Summary
While many of us have spent the last few weeks plowing through chocolate and knocking back eggnog, the untiring Oort engineering team has been busy adding new features and functionality for you to feast on in the new year.
Be prepared: we have a lot of new and exciting product features planned for this year, which we'll be shipping out early and often in the weeks and months ahead
We’re incredibly excited to be kicking off a year that promises so much. Thank you for joining us on this journey!
🌐 IPInfo Bolsters Threat Intelligence in Oort
We’ve been speaking for a while about the importance of good IP context. When security teams see a new IP address attempting to log in, there’s a lot of context that can make this easier to triage. This includes:
1. The corresponding geolocation
2. Whether the IP address is associated with a consumer VPN (like NordVPN) or a cloud proxy service (like Zscaler).
3. Which ISP/company/cloud provider owns the IP address. (For example, is it normal to be checking your email from an EC2 instance hosted on AWS?)
This kind of context is critical for filtering out noise and assessing if the observed behavior is normal.
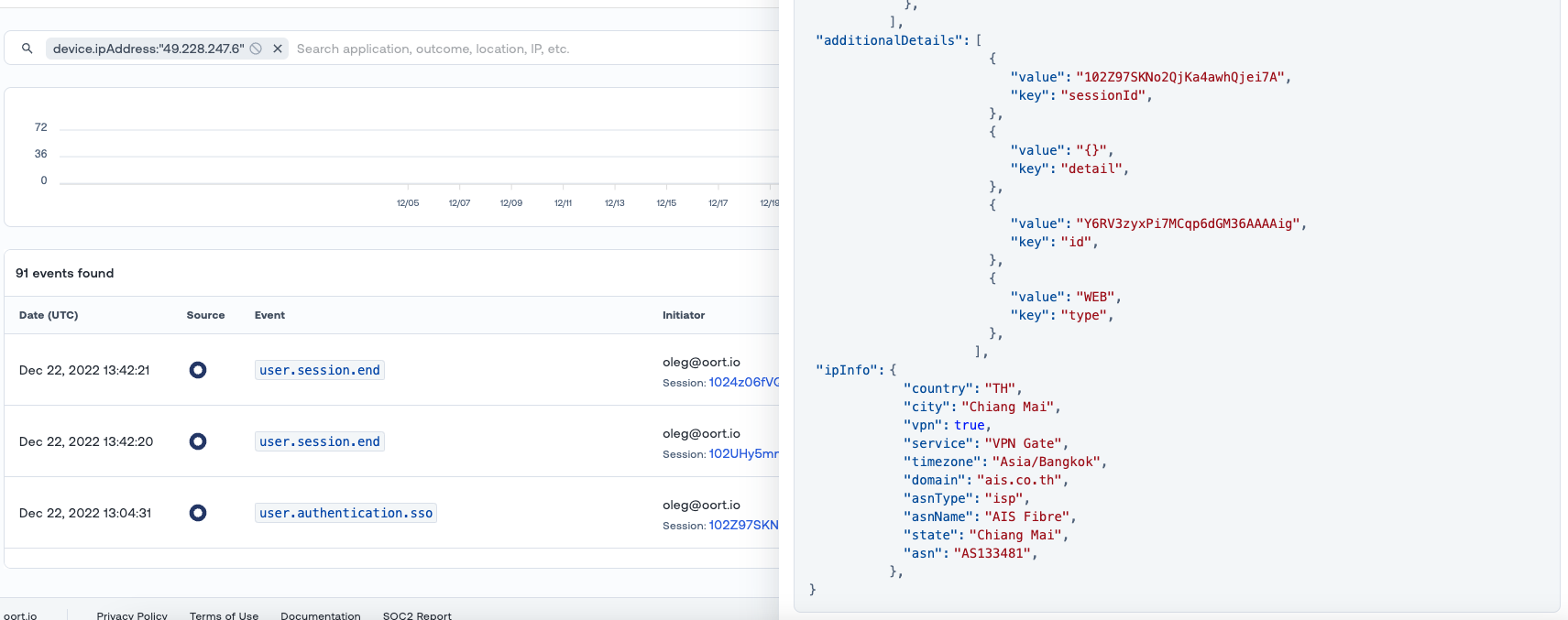
This recently culminated in the release of the new Networks Tab. We’ve now made this even richer with context from IPInfo, an (excellent) IP enrichment service. You can now track IPs belonging to services like hosting, VPNs, tor nodes, proxies or relays. That information can help identify unconventional behavior.
Furthermore, ASN information (ISP, location and more) is available on the event raw data (which we make available to you).

