Phew! We just got back from the Gartner IAM Summit in Las Vegas. It was great to connect with current customers, demo Oort to new partners, and learn all about the trends that are shaping the future of identity and access management.

If you were there, too, then you heard the message from Gartner loud and clear: ITDR is the next big thing, and with players like Microsoft presenting at this summit on the topic, you can be sure they’re right on the money.
If you weren’t able to make it to the summit, don’t worry, you can get an Oort demo any time. Just click below to find a time that works for you – we only need 15 minutes!
Okay, that’s a lot of excitement in and of itself, but let’s jump in to what our amazing engineering team managed to cook even while we were out singing the praises of ITDR.
New Features
🪪 New Workday User Tiles
Fresh off of this month’s huge announcement about Workday integration, we’ve now added user information tiles to identity sources on all User 360 pages. This give you the user’s Workday profile right on the screen so you can easily visualize and compare it to IDP sources for any inconsistencies.

🔎Search by Session ID
You can now search by session ID in the user activity tab in User 360 to return all of the events associated with that session ID. This helps contextualize a user’s events in Okta and allows deeper investigation of risky parallel sessions, for example, to see if concurrent sessions might have behaved differently.
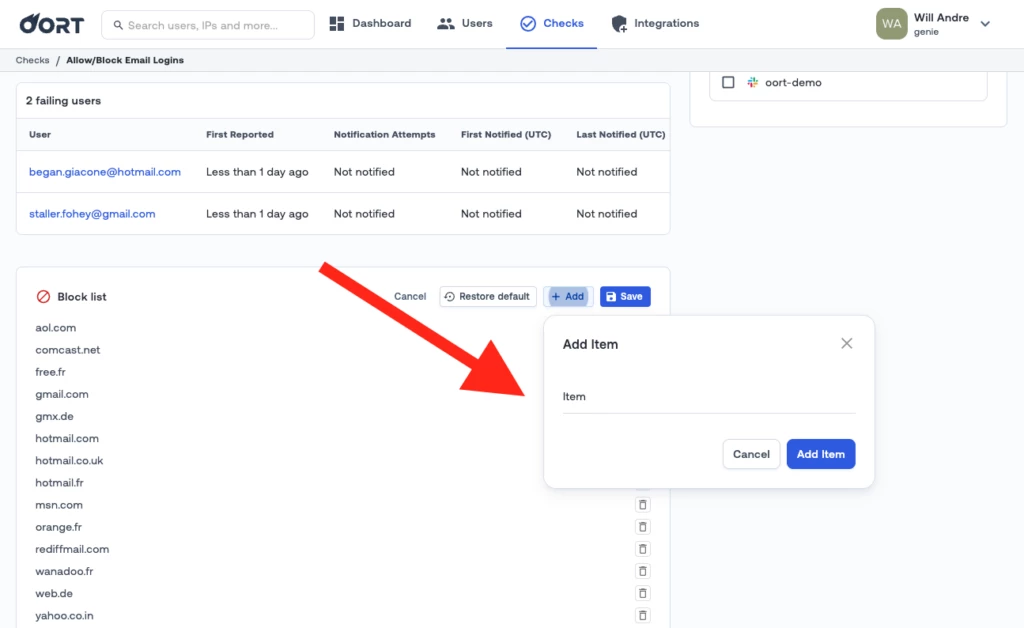
⛔️Editable Block & Watch Lists
You can now edit the lists of browsers, email domains, and IP addresses that you want to be included in or excluded from your check failures and notifications. This feature helps organizations to set certain policies such as alerting on authentications from known risky browser types. With regard to the check for known risky IP addresses, you can select which category of threat types you want to ignore when calculating and alerting on check failure.
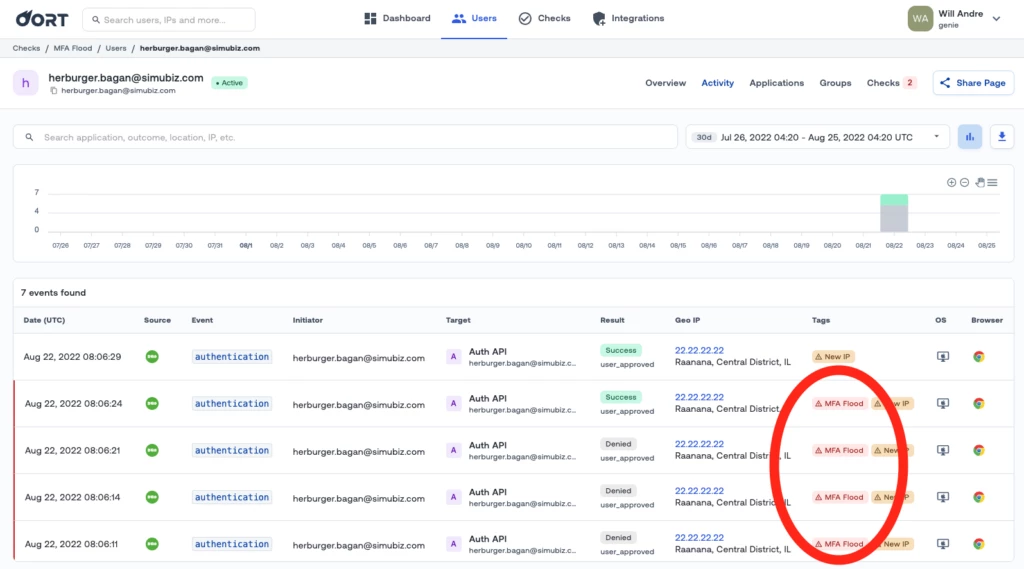
🏷Failed Checks In Activity Table
You can now see why checks failed inside the user activity table for checks that support it. This enables security analysts to quickly discern whether an event resulted in a check failure, and it eliminates the time wasted on context correlations.
Fixes
- 👌🏻Full URLs can now be used in the search bar to return users associated with that domain.
- 👌🏻User lists with checks filters applied now only return users within the protected population.
New Identity Security Checks
✅ New Access from a Previously Only Failing IP
This check allows you to receive alerts when an account succeeds in logging in from an IP address that has only seen failures in the past 90 days. This is a useful notification as it can identify successful brute force or password spraying attacks against your organization.
That’s a wrap for this week! Make sure you subscribe to our updates up top so you don’t miss any new features or announcements coming from Oort! Can’t wait? Get a demo today!



