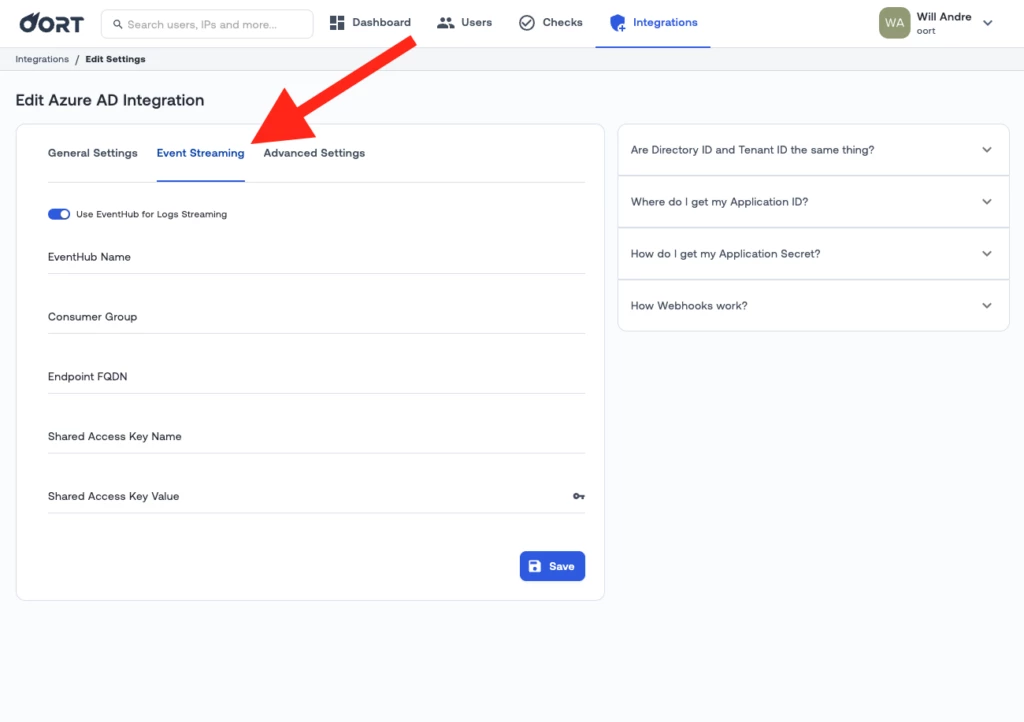
▶️ EventHub Integration Now Available for Azure AD
You can now configure your Azure AD instance to utilize the EventHub streaming service. Using EventHub reduces the likelihood that your organization will hit any sort of rate limit when collecting logs. To enable EventHub, go to the “Integrations” tab, select your Azure AD instance, then click the “Event Streaming” tab. Enter your information and click Save.
Improvements
👌🏻Customers using OIE can now enable collections for “Devices” and “Authenticators”
👌🏻 The Identity Security Check for “Risky Parallel Sessions” has been optimized to remove obvious machine communications
That’s a wrap for this week! Make sure you subscribe to our updates up top so you don’t miss any new features or announcements coming from Oort! Can’t wait? Get a demo today!