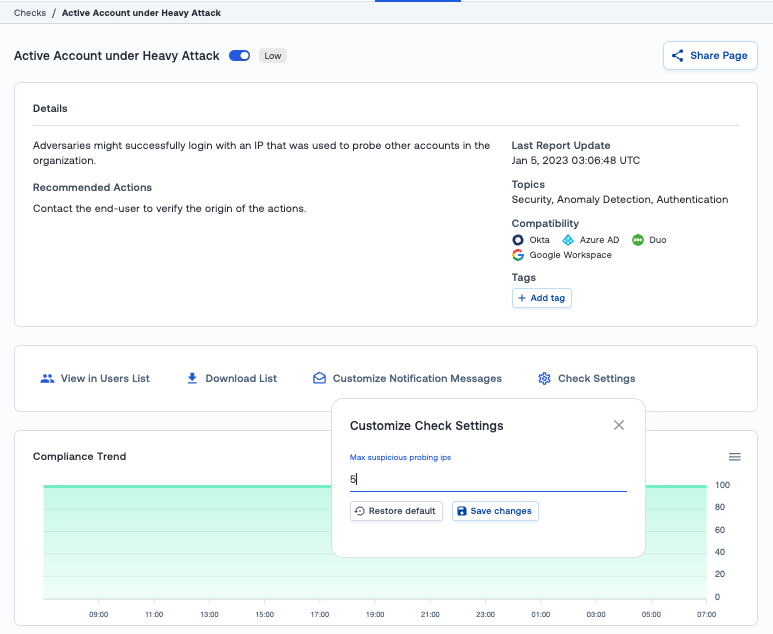
🔔 New Check Available: Active Account Under Heavy Attack
Having greater context on suspicious IP addresses makes it possible to detect additional threats. Every day we see suspicious IP addresses trying to log into accounts. Often they will target publicly-known email addresses, such as those found on company websites.
More often than not these attempts fail – especially if those accounts are protected by multi-factor authentication. Unfortunately, MFA weaknesses and bypass techniques show that MFA is not infallible. Therefore, Oort’s ability to detect sudden spikes in failed login attempts is highly valued by security teams.
With this new check, you can get insight when an active account is being probed by an IP address that has already attempted sign-ins against other accounts. By default, Oort alerts when an IP has probed 5 or more times but this threshold is configurable.
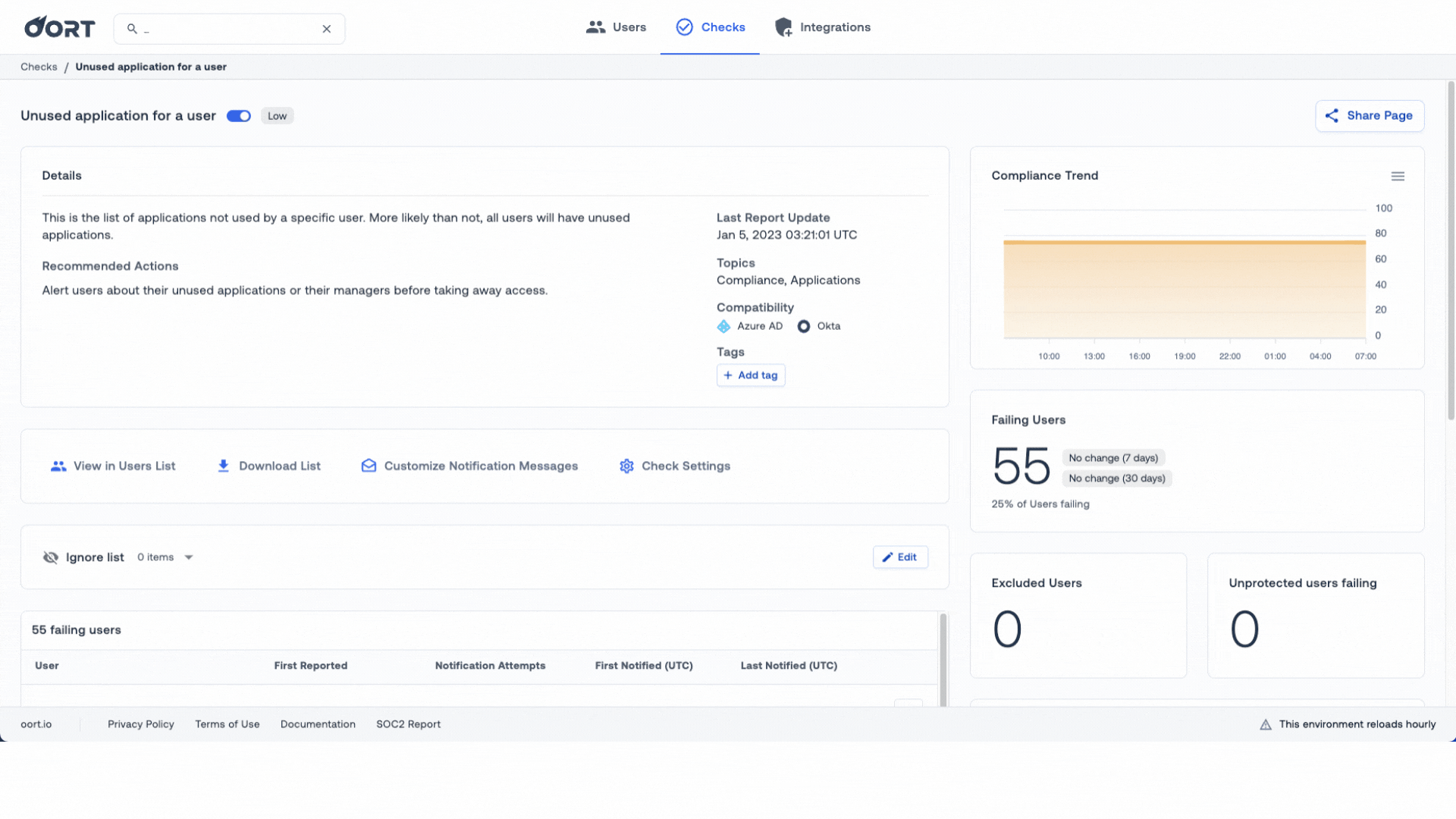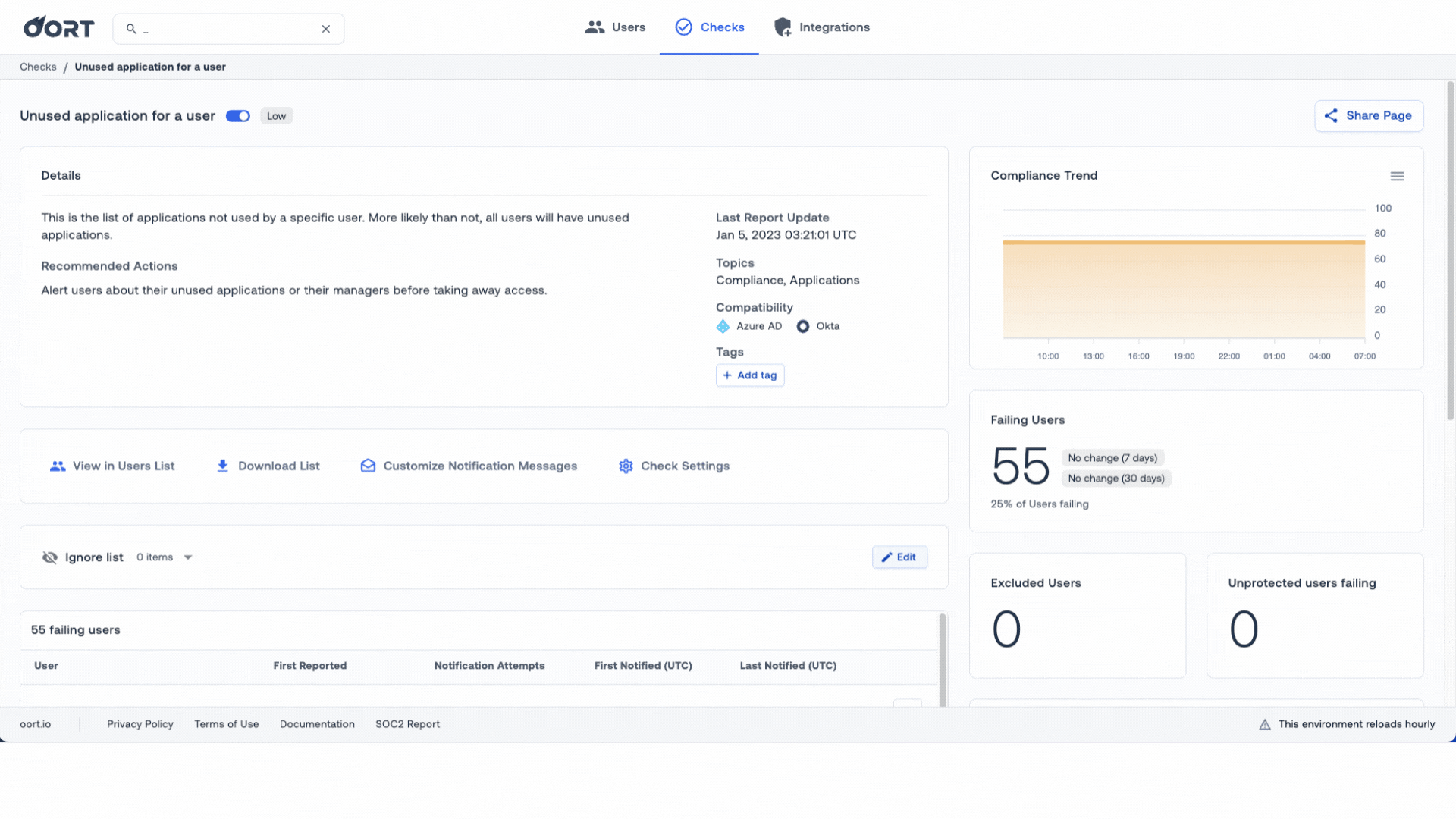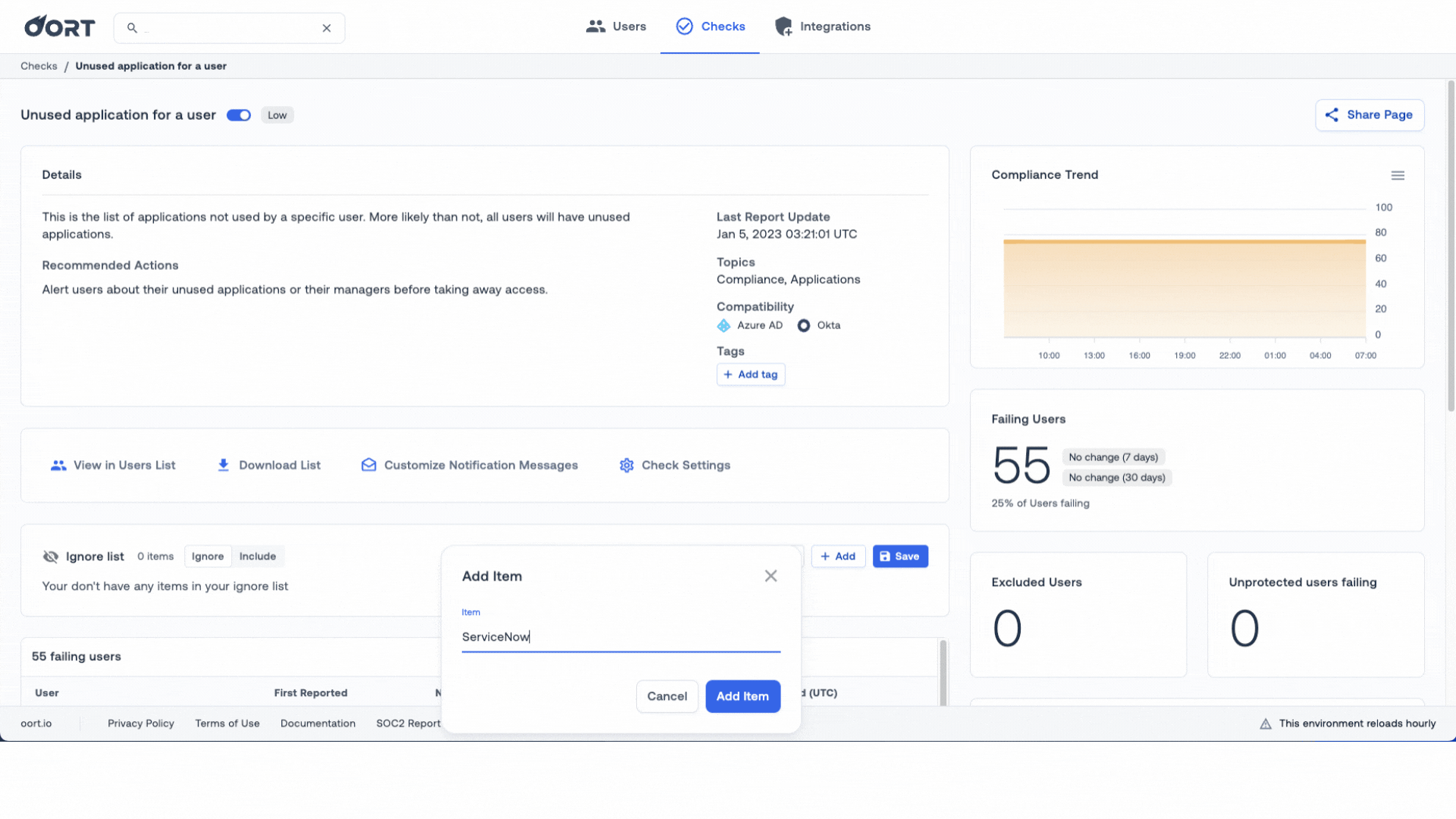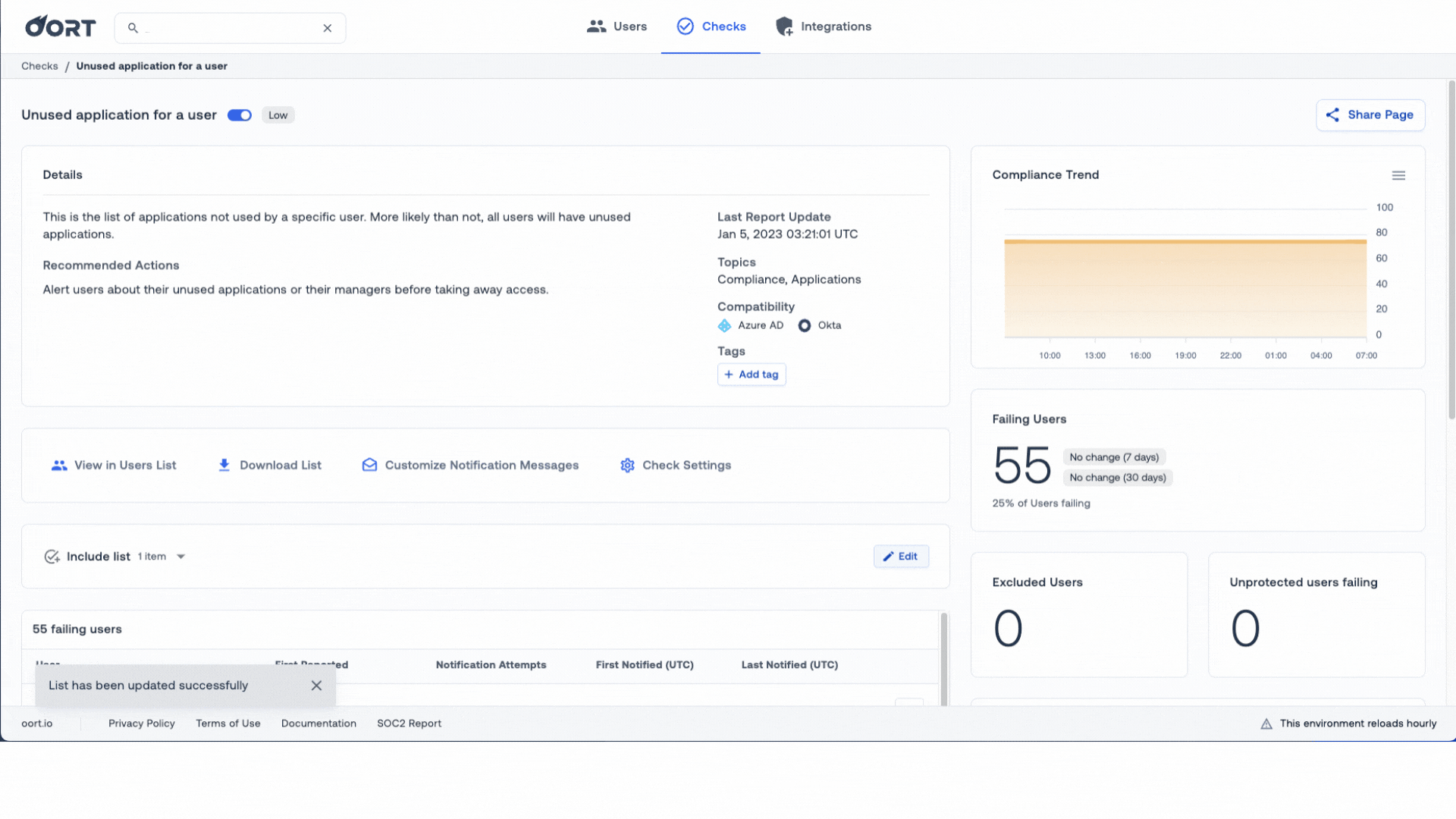
🖥️ Customize Insights on Unused Applications
Just before the holidays, we wrote about Oort’s ability to detect unused applications. Unused licenses have obvious financial implications, but having users with excessive access also constitutes a potential security risk.
In this release, you can now add greater customization to these insights:
1. Customize Check Settings. Choose to only be alerted on sensitive apps, define the app usage time frame, and ignore bookmark apps.
2. Ignore and Include Lists. Choose to add Apps to an ignore list OR choose to only focus on specific apps by using the “Include” list toggle. By doing so, you can focus on the applications that cost the most!
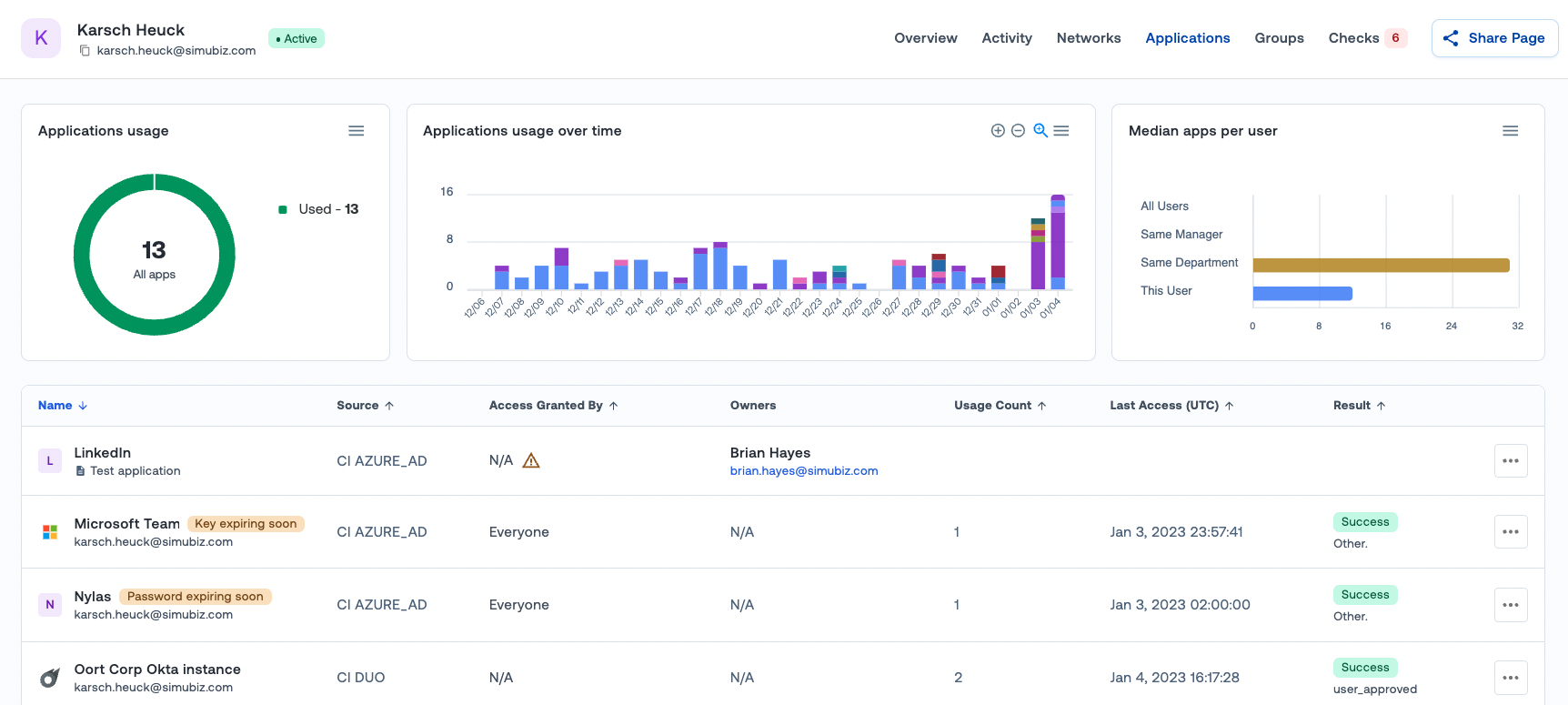
To make life even easier, we’re also providing more information on the applications in question, as well as displaying the owners of that app. This will make it really easy to follow-up with the correct person and verify if the user still needs access.
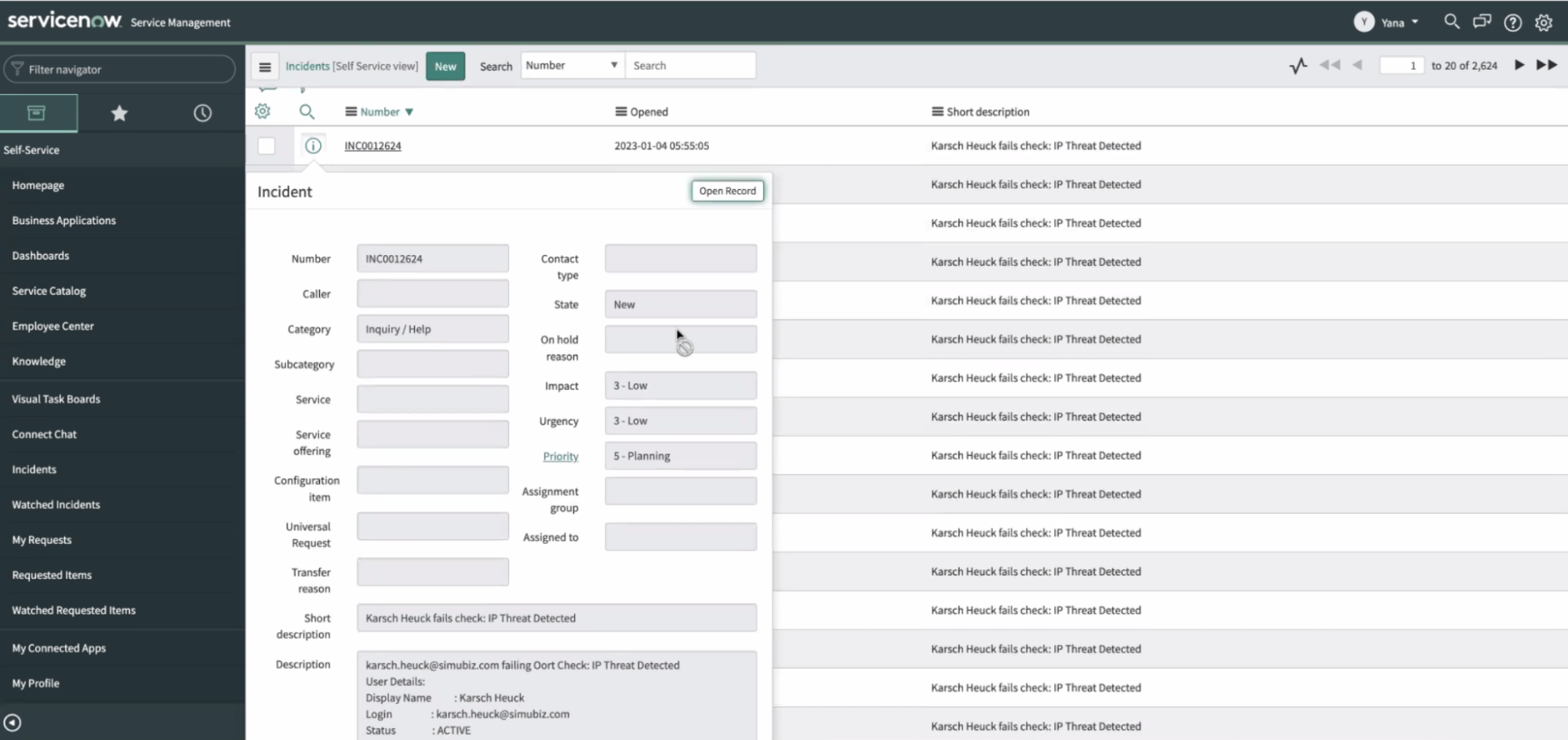
🔗 Greater Context in ServiceNow and Jira
We’ve said it before, but I’ll say it again: it’s critical that you can get Oort’s insights into your existing security workflows and avoid signing into thousands of different platforms. In this release, we’ve beefed up the information that you receive in ServiceNow and Jira. This means that you save time investigating, as you don’t need to go back into the Oort platform for further context.
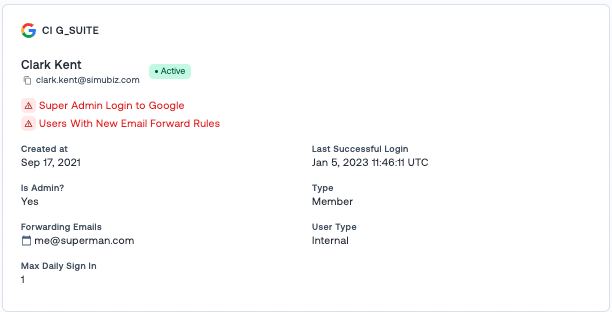
🗂️ User Profile Provider Card
Within every user profile, Oort provides “provider cards”. These cards provide a summary of that user from every identity provider we’ve integrated. This will often involve multiple sources, such as Okta, Azure AD, Workday, and GSuite.
These provider cards now show additional details:
1. Forwarding emails used (read more about that issue in a previous blog).
2. All failed checks displayed relevant to the identity provider.
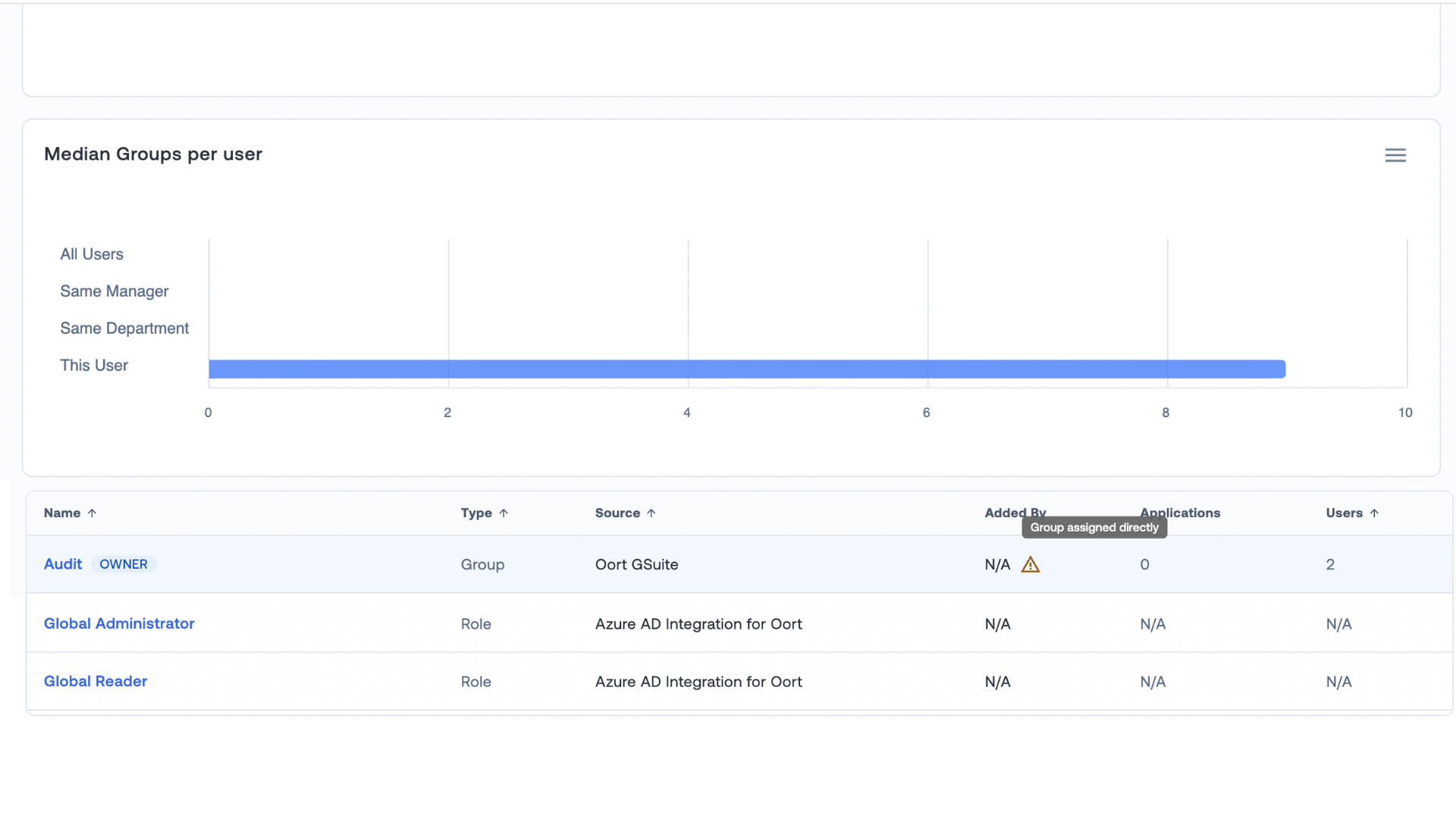
🧑🤝🧑 Group and Role Assignments
As we’ve already seen, most security teams are concerned when users have unnecessary access. Often, roles and permissions are granted through group memberships, and so gaining insight into what group gave them the role, and if a user is the owner of a given group is especially helpful. For example, we’ll display a warning if the owner assigned the role directly.
Furthermore, the Groups tab will also now show information specific to Azure AD role assignments. Roles are usually assigned to admins like an App Admin and can be assigned either directly or via a group membership.
Bug Fixes and Minor Improvements
- Full country name. Oort now shows the full country name in New Country for Tenant Check, which formerly only showed the alpha-2 country code.
- Open user in a new tab, saves you time by enabling you to open multiple users in multiple tabs without the need to navigate back and forth.
- Improved sorting for Checks list. You can now view the most relevant checks first, which now incorporates the number of failing users and other factors.
- Tenant Access Log provides colored chips to easily distinguish roles.


